


|
||
|
||
Glupteba, an advanced piece of malware, has been used in several cybercriminal attacks for more than a decade now. But Palo Alto’s Unit 42 only brought to light one of the features that made it so effective—its Unified Extensible Firmware Interface (UEFI) bootkit component, which allowed it to intervene and control the operating system (OS) boot process and be extremely difficult to detect and remove, last November 2023.
That same Unit 42 analysis also unveiled 12 domains identified as Glupteba indicators of compromise (IoCs).
In a bid to uncover more potentially connected artifacts, the Threat Intelligence Platform (TIP) research team expanded the list of IoCs and found:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
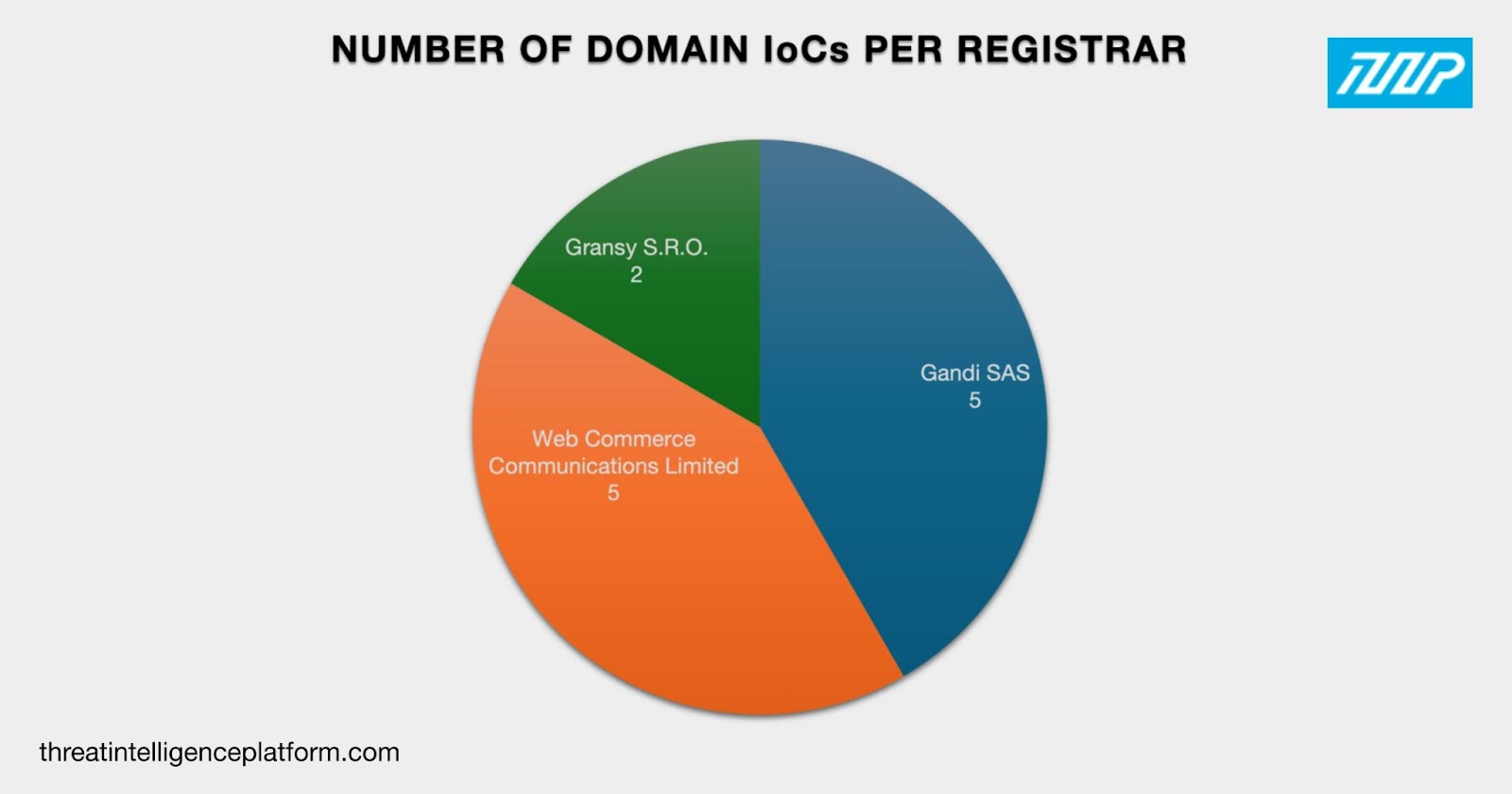
To gather more information about the Glupteba IoCs, we looked at their WHOIS records first. We discovered that:
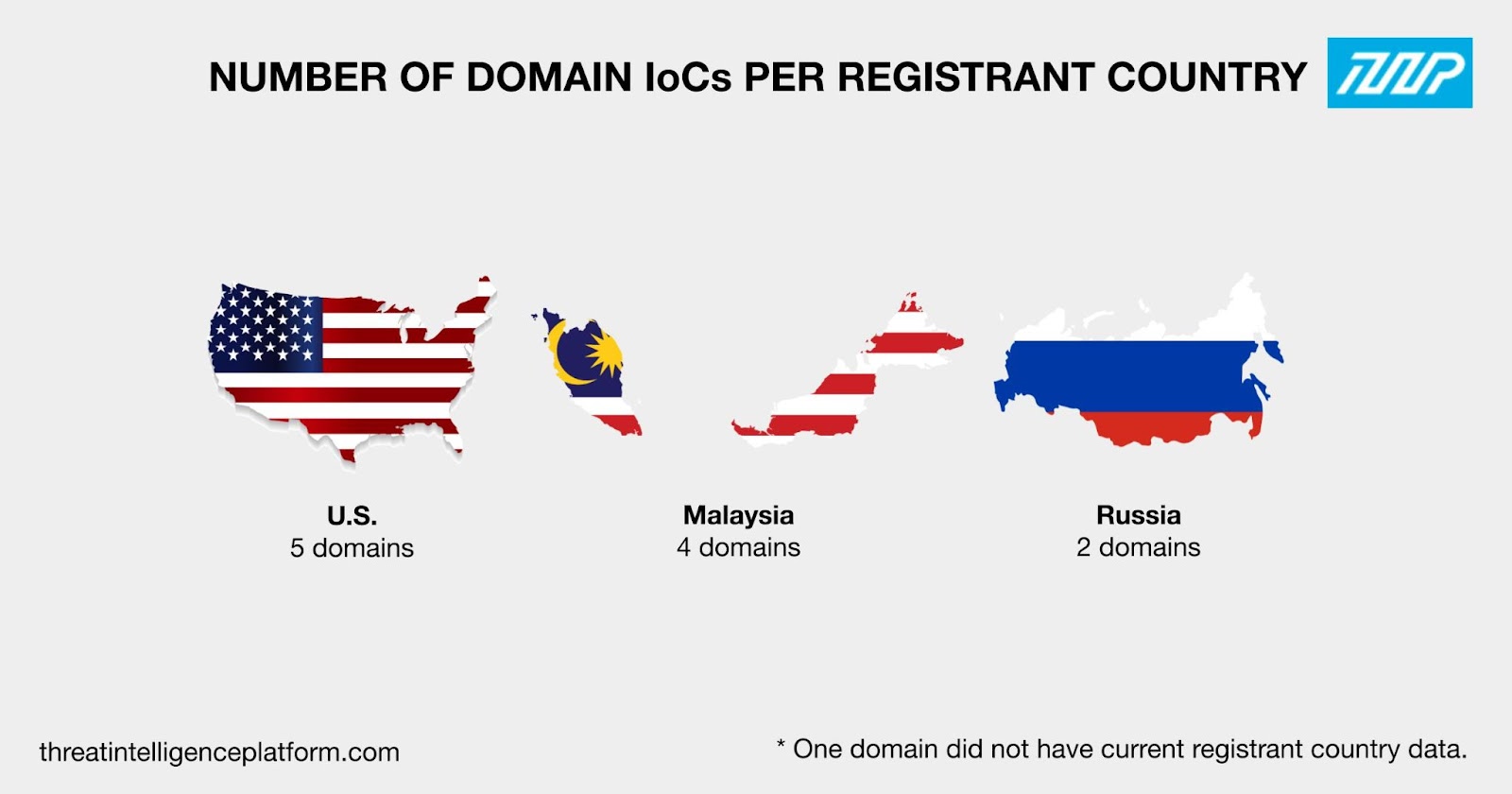
Eleven of them were spread across three registrant countries. Five were registered in the U.S., four in Malaysia, and two in Russia. One domain did not have registrant country data in its current WHOIS record.
