


|
||
|
||
Cybercriminals can launch distributed denial-of-service (DDoS) attacks with relative ease these days by using DDoS booter services, online services that automate the DDoS attack process.
WhoisXML API threat researcher Dancho Danchev recently uncovered a list of the user information for a popular DDoS booter service, which our research team used to create a profile and expand to identify related artifacts. Jumping off a list of 171 domains, 464 IP addresses, and nine email addresses involved in the DDoS booter service operation, we found:
A sample of the additional artifacts obtained from our analysis is available for download on our website.
As a first step, we did a bulk WHOIS lookup for the 171 domains tagged as IoCs to obtain their WHOIS details. We found that:
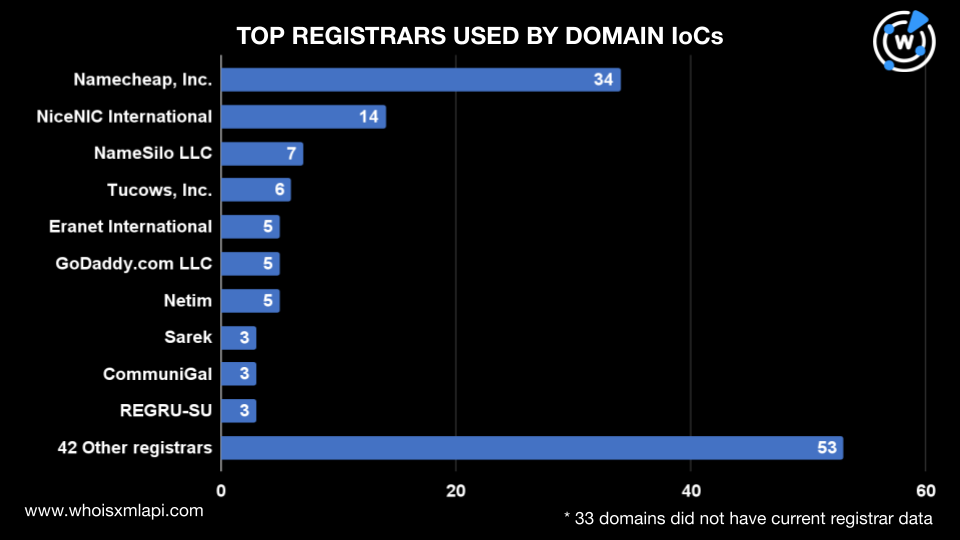
