


|
||
|
||
Group-IB uncovered ResumeLooters, a threat actor group specializing in victimizing job hunters to steal their personally identifiable information (PII). Along with their in-depth threat analysis, they identified 15 indicators of compromise (IoCs), specifically seven domain names, three subdomains, and five IP addresses.
The WhoisXML API research team used the 15 IoCs as jump-off points for an expansion analysis in a bid to find more potential ResumeLooters attack vectors that led to the discovery of:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
We began our investigation by taking a closer look at the 15 IoCs starting with the seven domain names.
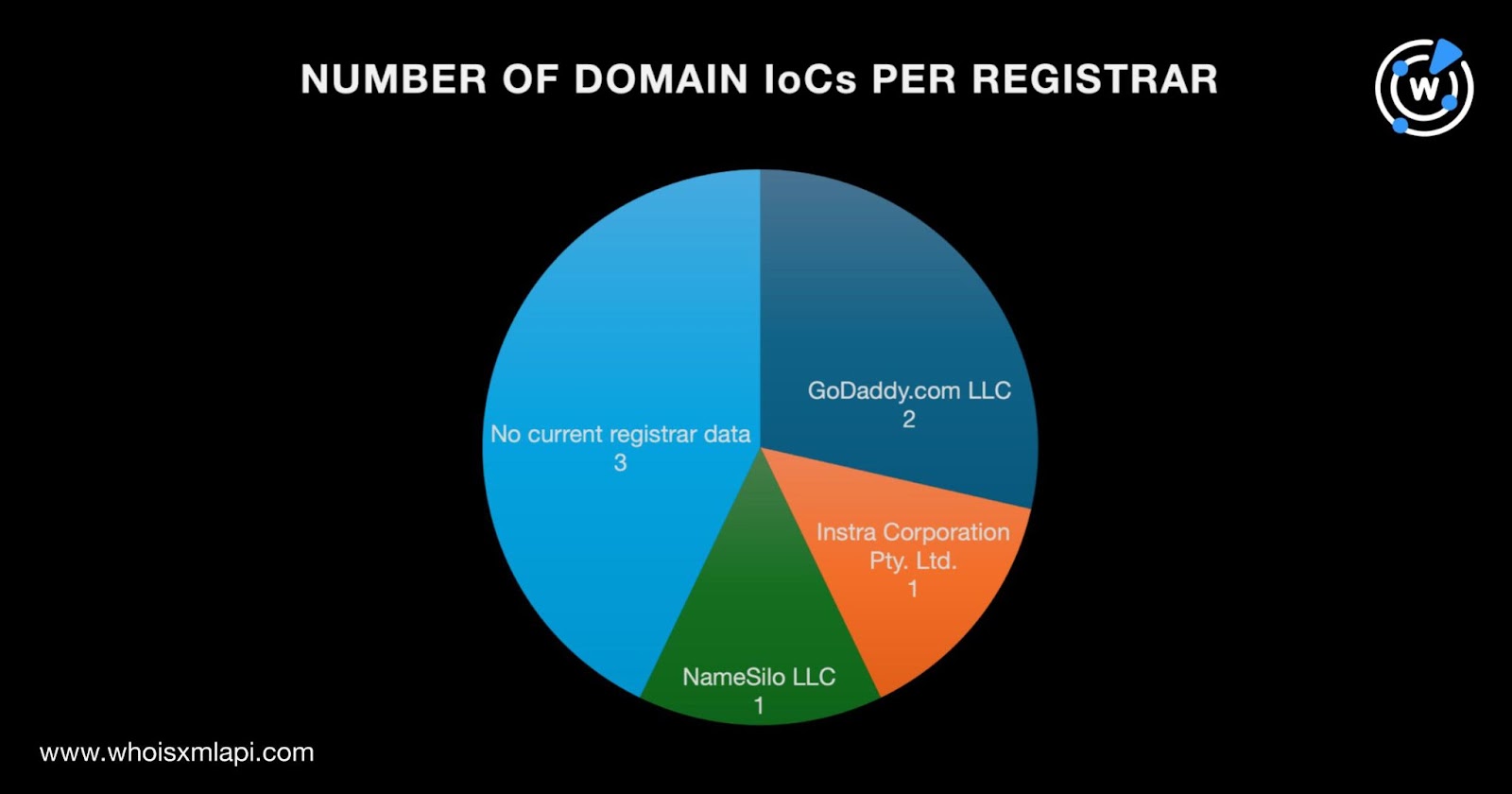
A bulk WHOIS lookup for the seven domains identified as IoCs led to these findings:
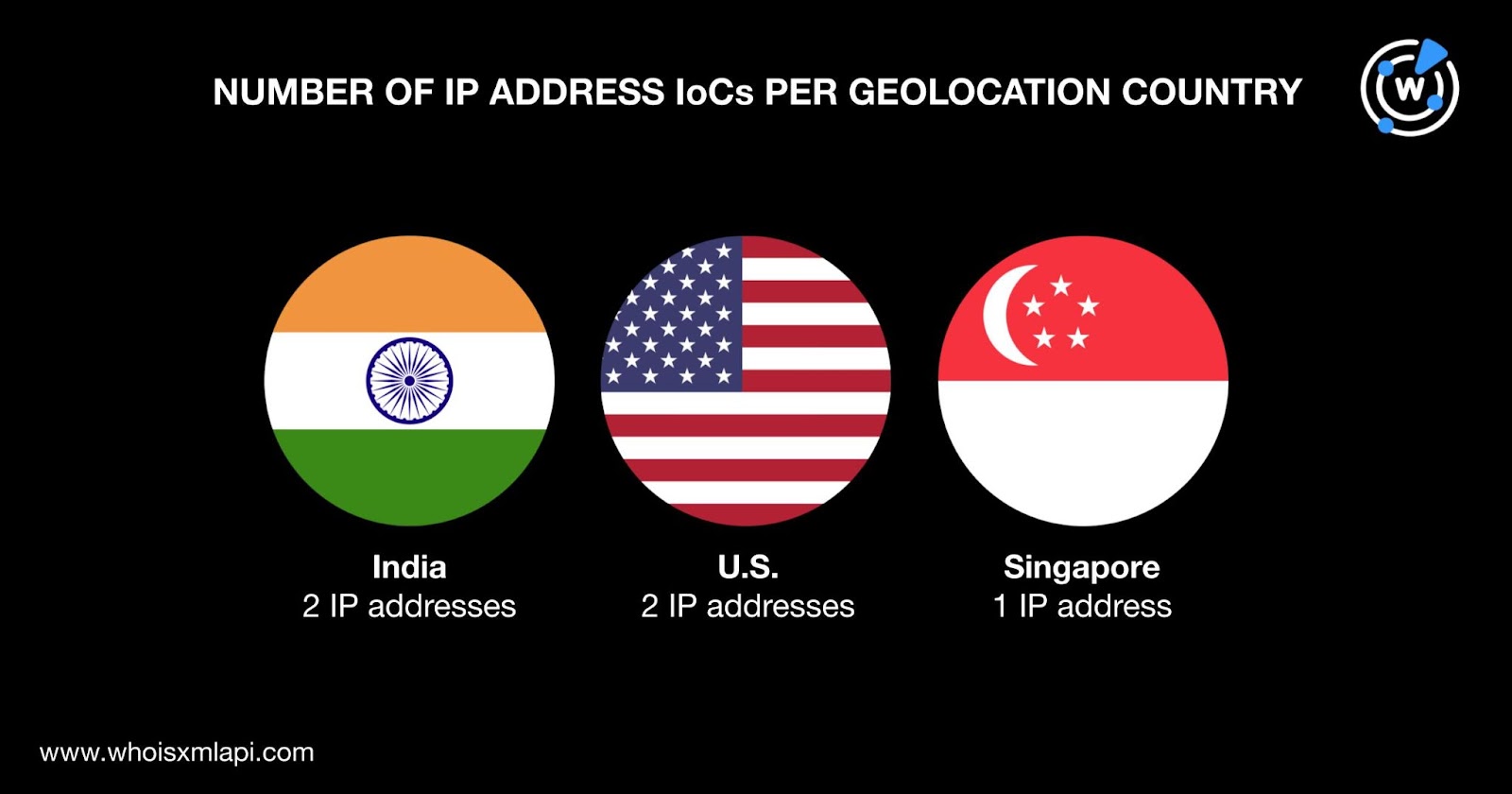
The bulk IP geolocation lookup for the five IP addresses named as IoCs gave these results:
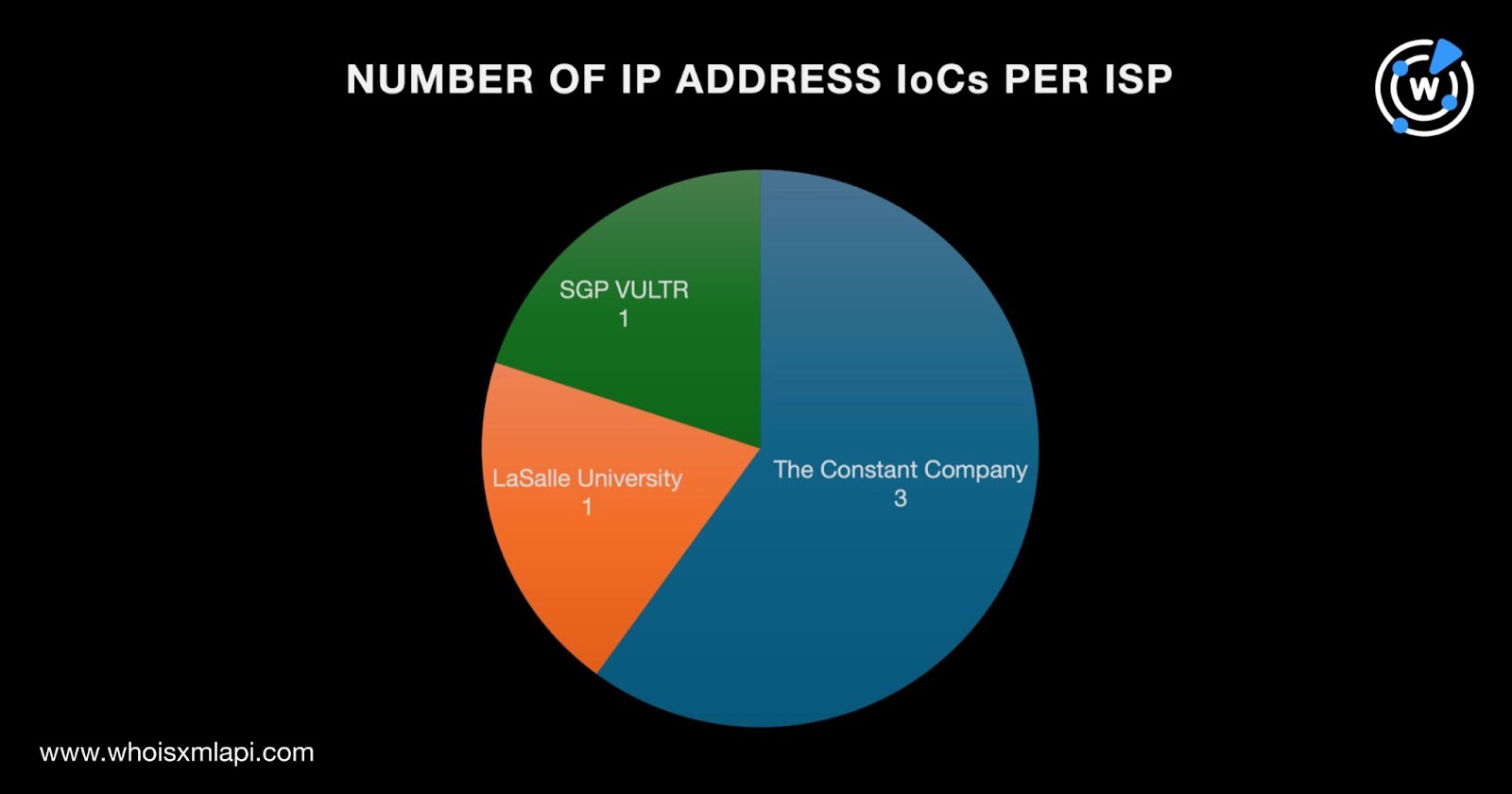
They were spread out across three ISPs led by The Constant Company, which accounted for three IP addresses. One IP address each was administered by LaSalle University and SGP VULTR.
This section describes how we went about finding artifacts potentially connected to ResumeLooters.
