


|
||
|
||
macOS has been gaining the unwanted attention of more and more backdoor operators since late 2023.
In February 2024, Bitdefender uncovered RustDoor, which was written in Rust and possibly has ties to the operators of a Windows ransomware. They published their findings, including seven indicators of compromise (IoCs) comprising five domain names and two IP addresses. Back in November 2023, meanwhile, SentinelOne analyzed crypto theft attacks targeting macOS users aided by KandyKorn. Their report unveiled four IP addresses as IoCs.
The WhoisXML API research team sought to find out how many potentially related web properties there are for the two threats in the DNS and uncovered:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
As per usual, we kicked off our analysis by looking more closely at the seven RustDoor IoCs—five domain names and two IP addresses.
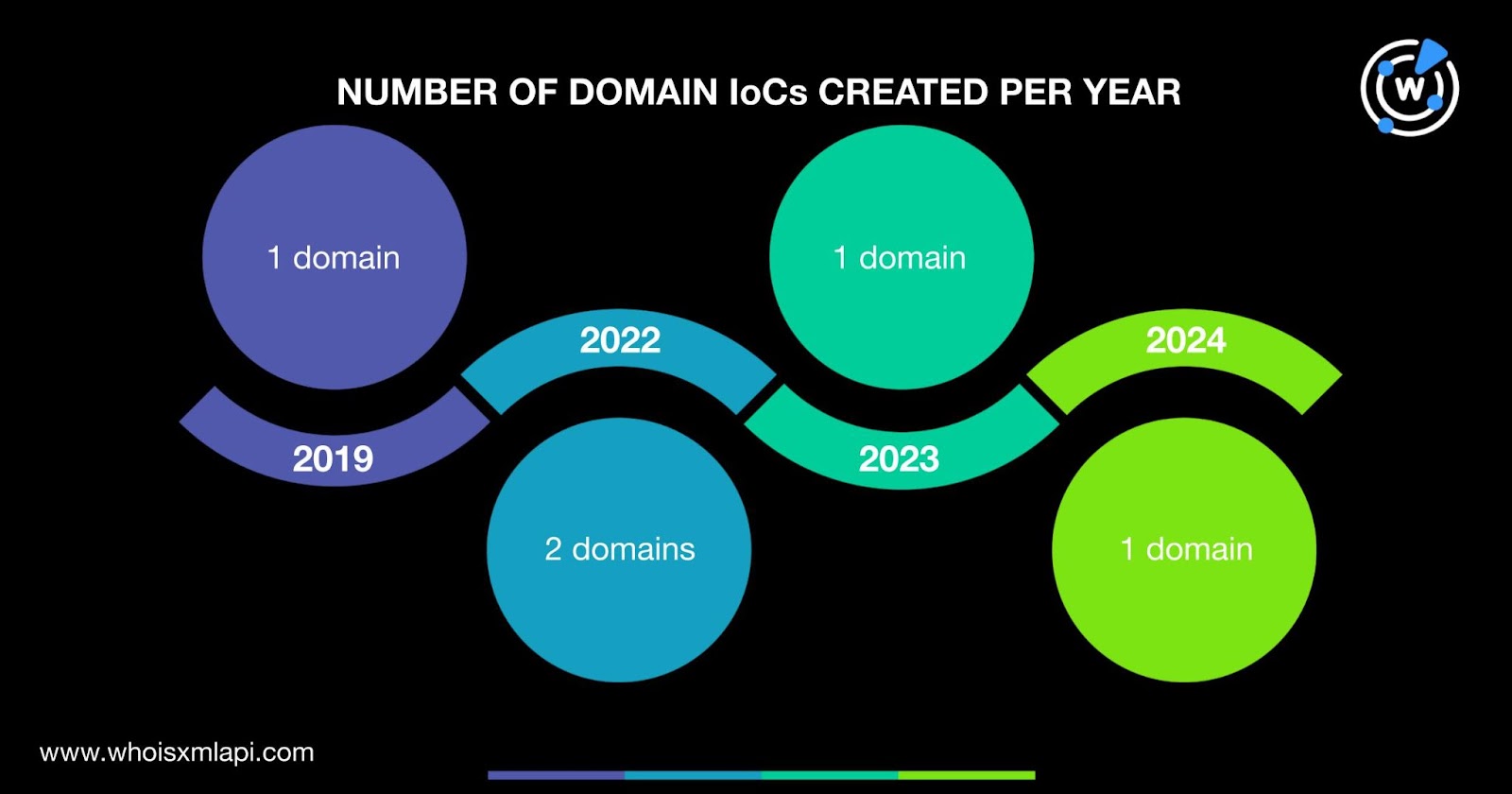
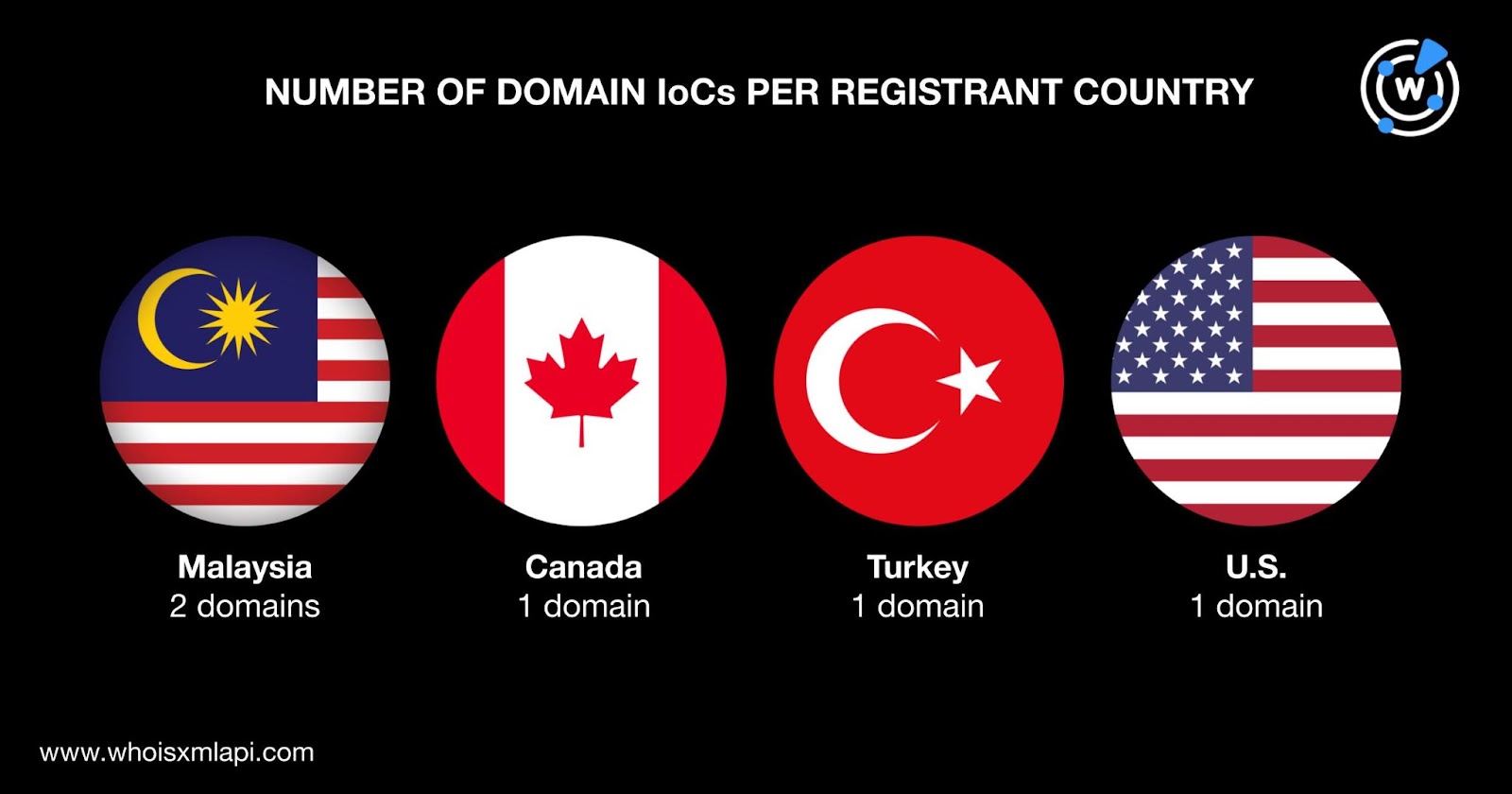
A bulk WHOIS lookup for the five domain names identified as IoCs found that:
They were created between 2019 and 2024. Specifically, two domain IoCs were created in 2022 and one each was created in 2019, 2023, and 2024.
They were registered in four different countries. Two domain IoCs were registered in Malaysia and one each was registered in Canada, Turkey, and the U.S.