We then proceeded with expanding the list of Glupteba IoCs to uncover more information about the bootkit’s infrastructure.
First, we looked for other domains whose WHOIS records contained the same registrant organization as the domain IoCs lightseinsteniki[.]org, liuliuoumumy[.]org, snukerukeutit[.]org, and sumagulituyo[.]org. We found 3,612 registrant-connected domains after duplicates and the IoCs were removed. A total of 838 of them turned out to be malicious. Here are five examples that have been flagged for at least two associated threat types.
| MALICIOUS REGISTRANT-CONNECTED DOMAIN | ASSOCIATED THREAT TYPES |
|---|---|
| abscete[.]info | Malware Command and control (C2) |
| ahoravideo-chat[.]com | C2 Malware Generic |
| blesblochem[.]com | Malware C2 |
| ge5r6h7tjrfrhegs[.]top | Malware C2 |
| grectedparices[.]ru | Malware C2 |
It is also interesting to note that threat actors could have chosen at least 24 of the malicious registrant-connected domains for use in attacks since they contained popular text strings or closely resembled those belonging to famous brands that could lure more users into clicking them. These strings include:
Next, we dove deeper into the 12 domain IoCs’ historical WHOIS records. That led to the discovery of 30 email addresses, 11 of which were public. Two of the public email addresses appeared in the current WHOIS records of three domains (after duplicates, the IoCs, and the registrant-connected domains were removed) that could be part of the Glupteba infrastructure.
After that, we looked at the 12 domain IoCs’ DNS records that allowed us to determine that they resolved to four IP addresses after duplicates were filtered out. They were all associated with at least two threat types each.
| MALICIOUS IP ADDRESS | ASSOCIATED THREAT TYPES |
|---|---|
| 104[.]198[.]2[.]251 | C2Malware |
| 34[.]143[.]166[.]163 | C2 Malware Generic Phishing |
| 34[.]168[.]225[.]46 | C2 Malware Generic |
| 34[.]94[.]245[.]237 | C2 Malware Phishing |
These four IP addresses were geolocated in two countries—three in the U.S. and one in Singapore.
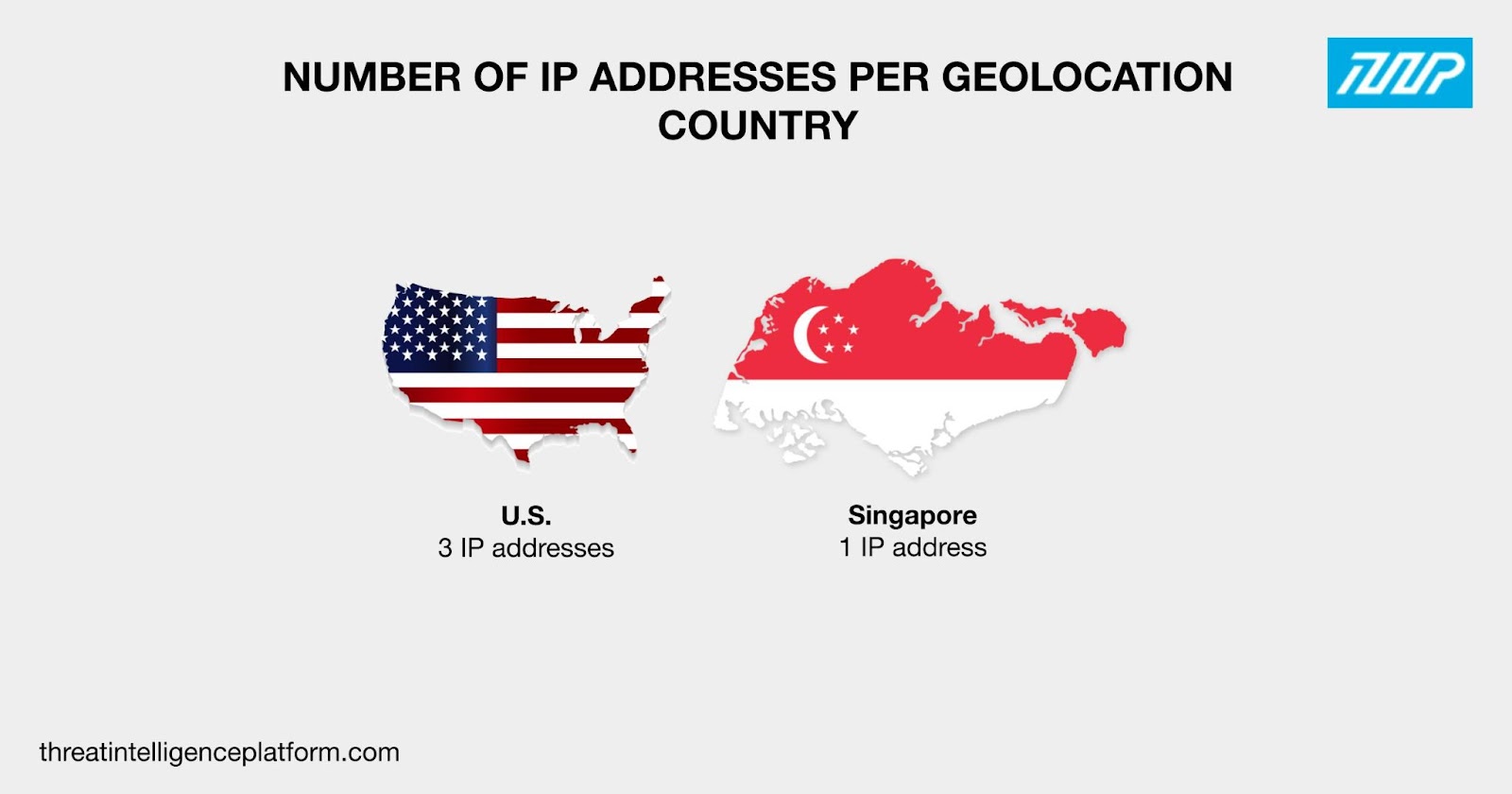
All four IP addresses were administered by a single ISP—Google LLC. None of them appeared to be dedicated, though, which hindered us from obtaining IP-connected domains.
To cover all the bases, we scoured the DNS for domains starting with text strings found among the 12 domain IoCs created since 1 November 2023 when the campaign was believed to have started. We discovered that one of them—dpav.—also appeared in five other domains after filtering out duplicates, the IoCs, and the registrant- and email-connected domains.
Our analysis of the Glupteba UEFI bootkit IoCs enabled us to uncover 3,624 potentially connected artifacts comprising 3,612 registrant-connected domains, three email-connected domains, four IP addresses, and five string-connected domains. A total of 842 of them—838 registrant-connected domains and four IP addresses—were associated with various threats as of this writing.
We also learned that at least 24 of the malicious registrant-connected domains may have mimicked famous brands or their products (i.e., Adobe, Dell, Facebook, LinkedIn, Kaspersky, Microsoft, and Mozilla) and personalities (i.e., Brian Krebs) in hopes of luring more victims in.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byVerisign

Sponsored byCSC

Sponsored byIPv4.Global

Sponsored byRadix

Sponsored byDNIB.com

Sponsored byWhoisXML API

Sponsored byVerisign
