


|
||
|
||
Intel-Ops researchers recently discovered that the 8Base Ransomware Group has been using Phobos ransomware to infect their targets’ networks. 8Base has reportedly been active since mid-2023.
The Phobos operators have been selling the ransomware’s multiple variants (e.g., Eking, Eight, Elbie, Devos and Faust) via the ransomware-as-a-service (RaaS) model. In the past, various groups utilized the ransomware to infect several targets, including county governments, emergency service providers, educational institutions, public healthcare service providers, and other critical infrastructure entities, successfully collecting ransom amounting to millions of U.S. dollars.
Sixty-three indicators of compromise (IoCs) comprising 46 domains and 17 IP addresses were made public in relation to the 8Base Phobos ransomware attack featured in this post. The WhoisXML API research team expanded the IoC list in a bid to find other potentially connected artifacts and uncovered:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
As per usual, we sought to find more information about the 63 IoCs. We began by subjecting the 46 domains identified as IoCs to a bulk WHOIS lookup, which revealed that:
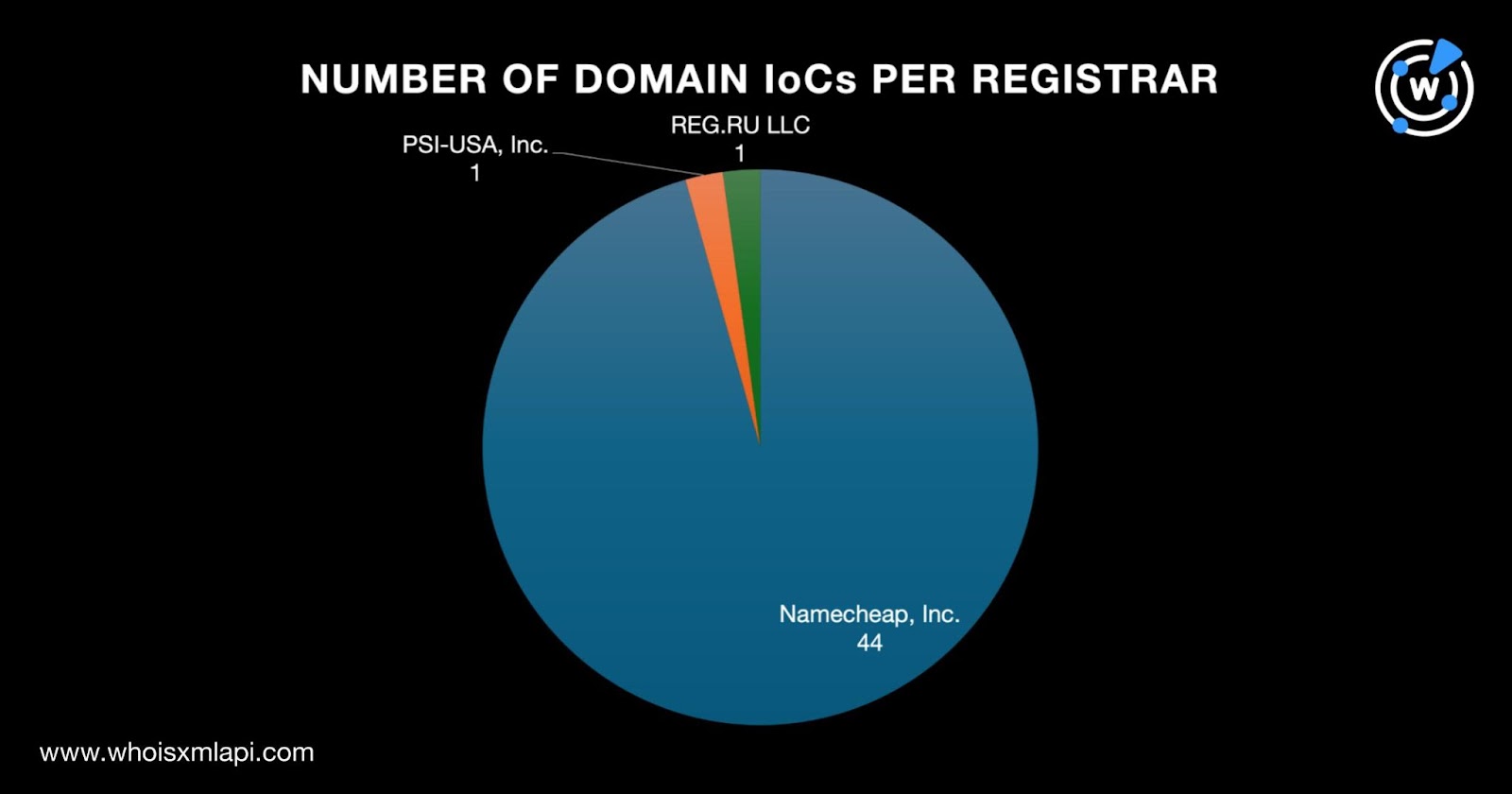
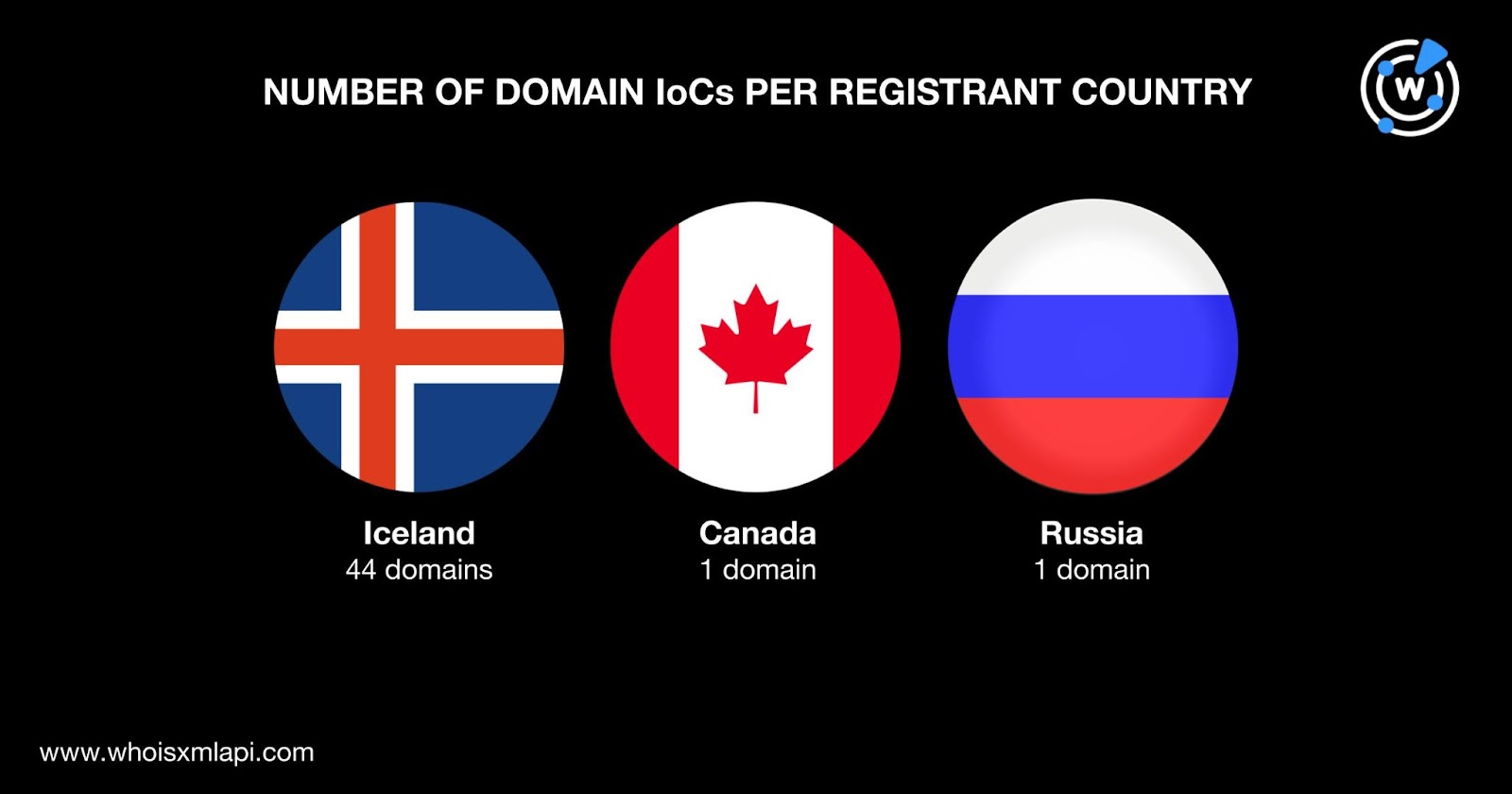
A majority of the domain IoCs, 44 to be exact, were registered in Iceland. One domain IoC each was registered in Canada and Russia.
