


|
||
|
||
A new info-stealing malware called “TimbreStealer” is in town. Cisco Talos detected its distribution through a phishing campaign targeting Mexico. The threat actors used finance-themed phishing emails to lure victims in, including generic fake invoices and those imitating invoices from Comprobante Fiscal Digital por Internet (CDFI), the country’s standard electronic invoice format.
The new malware has been dubbed sophisticated since it uses obfuscation techniques to bypass monitoring and enable persistent presence in victims’ devices. Despite this sophistication, Talos published a list of indicators of compromise (IoCs) comprising 24 IP addresses, 124 subdomains, and four domains. Our research team expanded the IoC list, which led to the discovery of:
A sample of the additional artifacts obtained from our analysis is available for download on our website.
The first step in our attack infrastructure analysis was to obtain the WHOIS details of the four domains tagged as IoCs. For this analysis, we also extracted 34 root domains from the 124 subdomains found on the IoC list. All in all, we did a bulk WHOIS lookup for 38 domains, which revealed that:

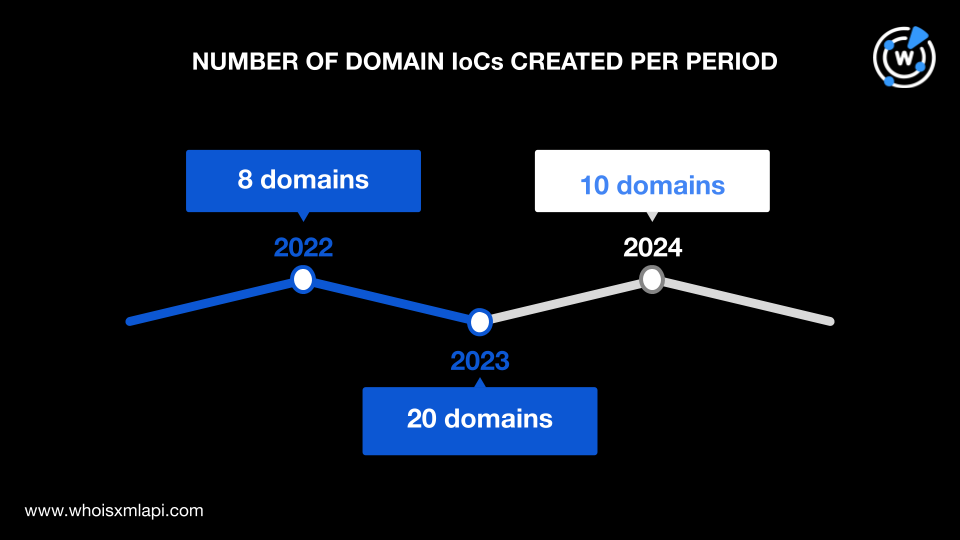
The oldest domain was registered in June 2022, while the newest ones were created in January 2024. Most of the domains, 20 to be exact, were created in 2023, eight were registered in 2022 and 10 in 2024.
Their registrations were spread across only two countries. Five domains were registered in Iceland and 32 in the U.S. One domain did not have current registrant country data.

We then subjected the IP addresses tagged as IoCs to a bulk IP geolocation lookup. We found that all 24 IP addresses were geolocated in the U.S. and managed by the same ISP, DigitalOcean LLC.