The oldest domain was registered in May 2019, while the newest ones were recently created, specifically in May 2024. Most of the domains, 66 to be exact, were created in 2023, six in 2020, eight in 2021, 30 in 2022, and 19 in 2024. Forty-one domain IoCs didn’t have creation dates in their current WHOIS records.
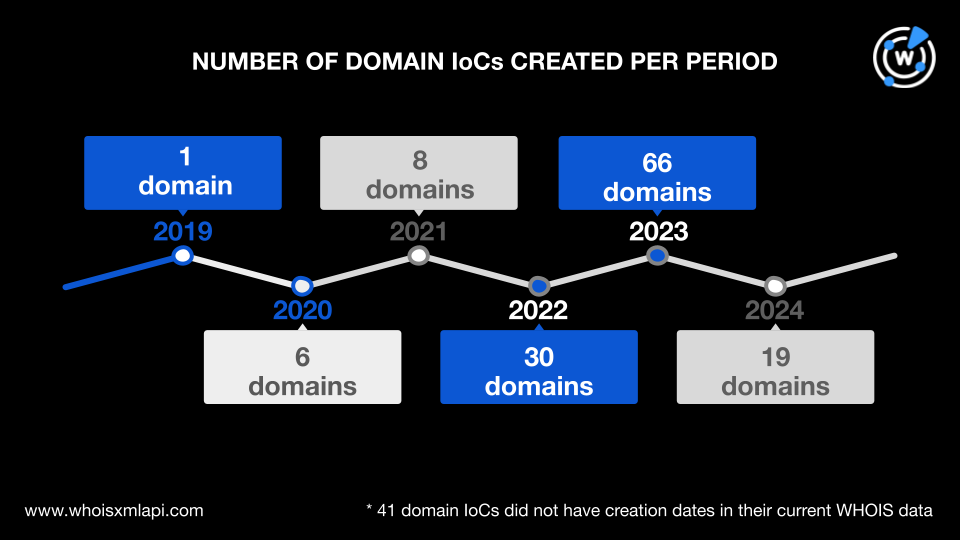
Their registrations were spread across 20 countries. The top 10 registrant countries are shown in the graph below, led by Iceland with 30 domains and the U.S. with 29. Ten domains were registered in Russia; six in the Netherlands; five each in Cyprus and Saint Kitts and Nevis; three each in China, the U.K., and Hungary; and two in Japan. Fifteen domain IoCs were registered across 10 other countries, while 60 did not have current registrant country data.
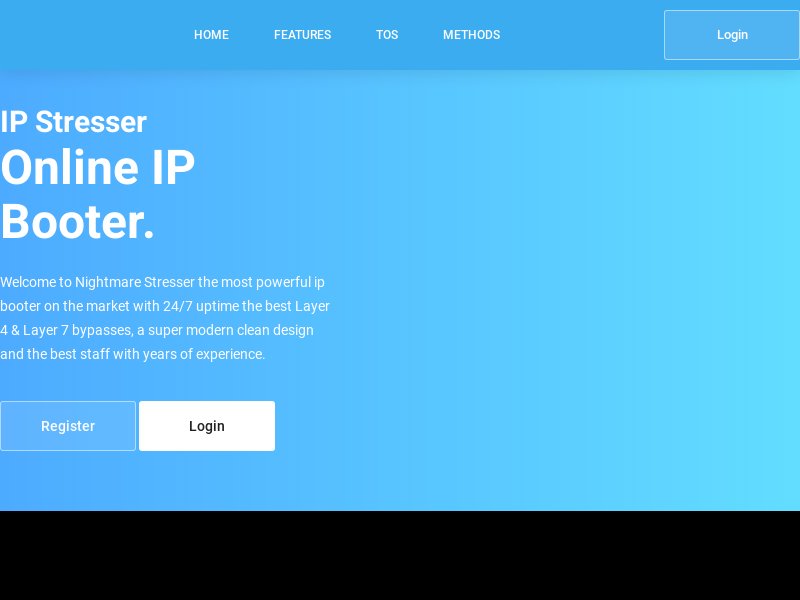
Some of the domains have already been seized by the Federal Bureau of Investigation (FBI), as revealed by Screenshot API.