Next, we performed a bulk IP geolocation lookup for the 17 IP addresses identified as IoCs and found that:
To find out if 8Base had other domains and IP addresses in its attack infrastructure, we expanded the list of IoCs starting with WHOIS History API queries for the 46 domain IoCs. That led to the discovery of four email addresses from their historical WHOIS records. Three of the four email addresses were public.
Reverse WHOIS API queries for the three public email addresses provided us with 368 connected domains after duplicates and the IoCs were filtered out. Close to 200 of the email-connected domains, 193 to be exact, sported the .pro ngTLD extension, akin to one domain IoC. The 175 remaining email-connected domains, meanwhile, were spread across seven TLD extensions, specifically .cn, .hk. .com.cn, .top, .com, .tw, and .us.

A bulk WHOIS lookup for the 368 email-connected domains showed that 144 were, like the domain IoCs, created in 2023.
Next, we ran DNS lookups for the 46 domains identified as IoCs and found that some of them resolved to three IP addresses that are not in the current IoC list.
Threat intelligence lookups for the three additional IP addresses revealed that one—45[.]89[.]127[.]159—was seemingly associated with malware distribution.
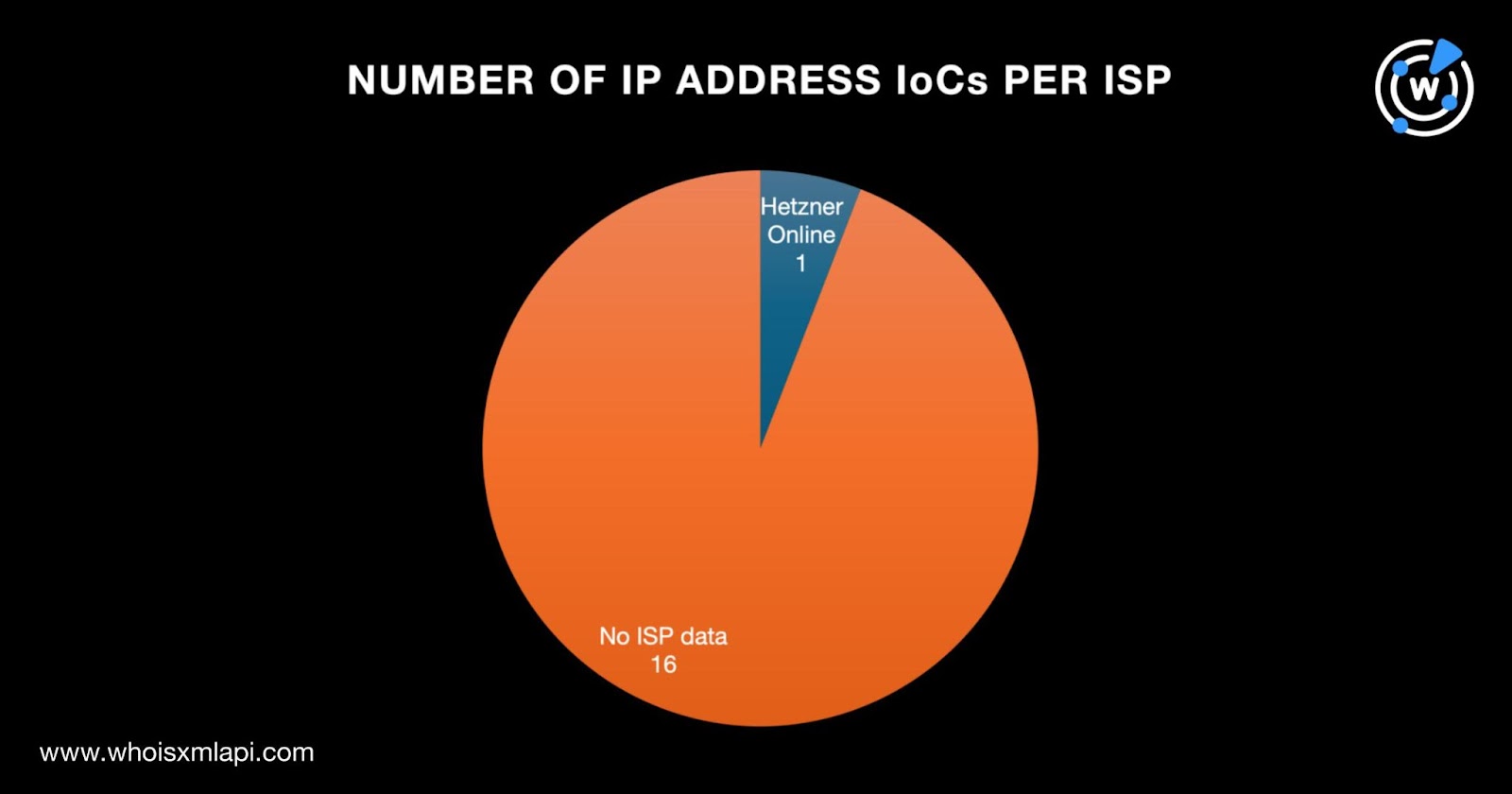
And like the 17 IP addresses identified as IoCs, a bulk IP geolocation lookup for the three additional IP addresses showed they all originated from Germany even though only one—88[.]198[.]21[.]27—had public ISP data. It was administered by Hetzner Online.
Next, we ran reverse IP/DNS lookups for 20 IP addresses in total (17 identified as IoCs and three additional from the DNS lookups) and found that 10 of them could be dedicated hosts. The 10 remaining IP addresses showed no results.
Altogether the 10 possibly dedicated IP addresses hosted 13 domains after duplicates, the IoCs, and the email-connected domains were filtered out. More than half of the IP-connected domains, seven to be exact, sported the .de ccTLD extension, consistent with the geolocation lookup results. The six remaining IP-connected domains, meanwhile, were spread across five TLD extensions, specifically .com, .me, .net, .org, and .team. Note that .net was also used by one domain IoC.