IP geolocation lookups for the two IP addresses classified as IoCs revealed that:
Two of the domain IoCs contained macOS- and iCloud-related text strings—maconlineoffice[.]com and serviceicloud[.]com—that could indicate attempts to legitimize their campaign. The threat actors possibly hoped to trick users into downloading the backdoor by making them think they were installing Microsoft 365 for Mac, Office for Mac, or iCloud.
To find out if other RustDoor-connected artifacts were present in the DNS, we performed an expansion analysis beginning with WHOIS History API searches for the five domain names categorized as IoCs. That led to the discovery of 10 email addresses from their historical WHOIS records, one of which was public.
A current Reverse WHOIS API query for the public email address allowed us to collate five email-connected domains after duplicates and the IoCs were filtered out. Interestingly, judging by the domains (i.e., findmy-inc[.]us, findmy-lcloud[.]us, and findmyapp-location[.]us), a majority of them (three out of five domains) seemed to allude to connections to macOS’s Find My asset tracking service.
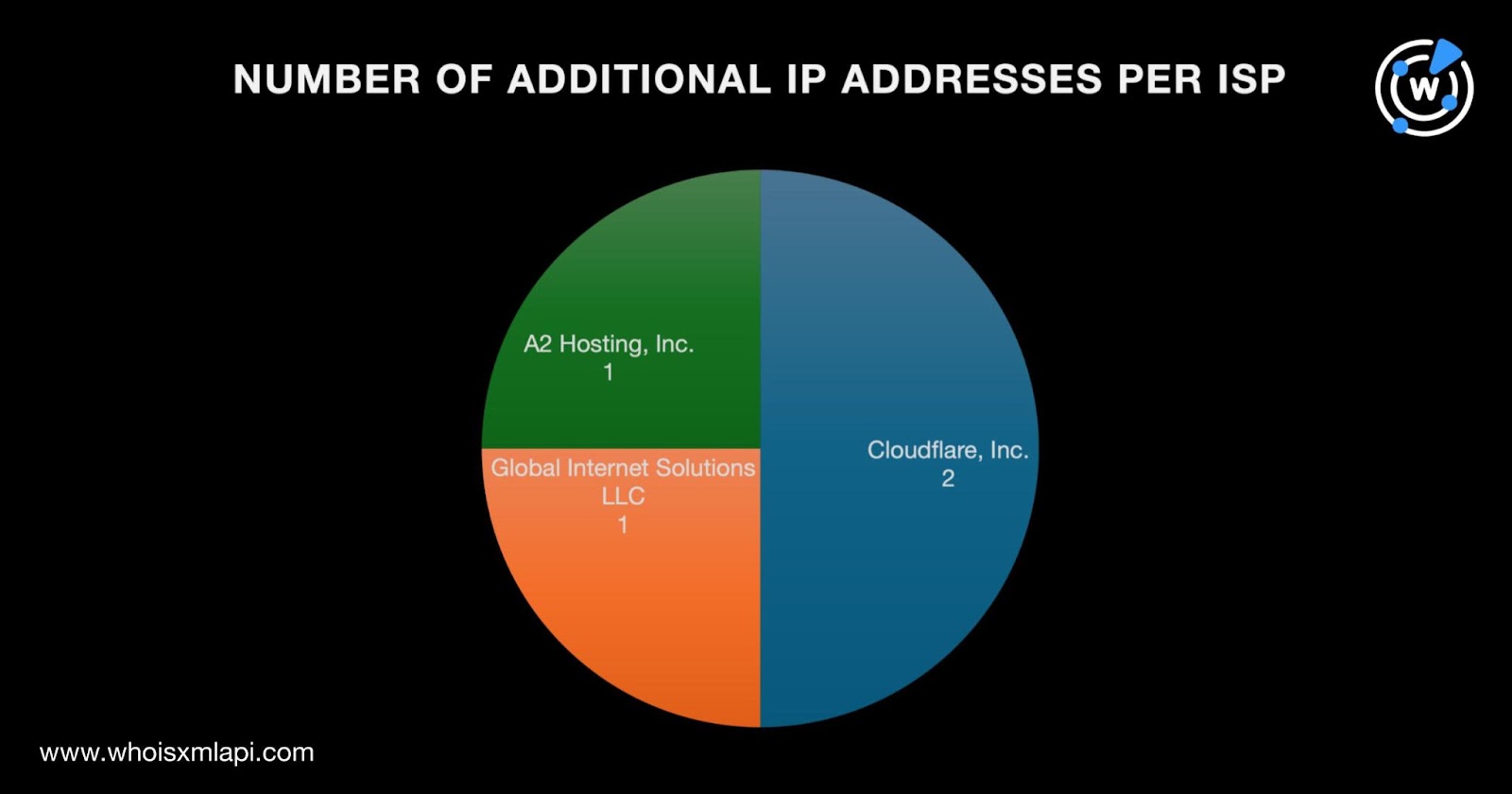
Next, we performed DNS lookups for the five domain IoCs that enabled us to uncover four additional IP addresses. IP Geolocation Lookup showed that:
