


|
||
|
||
Advanced persistent threat (APT) groups will employ any means necessary to compromise the networks of their intended targets. And for Cosmic Leopard, that means using GravityRAT, an Android-based malware, and HeavyLift, a Windows-based malware loader, in their most recent operation Cisco Talos has dubbed “Operation Celestial Force.”
Cisco Talos’s in-depth investigation of Operation Celestial Force published 19 domains identified as indicators of compromise (IoCs). The WhoisXML API research team sought to find out if other threat artifacts could be found in the DNS via an IoC expansion analysis.
Our DNS deep dive led to the discovery of:
Note that this post contains only a preview of our findings. The full research, including a sample of the additional artifacts obtained from our analysis are available for download from our website.
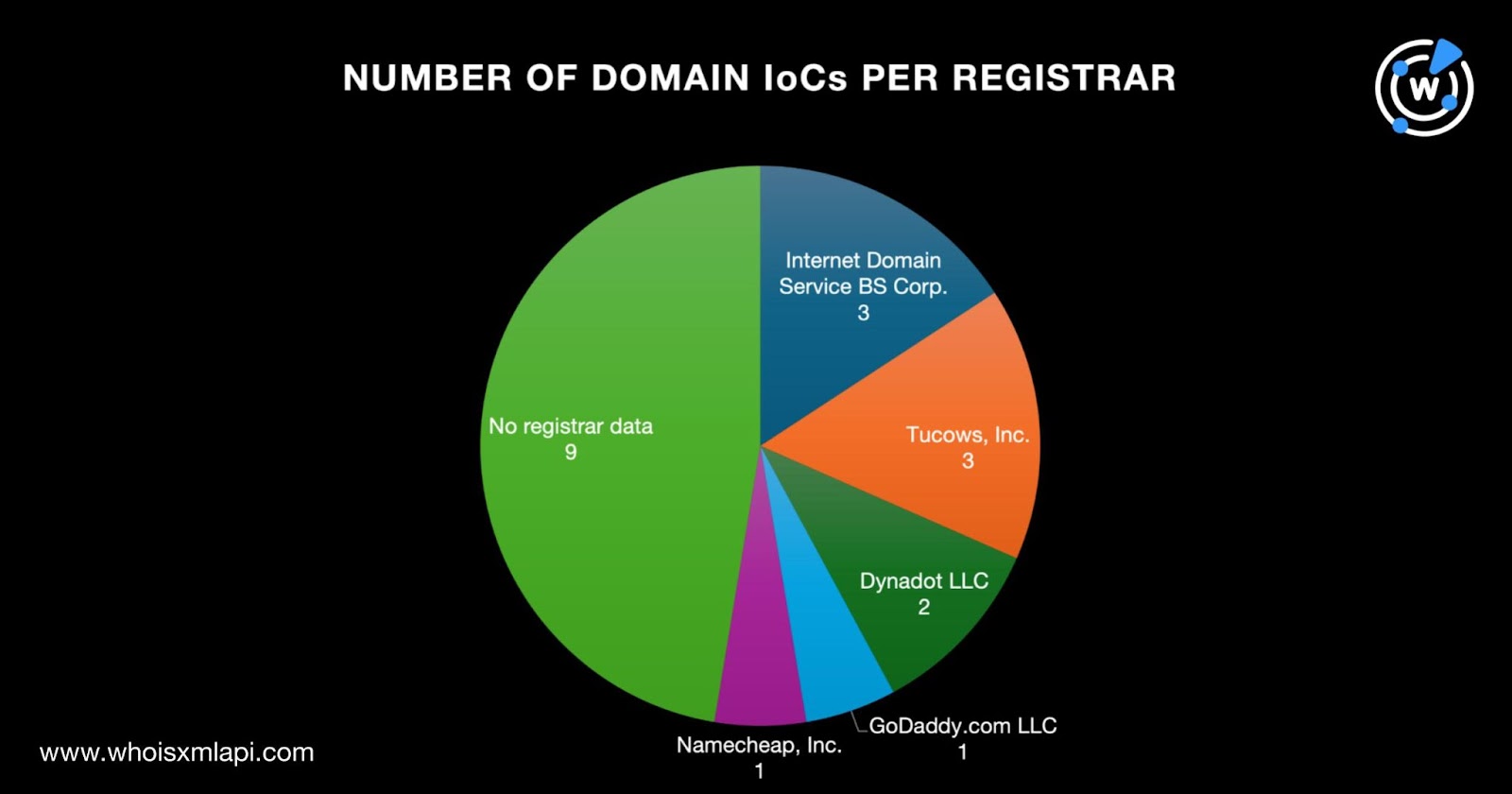
We began our analysis by subjecting the 19 domains identified as IoCs to a bulk WHOIS lookup, which revealed that:
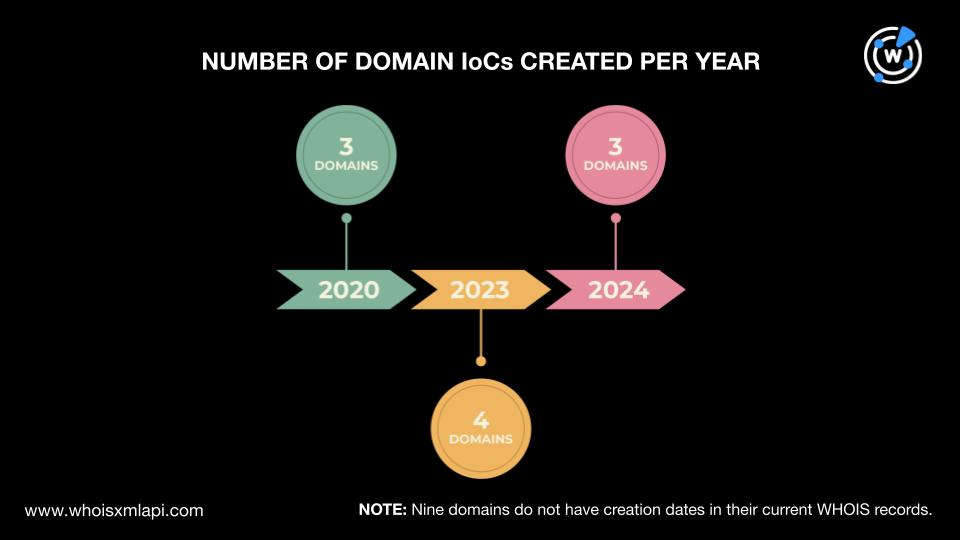
The Cosmic Leopard APT group seems to prefer using somewhat recent or newly registered domains (NRDs) for their Operation Celestial Force campaign. Three domain IoCs were created in 2020, four in 2023, and three in 2024.
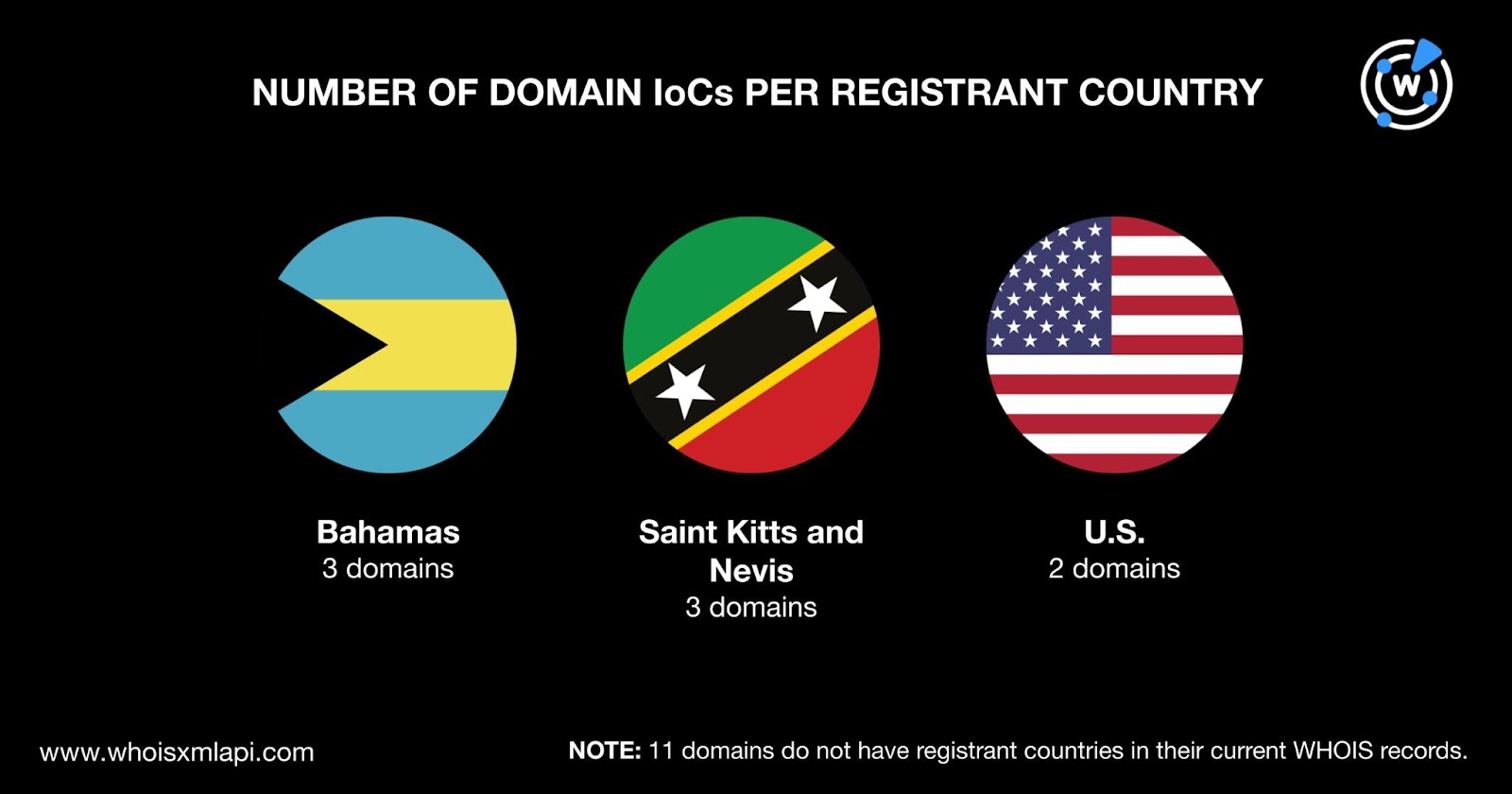
The Bahamas and Saint Kitts and Nevis tied as the top registrant countries, accounting for three domain IoCs each. The U.S. accounted for two domain IoCs. Finally, 11 domain IoCs do not have registrant countries in their current WHOIS records.
Our search for Operation Celestial Force artifacts started with running WHOIS History API queries for the 19 domains identified as IoCs. We collated 33 email addresses after filtering out duplicates from their historical WHOIS records. Only one of them, however, was a public email address.
A Reverse WHOIS API query for the sole public email address led to the discovery of three email-connected domains after filtering out duplicates and the IoCs.
To uncover more threat artifacts, we performed DNS lookups for the 19 domains identified as IoCs. We found out that they resolved to 15 IP addresses in total after filtering out duplicates. Threat intelligence lookups for them showed that they were all associated with various threats.
To know more about the 15 IP addresses, we performed a bulk IP geolocation lookup.
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byIPv4.Global

Sponsored byVerisign

Sponsored byWhoisXML API

Sponsored byDNIB.com

Sponsored byRadix

Sponsored byVerisign

Sponsored byCSC