After analyzing the IoCs, we then sought to uncover threat artifacts or web properties that could be connected to the TimbreStealer malware infrastructure.
WHOIS History API searches for the domain IoCs led our research team to discover 52 email addresses in their historical WHOIS records, 12 of which were public. Reverse WHOIS API revealed that these public email addresses appeared in the current WHOIS records of 806 domains.
However, since one of the email addresses was used to register 695 domains and was likely owned by a domainer, it was excluded, along with its connected domains. That left us with 111 email-connected domains after filtering out duplicates and IoCs.
We then obtained the IP resolutions of the four domains and 124 subdomains tagged as IoCs by performing DNS lookups. The exercise led to the discovery of 11 additional IP addresses, two of which were used to resolve more than 100 of the subdomain IoCs.
Running IP geolocation lookups on the 11 IP addresses revealed that:
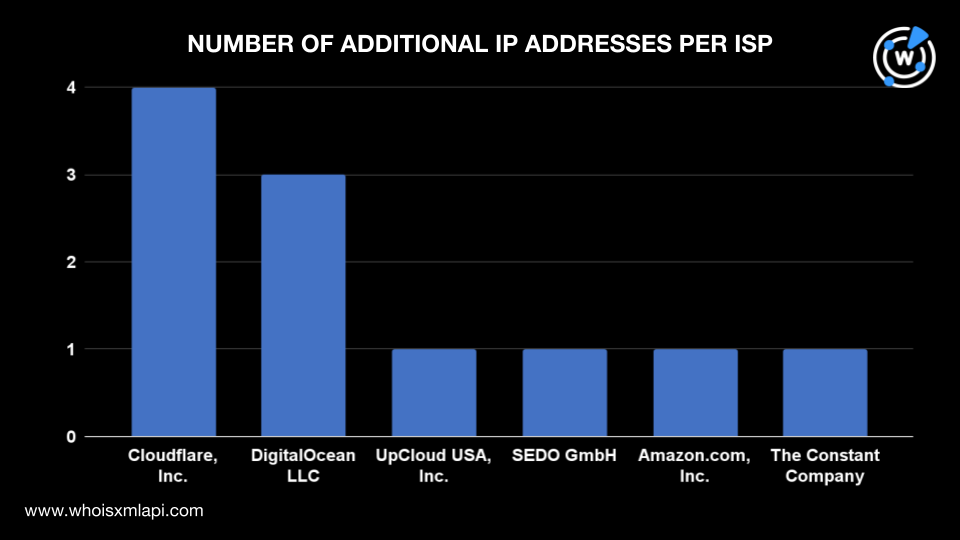
They were administered by six ISPs. Cloudflare, Inc. managed four IP addresses; DigitalOcean LLC, three; and UpCloud USA, Inc., SEDO GmbH, Amazon.com, Inc., and The Constant Company managed one IP address each.
We also ran the 11 additional IP addresses on Threat Intelligence API, which revealed that five were associated with various threats. A couple of examples are shown in the table below.
| IP ADDRESSES | ASSOCIATED THREAT TYPES |
|---|---|
| 172[.]67[.]164[.]129 | GenericPhishingMalware |
| 91[.]195[.]240[.]12 | Command-and-control (C2)PhishingMalwareSpam |
Next, we subjected the 35 IP addresses in total (i.e., 24 IP addresses tagged as IoCs and 11 additional IP addresses) to reverse IP lookups, which showed that 11 were potentially dedicated. They led to 38 IP-connected domains after removing duplicates, the IoCs, and the email-connected domains.
Finally, we analyzed the IoCs’ string usage, noting the subdomain string pattern involving eight Spanish words and two tech-related terms, each followed by random numbers. As previously mentioned, these seemingly domain generation algorithm (DGA)-created subdomains were spread across 34 different root domains.
To find similar subdomains, we used Domains & Subdomains Discovery and found 18,798 subdomains created from 1 January 2023 to 4 March 2024. These subdomains started with the text strings below and immediately followed by the numbers 0 to 9 (e.g., auditoria0, auditoria1, auditoria2, auditoria3, auditoria4, etc.).
Meanwhile, domain searches using the text strings that appeared among the domain IoCs and the root domains of the subdomain IoCs unveiled 452 string-connected domains added from 1 January 2023 to 4 March 2024. These domains started with the following text strings:
Threat Intelligence API revealed that some of the string-connected web resources were associated with malware and phishing activities. Examples include:
Our TimbreStealer investigation began with four domains, 24 IP addresses, and 124 subdomains tagged as IoCs for a Mexico-targeted malware distribution campaign. After analyzing their WHOIS records, IP geolocation data, and string usage, we discovered more than 19,000 connected artifacts comprising 12 public email addresses, 111 email-connected domains, 11 additional IP addresses, 38 IP-connected domains, 452 string-connected domains, and 18,798 string-connected subdomains.
It is also important to note that the campaign exclusively targeted people in Mexico using geofencing techniques. Users attempting to connect to the malicious resources from other locations cannot access the malicious PDF. As a result, our screenshot analyses for the IoCs and artifacts did not yield relevant results.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byCSC

Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byRadix

Sponsored byIPv4.Global

Sponsored byWhoisXML API

Sponsored byVerisign