Still, some domains continued to host content offering DDoS-related tools. Some of them are shown below.
Next, we subjected the 464 IP addresses to a bulk IP geolocation lookup and found that:
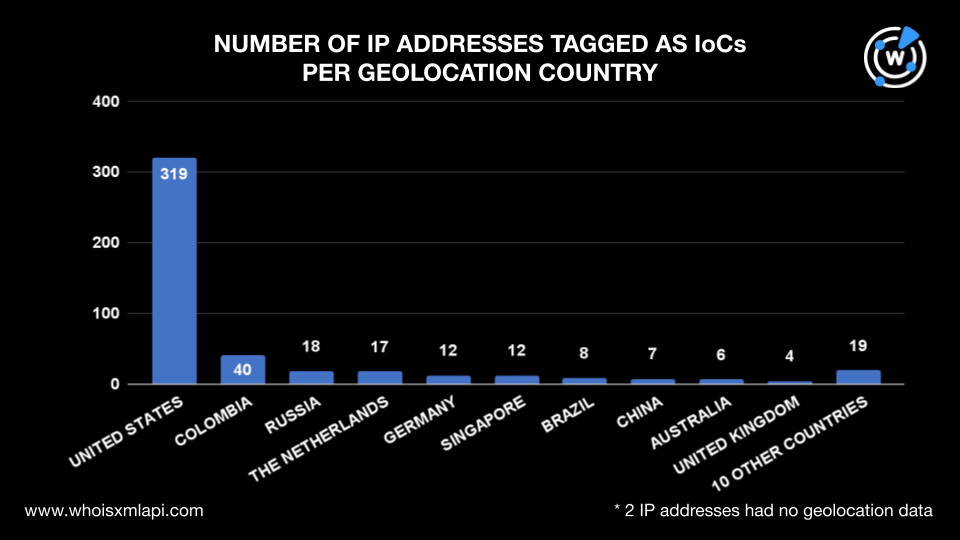
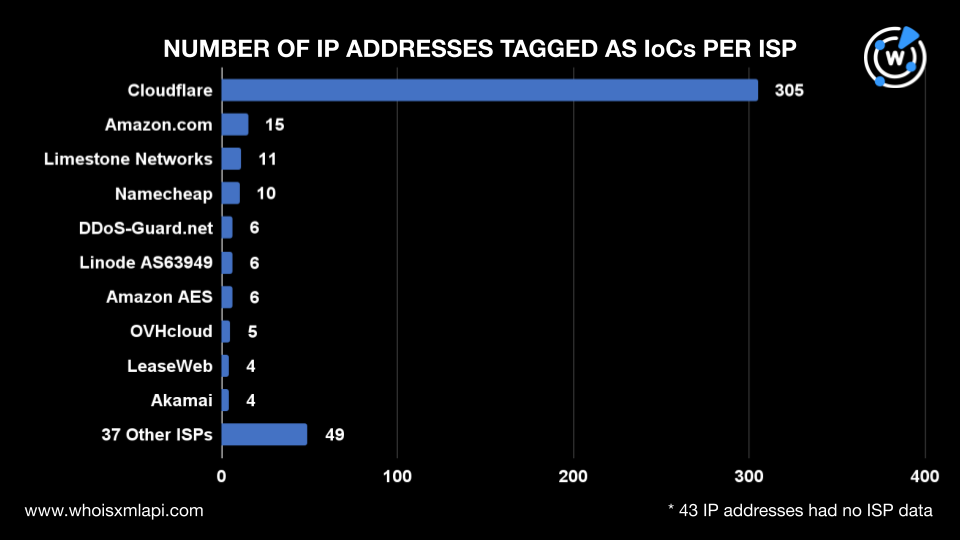
The IP addresses were administered by 47 ISPs, with Cloudflare managing 305; Amazon with 15; Limestone Networks with 11; Namecheap with 10; DDoS-Guard.net, Linode AS63949, and Amazon AES with six each; OVHcloud with five; and LeaseWeb and Akamai with four each. 49 IP addresses were administered by other ISPs, while 43 did not have ISP information.
After examining the IoCs, we searched for potential threat artifacts and web properties associated with the DDoS booter.
WHOIS History API searches for the domain IoCs led our research team to discover 175 email addresses in their historical WHOIS records, 20 of which were public. We then ran these public email addresses and the nine email addresses tagged as IoCs on Reverse WHOIS API, which revealed that they appeared in the current WHOIS records of more than 15,000 domains. After filtering out the IoCs and domains that may belong to domainers (i.e., email addresses used to register more than 50 domains), we were left with 43 email-connected domains.
We then obtained the IP resolutions of the 171 domains tagged as IoCs by performing DNS lookups, which led to the discovery of 185 additional IP addresses. Running IP geolocation lookups on the IP addresses revealed that:
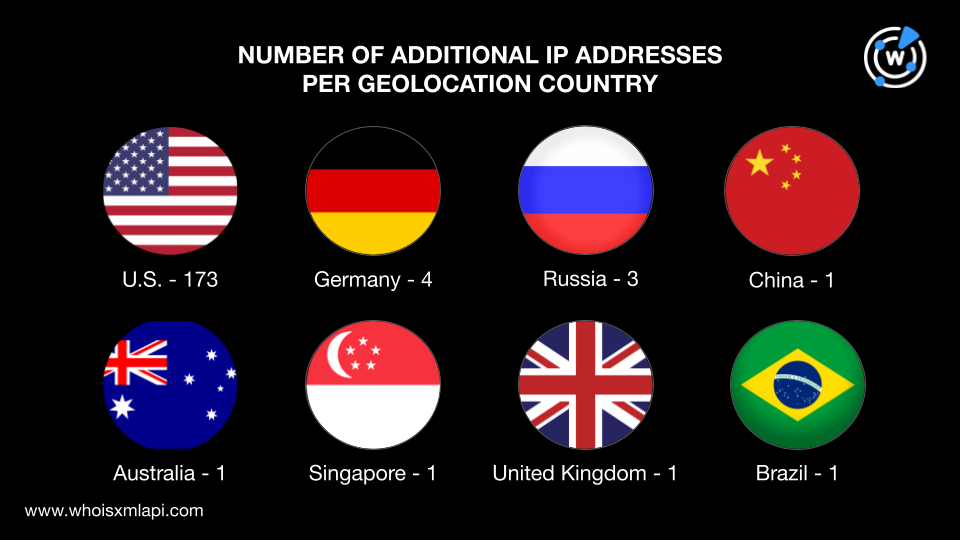
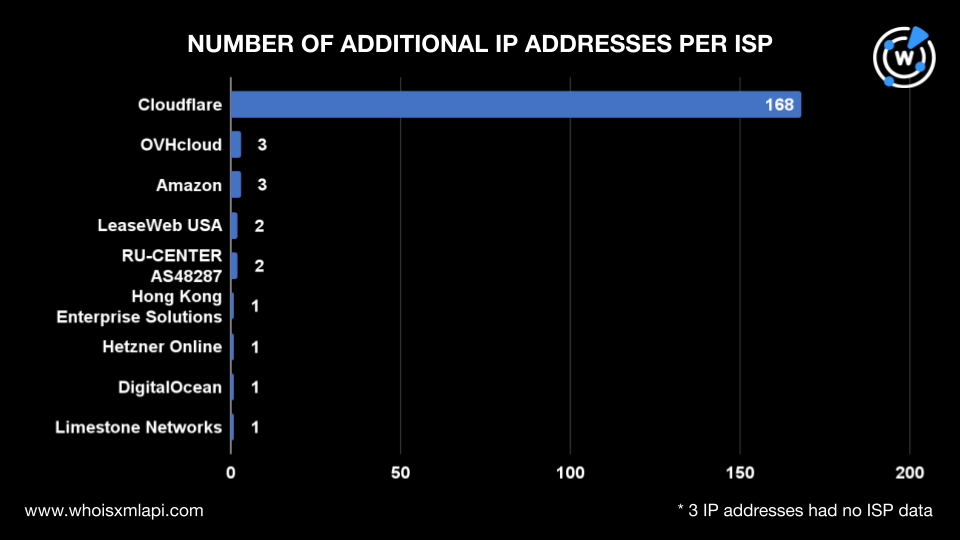
Nine ISPs administered them. Cloudflare, Inc. managed 168 IP addresses; OVHcloud and Amazon each managed three; LeaseWeb USA and RU-CENTER AS48287 each managed two; and Hong Kong Enterprise Solutions, Hetzner Online, DigitalOcean, and Limestone Networks each managed one.
