


|
||
|
||
The Zscaler ThreatLabz 2024 Phishing Report named Microsoft, OneDrive, Okta, Adobe, SharePoint, Telegram, pCloud, Facebook, DHL, WhatsApp, ANZ Banking Group, Amazon, Ebay, Instagram, Google, Sparkasse Bank, FedEx, PayU, Rakuten, and Gucci as the 20 most phished brands. They are proof that popularity comes at a steep price. In their case, phishers have been exploiting their customers’ trust to gain entry into as many enterprise networks as possible. Why? The 20 brands have millions of users worldwide.
The report, however, did not contain specifics about the phishing campaigns where the 20 aforementioned brands were abused. In a bid to shed more light, the WhoisXML API research team conducted an in-depth DNS investigation to find domains, subdomains, and IP addresses that could have figured in the threats or weaponized for similar attacks in the future.
Our study led to the discovery of:
Note that this post contains only a preview of our findings. The full research, including a sample of the additional artifacts obtained from our analysis are available for download from our website.
To kick off our search for digital properties that could have figured or be weaponized in the future for phishing and other cyber attacks, we needed more information about the 20 most spoofed brands first, specifically the products’ domain names and web pages and WHOIS record details.
Our bulk WHOIS lookup for the 20 most phished brands revealed that telegram[.]org and sparkasse[.]de had redacted WHOIS records, which meant exclusion from further investigation. We would not be able to determine which telegram- and sparkasse-containing domains could be publicly attributed to Telegram and the Sparkasse Financial Group. We used the data in the following table for our query.
| BRAND | DOMAIN NAME | WEB PAGE ADDRESS |
|---|---|---|
| Microsoft | microsoft[.]com | |
| OneDrive | microsoft[.]com/en-us/microsoft-365/onedrive/ | |
| Okta | okta[.]com | |
| Adobe | adobe[.]com | |
| SharePoint | microsoft[.]com/en-us/microsoft-365/sharepoint/ | |
| Telegram | telegram[.]org | |
| pCloud | pcloud[.]com | |
| facebook[.]com | ||
| DHL | dhl[.]com | |
| whatsapp[.]com | ||
| ANZ Banking Group | anz[.]com[.]au | |
| Amazon | amazon[.]com | |
| Ebay | ebay[.]com | |
| instagram[.]com | ||
| google[.]com | ||
| Sparkasse Financial Group | sparkasse[.]de | |
| FedEx | fedex[.]com | |
| PayU | payu[.]com | |
| Rakuten | rakuten[.]com | |
| Gucci | gucci[.]com |
Our analysis of the remaining 18 text strings (16 connected to brands with domains and two connected to brands with specific web pages) was broken down into three parts. In the first part, we looked for domains containing the 16 remaining most phished brands that had domain names. In the second part, we searched for subdomains where the string microsoft.com, alongside onedrive or sharepoint, appeared. The third part looked at the IP resolutions of all the malicious web properties.
Inspecting the Underbelly of the Branded Domains
The next step was to look for domain names containing text strings found in those belonging to the 16 brands left on our list, namely:
Our Domains & Subdomains Discovery searches for the 16 text strings using the Domains only, Starts with, and Added since January 1, 2023 (based on the report’s coverage) turned out 3,120 branded domains.
Threat Intelligence API revealed that 12 of the 3,120 branded domains were associated with various threats. Take a look at five examples below.