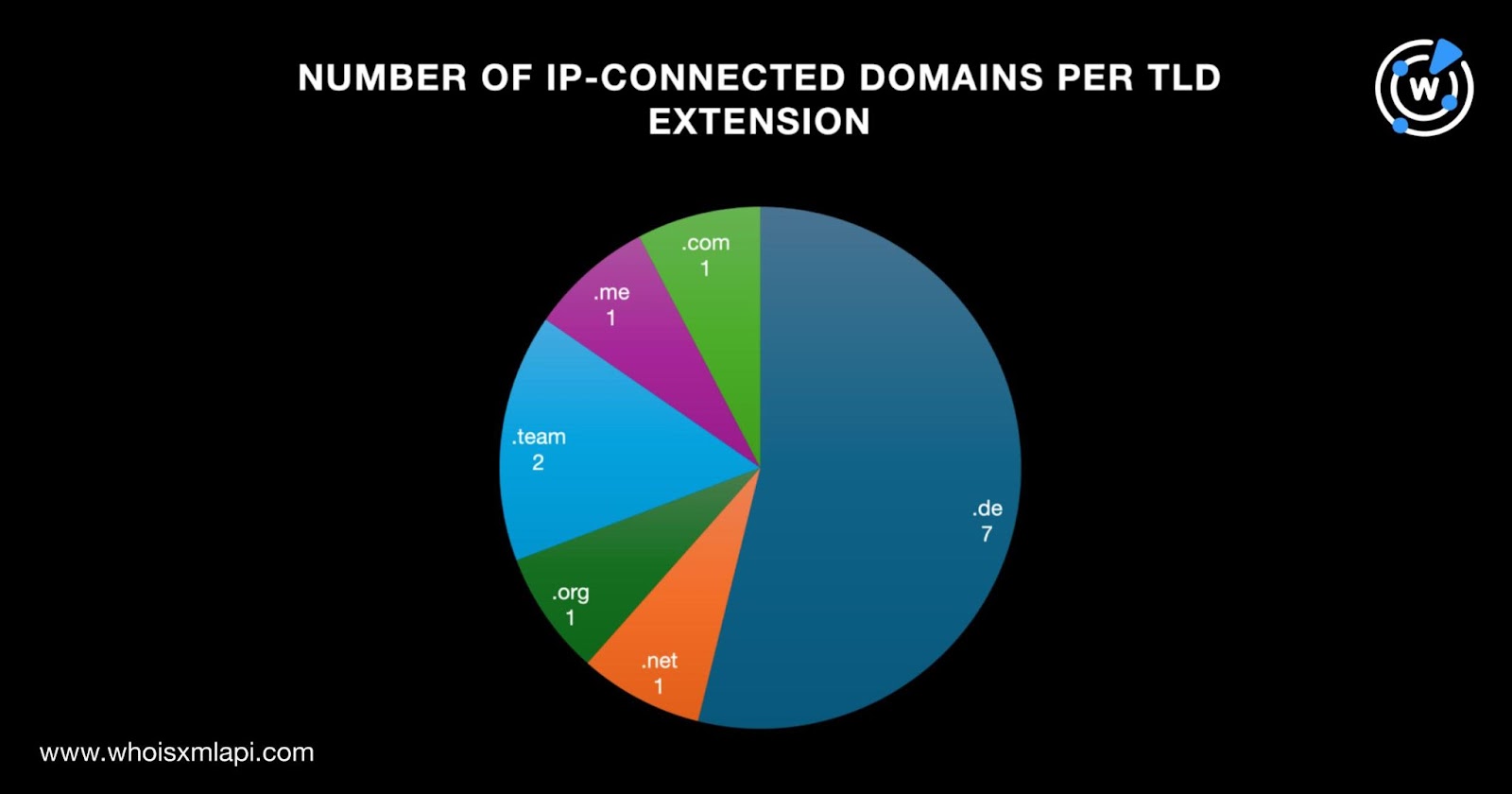
A bulk WHOIS lookup for the 13 IP-connected domains showed that like the domain IoCs, four were created in 2023.
To cover all the bases, we then looked for other domains starting with the same text strings seen among the domain IoCs using Domains & Subdomains Discovery. We uncovered 20 domains after filtering out duplicates, the IoCs, and email- and IP-connected domains containing these seven strings:
Given that they only used different TLD extensions from the domains identified as IoCs, they could be weaponized for similar attacks. It is also interesting to note that serv appeared in 12 of the string-connected domains in combination with adv or blog. 8Base could be using supposed advertising or blog servers or services as a social engineering ruse.
Throughout our investigation, interesting similarities between the IoCs and potentially connected artifacts stood out, namely:
Our further investigation of the latest 8Base Phobos ransomware attack led to the discovery of 404 potentially connected web properties. We specifically found 401 email-, IP-, and string-connected domains and three IP addresses.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byWhoisXML API

Sponsored byRadix

Sponsored byCSC

Sponsored byIPv4.Global

Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byVerisign
