


|
||
|
||
Toward the end of August 2024, a customized malware dubbed “Voldemort” based on strings found in its code was used in a cyber espionage campaign targeting various countries. The malicious code employed a relatively new mix of tools, tactics, and procedures (TTPs), including weaponized Google Sheets, government agency impersonation, and the presence of peculiar strings like “test” for filenames.
To date, the campaign is believed to have sent around 20,000 phishing emails impacting more than 70 organizations worldwide. Fellow security researchers have also identified 19 indicators of compromise (IoCs) comprising 10 subdomains and nine IP addresses.
To aid organizations with network protection, the WhoisXML API research team expanded the initial list of IoCs to identify more connected artifacts, namely:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
We began our analysis by looking for more information about the 19 IoCs.
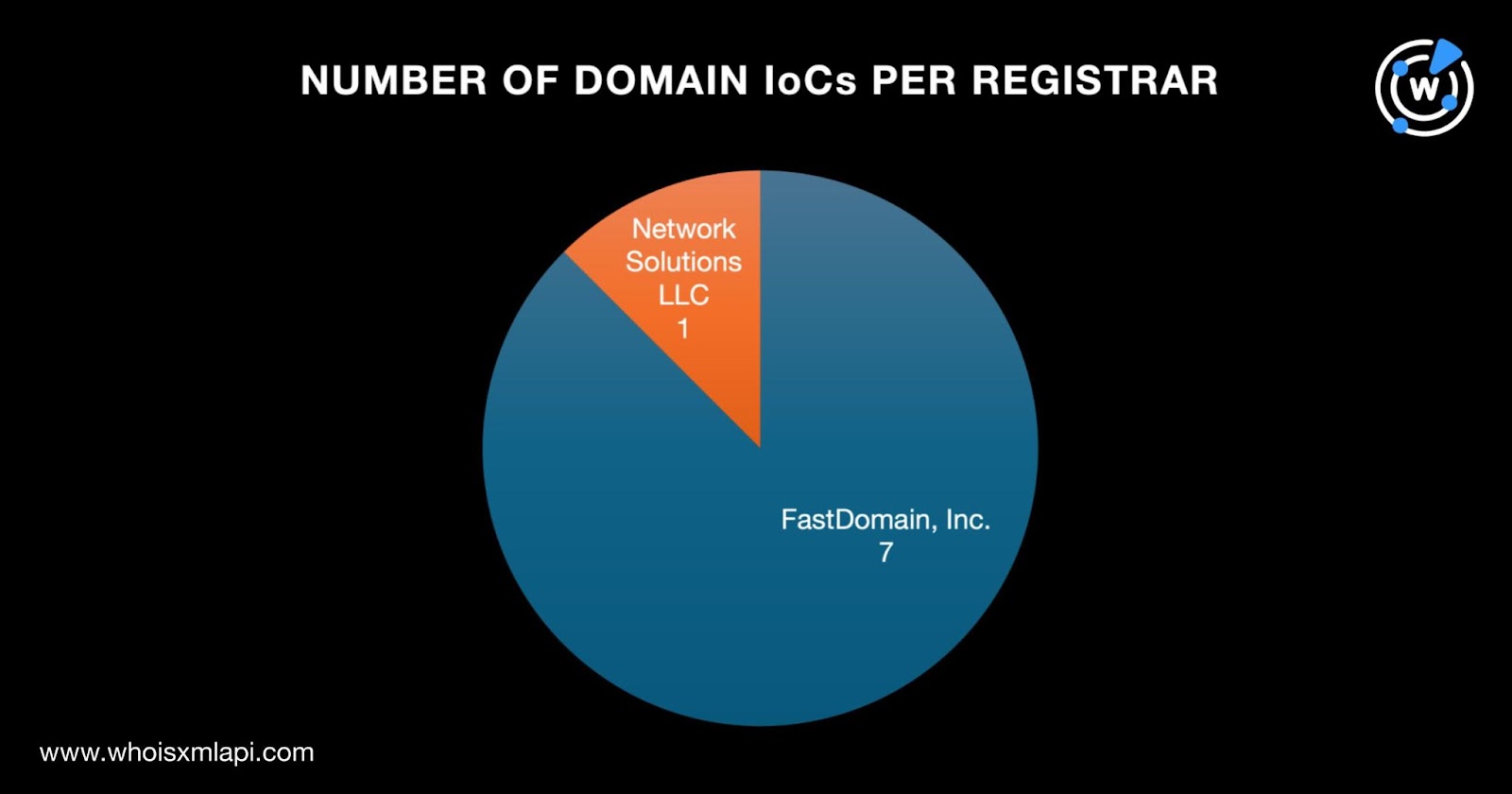
To perform a bulk WHOIS lookup, we stripped the 10 subdomains down to the domain level, which provided us with nine domains for analysis. The lookup revealed that one domain name didn’t have details in its current WHOIS record. We were thus left with eight domain IoCs for this step of the analysis.
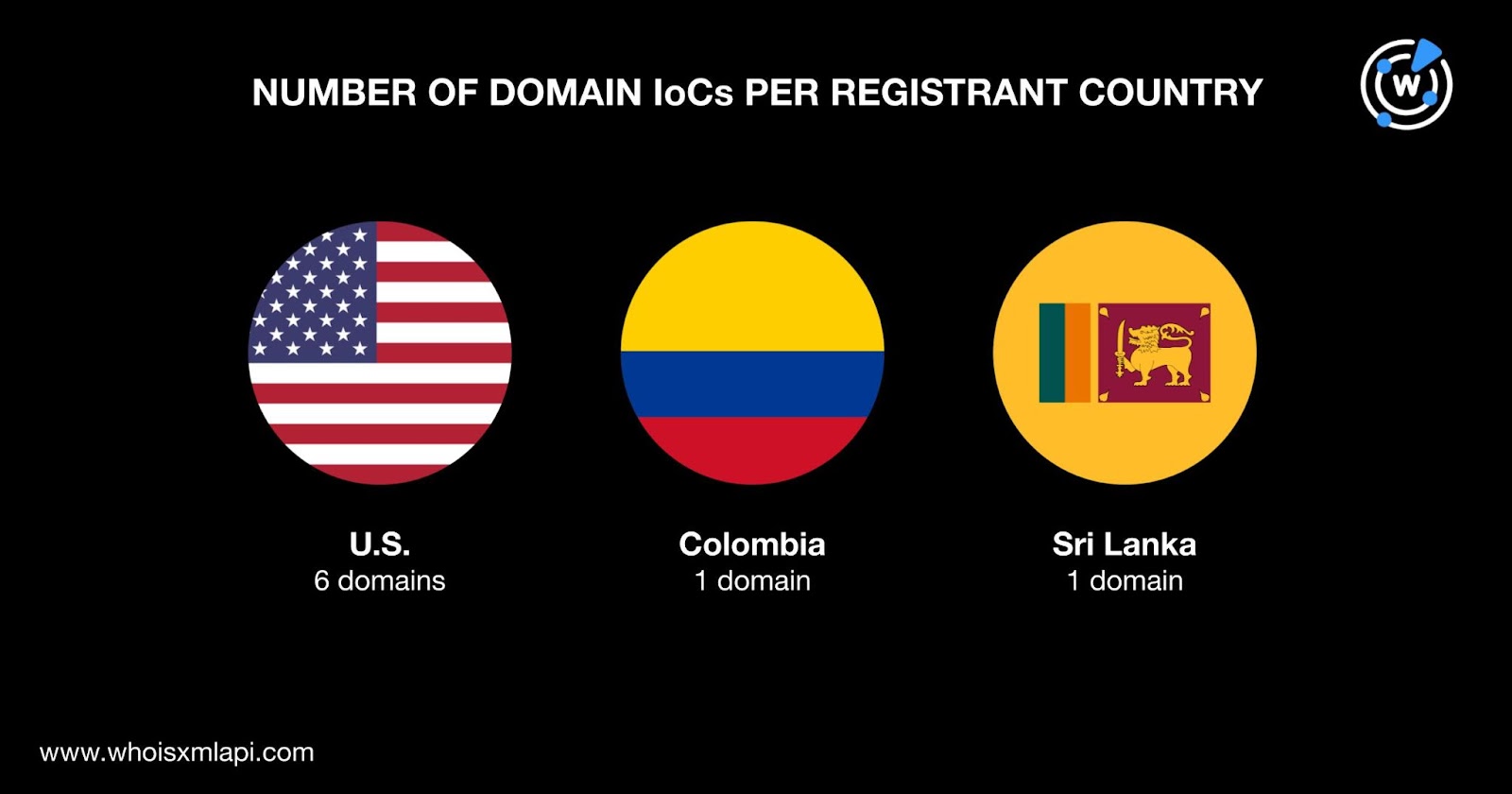
They were spread across three registrant countries led by the U.S., which accounted for six domain IoCs. One domain each was registered in Colombia and Sri Lanka.
Three of the eight domain IoCs had public registrant details, specifically:
We then performed a bulk IP geolocation lookup for the nine IP addresses and found that they were all geolocated in the U.S. and administered by Cloudflare.
We then proceeded to expand the initial IoC list starting with reverse WHOIS searches for the eight domain IoCs. We used the three registrant email addresses, three registrant names, and one registrant organization we found in the current WHOIS records of three of the domain IoCs as search terms. Our searches led to the discovery of 451 registrant-connected domains after duplicates and the IoCs were filtered out.
Next, we queried the eight domain IoCs on WHOIS History API and obtained 92 email addresses from their historical WHOIS records, 18 of which turned out to be public.
We queried the 18 public email addresses on Reverse WHOIS API. Thirteen of them were also found in the current WHOIS records of other domains. We uncovered 298 email-connected domains after filtering out duplicates, the IoCs, and the registrant-connected domains.
After that, we performed DNS lookups for the eight domain IoCs and discovered that five of them had active IP resolutions. Four of those IP addresses were not part of the initial IoC list. Threat Intelligence Lookup also showed that they were all associated with various threats.
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byWhoisXML API

Sponsored byVerisign

Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byRadix

Sponsored byIPv4.Global

Sponsored byCSC