| MALICIOUS BRANDED DOMAIN | ASSOCIATED THREAT TYPES |
|---|---|
| amazon[.]org[.]gg | Phishing |
| facebook[.]com[.]br | Generic threat |
| fedex[.]info[.]pl | Phishing |
| google[.]site | Malware distribution |
| gucci[.]com[.]by | Attack |
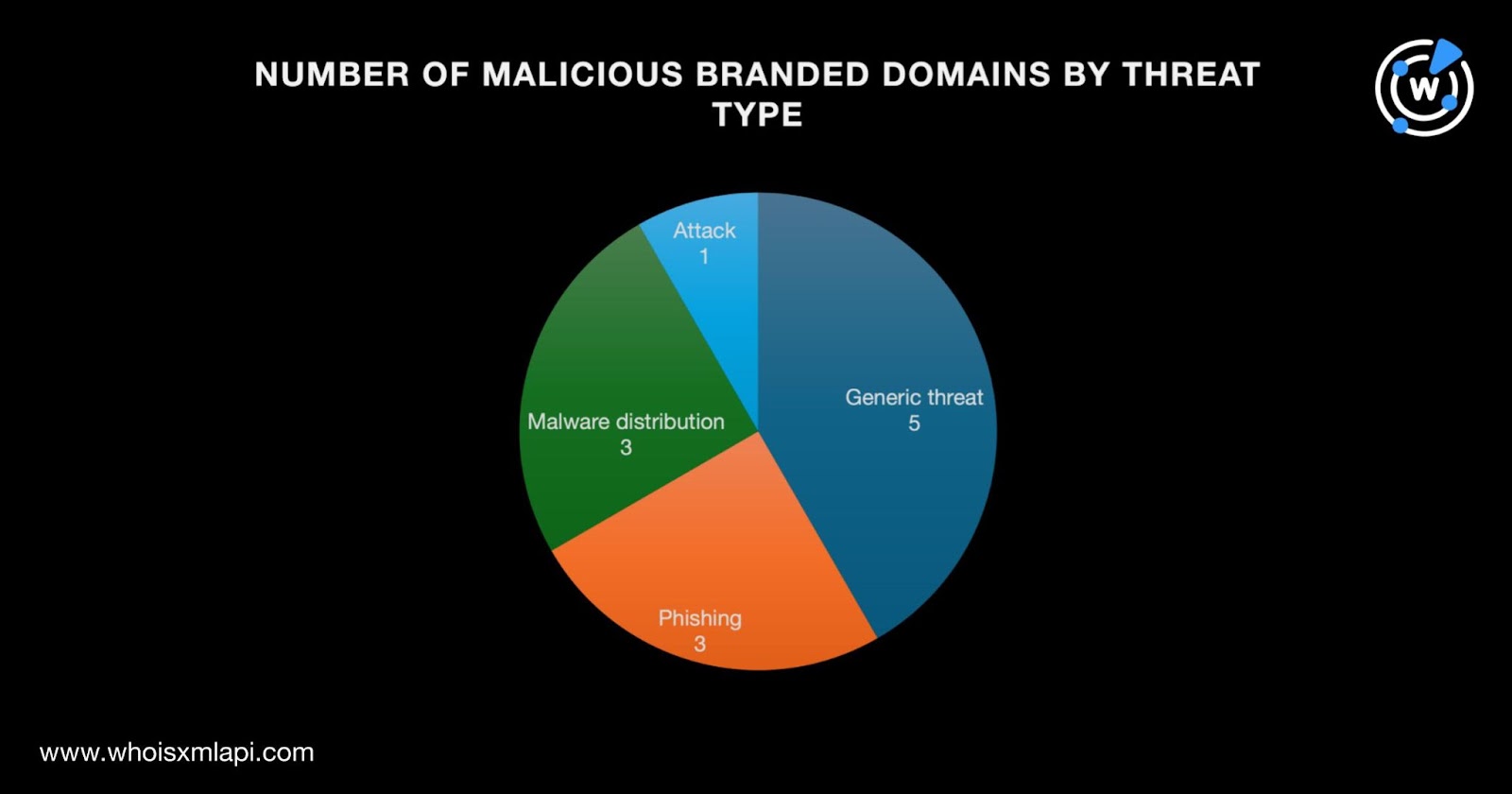
Specifically, five out of 12 malicious branded domains were associated with generic threats. Three domains each were connected to phishing and malware distribution and one with an attack.