Our bulk WHOIS lookup earlier revealed the registrant name and organization of domain IoC 8t[.]ae. A reverse WHOIS search using the registrant name as input provided us with 302 connected domains after duplicates and the IoCs were filtered out, 77 of which remained accessible at the time of writing according to Screenshot API results.
WHOIS History API also allowed us to obtain four email addresses from the historical WHOIS records of the seven domain IoCs after duplicates were removed. Two of them were public, which we then used as Reverse WHOIS API search inputs. They gave us 69 email-connected domains after filtering out duplicates, the IoCs, and the registrant-connected domains. Twenty-seven continued to host live pages to date.
Next, we performed DNS lookups for the seven domain IoCs and found that they resolved to six additional IP addresses after removing duplicates and the IoCs. Like two of the IP address IoCs, all of them were geolocated in the U.S. and administered by Cloudflare, Inc. All six additional IP addresses were also associated with various threats. Specifically:
We then subjected the 11 IP addresses in total (i.e., five IoCs and six additional hosts) to reverse IP lookups and found that three of them could be dedicated. They enabled us to uncover three IP-connected domains after duplicates, the IoCs, and the registrant- and email-connected domains were filtered out.
To complete our investigation, we used Domains & Subdomains Discovery to look for domains that started with text strings found among the seven domain IoCs. Our searches enabled us to gather 573 string-connected domains, two of which—8t[.]pm and 8t[.]wf—were associated with malware attacks according to Threat Intelligence API.
Group-IB, in their report, also identified three ResumeLooters subdomain IoCs. Two of them—recruit[.]iimjobs[.]asia and recruiter[.]foundit[.]asia—seemed to be impersonating legitimate job-hunting websites.
Google searches for the two sites revealed that the legitimate job-hunting websites’ domain names were iimjobs[.]com and foundit[.]in. They both had public registrant organization data in their current WHOIS records according to WHOIS lookups. The same searches for iimjobs[.]asia and foundit[.]asia, meanwhile, did not turn up registrant organization information for both likely typosquatting domains. Screenshot lookups for iimjobs[.]asia and foundit[.]asia also showed both were unreachable as of this writing.
If ResumeLooters specially crafted the domains iimjobs[.]asia and foundit[.]asia for their campaign, could they or other cybercriminals have done the same thing? We trooped to Domains & Subdomains Discovery to find out.
Our closer looks uncovered eight iimjobs.- and 166 foundit.-containing domains.
While none of the iimjobs.-containing domains were associated with any threat, only three of them could be publicly attributed to iimjobs[.]com’s registrant organization.
Like the iimjobs.-containing domains, none of the foundit.-containing domains were classified as malicious. But WHOIS record comparisons showed that only one of them could be publicly attributed to foundit[.]in’s registrant organization.
Our analysis of ResumeLooters led to the discovery of 953 potentially connected web properties, specifically 302 registrant-connected domains, 69 email-connected domains, six additional IP addresses, three IP-connected domains, and 573 string-connected domains. Eight of the related digital properties were associated with various threats, including phishing, malware attacks, generic threats, and suspicious activities.
Our analysis of two of the subdomains ResumeLooters used in their campaign also showed signs of possible job-hunting site impersonation targeting iimjobs[.]com and foundit[.]in.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byRadix

Sponsored byIPv4.Global

Sponsored byCSC

Sponsored byDNIB.com

Sponsored byVerisign

Sponsored byVerisign

Sponsored byWhoisXML API