We also ran the 185 additional IP addresses on Threat Intelligence API, which revealed that they were all associated with various threats. The table below shows a few examples.
| IP ADDRESSES | ASSOCIATED THREAT TYPES |
|---|---|
| 54[.]157[.]24[.]8 | Command and control (C&C) Generic Phishing Malware |
| 104[.]21[.]11[.]249 | Phishing Malware |
| 172[.]67[.]150[.]206 | Phishing Malware |
| 2606:4700:3032::ac43:96ce | Phishing Malware |
| 2606:4700:3032::ac43:911c | Phishing Malware |
Next, we subjected the 649 IP addresses in total (i.e., 464 IP addresses tagged as IoCs and 185 additional IP addresses) to reverse IP lookups, which showed that 74 were potentially dedicated. They led to 645 IP-connected domains after removing duplicates, the IoCs, and the email-connected domains.
Finally, we analyzed the IoCs’ string usage and looked for similar-looking domains registered from 1 January 2023 to 19 May 2024. We used text strings that appeared in the 171 domains tagged as IoCs as search strings on Domains & Subdomains Discovery. This led us to 1,303 string-connected domains after removing duplicates, IoCs, and email and IP-connected domains. These domains started with the following text strings:
Threat Intelligence API revealed that dozens of the string-connected web resources were associated with malware distribution. Examples include the domains that used the same strings as those seized by the FBI, such as:
Our investigation of the DDoS booter service ecosystem began with 171 domains, 464 IP addresses, and nine email addresses. An in-depth analysis of their WHOIS records, IP geolocation, and string usage led us to 2,196 connected artifacts, including 20 additional email addresses, 43 email-connected domains, 185 additional IP addresses, 645 IP-connected domains, and 1,303 string-connected domains.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byRadix

Sponsored byWhoisXML API

Sponsored byVerisign

Sponsored byIPv4.Global

Sponsored byDNIB.com

Sponsored byCSC

Sponsored byVerisign