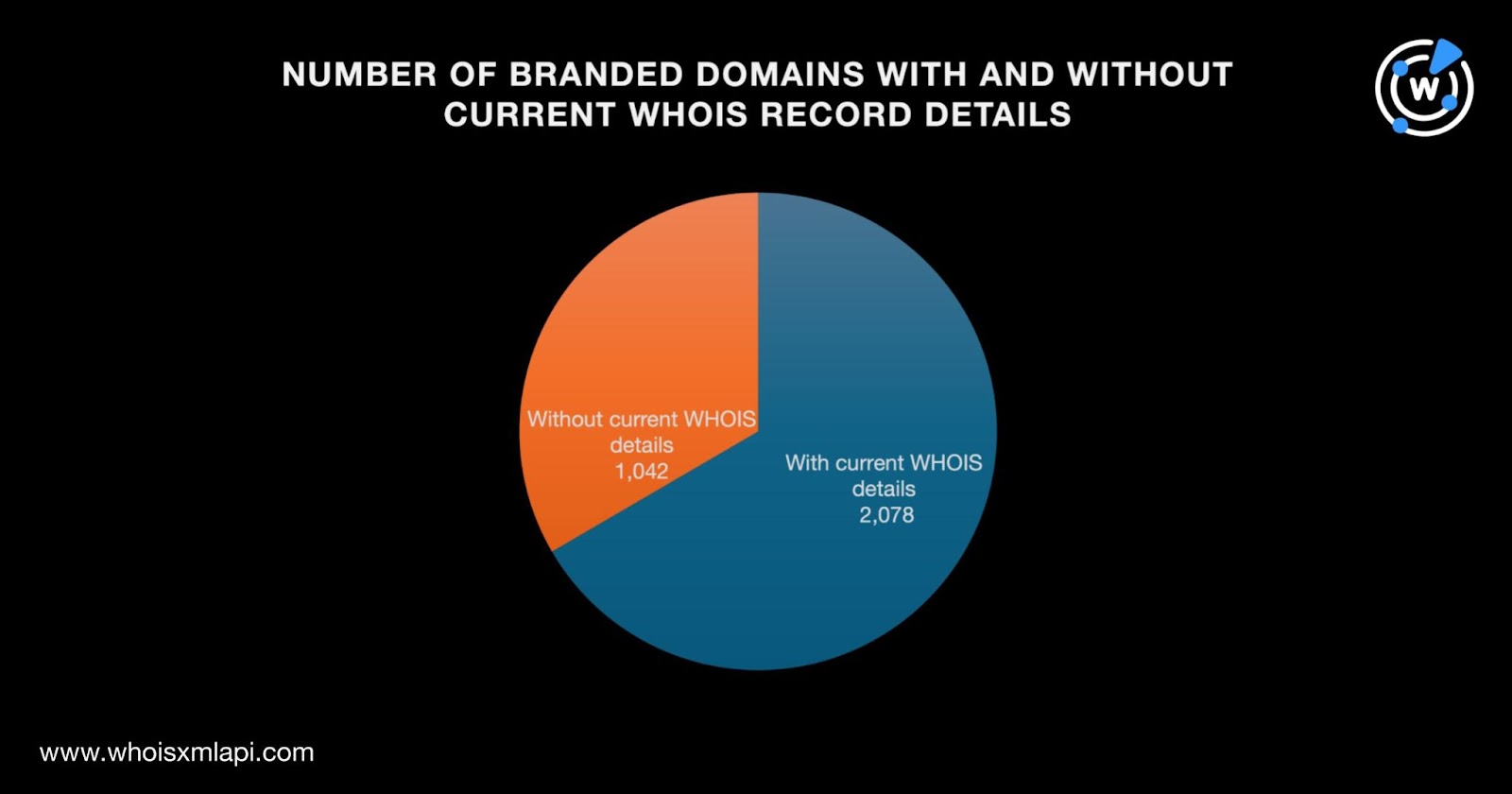
Next, we subjected the 3,120 branded domains to a bulk WHOIS lookup and found that 1,042 did not have details in their current WHOIS records. That left us 2,078 branded domains for the rest of this study.