Threat Intelligence Lookup revealed that one of the additional IP addresses—85[.]187[.]128[.]40—was associated with phishing.
Next, we subjected the six IP addresses (i.e., the two originally identified as IoCs and four additional hosts) to reverse IP lookups. We found that two of them could be dedicated although they did not lead to any other connected domain that has not been dubbed an IoC or email-connected.
To cover all the bases, we used exact text strings found among the five domains named as IoCs as Domains & Subdomains Discovery search terms. That led to the discovery of 72 string-connected domains.
To satisfy our curiosity, we searched for possible signs of iCloud impersonation. A Domains & Subdomains Discovery search for icloud-containing domain names created just this year (i.e., since 1 January 2024) uncovered 785 such web properties.
WHOIS record comparisons with apple[.]com showed that only one of them—icloud[.]global—could be publicly attributed to Apple based on its registrant organization.
Threat Intelligence API also revealed that eight of the icloud-containing domains were associated with phishing and generic threats. Specifically, all were phishing-related and one was also associated with a generic threat.
For our second case, SentinelOne identified four IP addresses as IoCs. IP geolocation lookups for them showed that:
To find other potentially connected artifacts, we began with reverse IP lookups for the four IP addresses tagged as IoCs. We found out that three of them could be dedicated and enabled us to collate 28 IP-connected domains after duplicates were removed.
Threat intelligence lookups for the 28 IP-connected domains revealed that all of them were associated with malware attacks.
Our in-depth DNS foray into two of the latest macOS backdoors using a total of 11 IoCs as expansion analysis jump-off points led to the discovery of 109 potentially connected artifacts. Specifically, they allowed us to uncover five email-connected domains, four additional IP addresses, 28 IP-connected domains, and 72 string-connected domains. The analysis also revealed that 29 of the web properties we dug up were malicious—one was associated with phishing and 28 could be malware hosts.
That said, the 109 additional artifacts possibly related to RustDoor and KandyKorn inferred the presence of additional threats that have not yet been identified or reported to date. And the 785 icloud-containing domains, eight of which were malicious, pointed to threats targeting the cloud service.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byCSC

Sponsored byIPv4.Global

Sponsored byDNIB.com

Sponsored byRadix

Sponsored byVerisign

Sponsored byVerisign

Sponsored byWhoisXML API