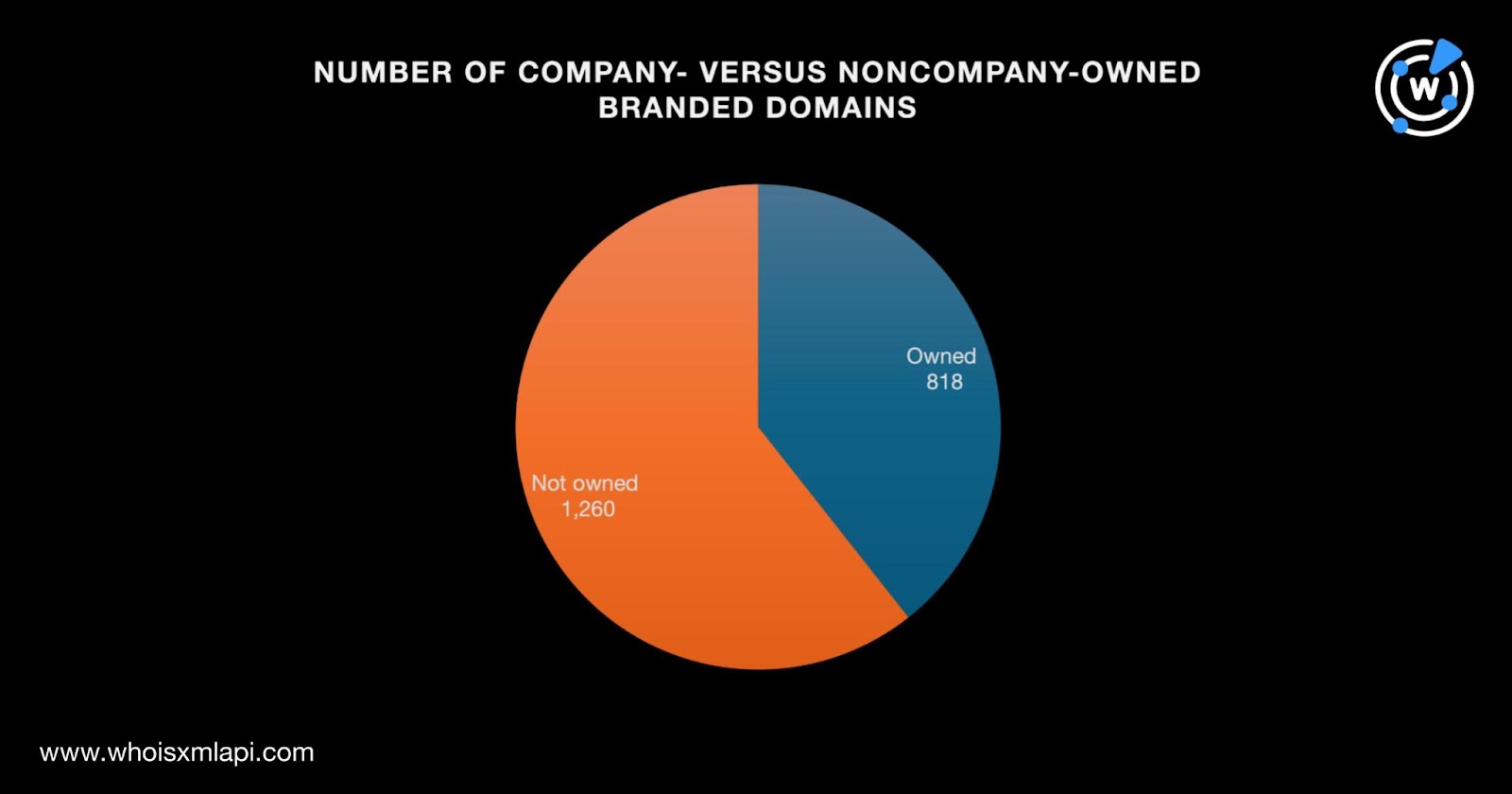
Of the 2,078 branded domains with current WHOIS record details, 818 could be publicly attributed to the 16 brand owners while 1,260 could not.
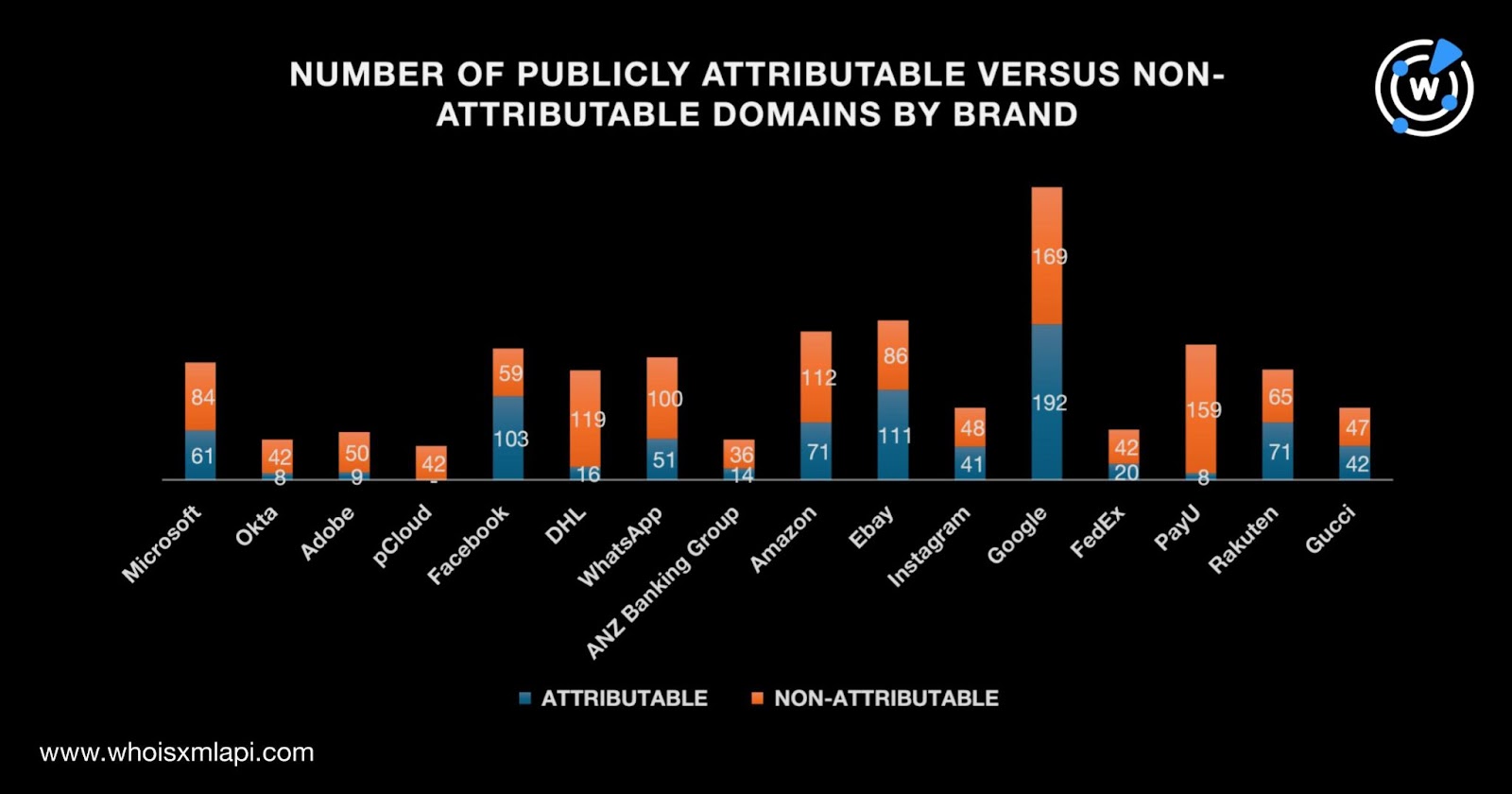
Here’s a more in-depth breakdown of the 2,078 branded domains with current WHOIS record details by brand.
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byCSC

Sponsored byDNIB.com

Sponsored byIPv4.Global

Sponsored byWhoisXML API

Sponsored byVerisign

Sponsored byRadix

Sponsored byVerisign
