


|
||
|
||
Thanksgiving is right around the corner. With it, of course, come celebrations with family and friends and the biggest Black Friday sales. All seems well and good but that’s not always the case, isn’t it? Because cyber threat actors always take advantage of the biggest holidays and sales to lure more victims to their eagerly waiting traps—malicious domains and subdomains.
The WhoisXML API research team is always on the lookout for current and potential threat sources in a bid to make the Internet a safer place for all. That said, we recently took a DNS deep dive in search of domains and subdomains that could serve as attack vectors for Thanksgiving- and Black Friday-themed cyber attacks.
Our in-depth investigation led to the discovery of:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
For this study, we obtained our datasets for expansion analysis from our First Watch Malicious Domains Data Feed. We specifically searched for domains containing the text strings blackfriday and thanksgiving and uncovered a sample of 2,091 and 233 domains, respectively, as of 13 November 2024.
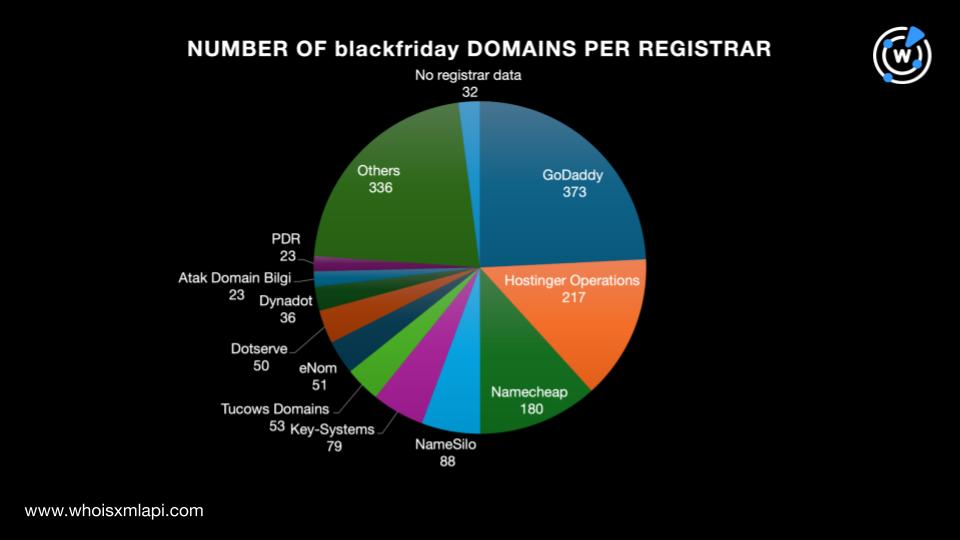
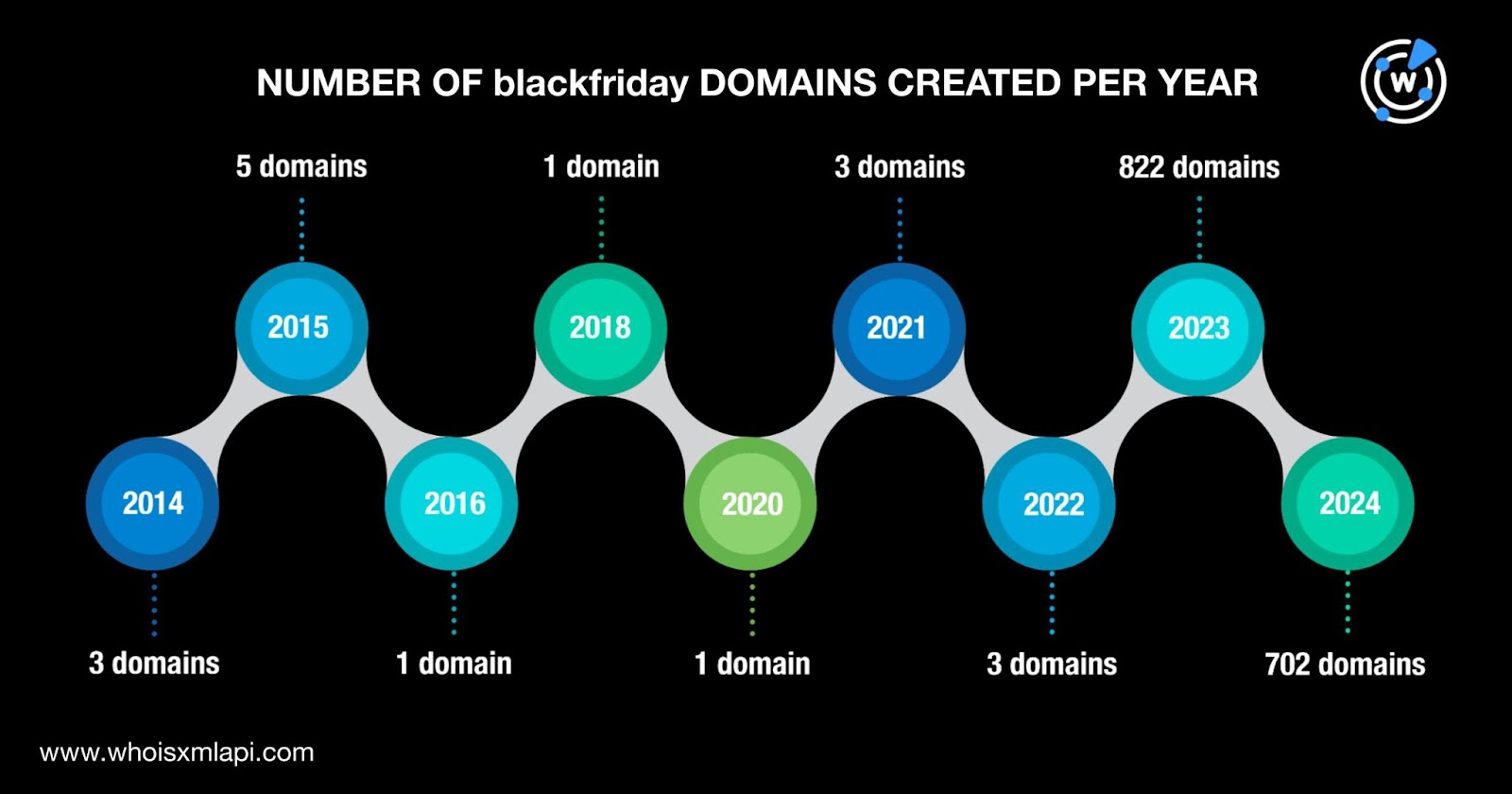
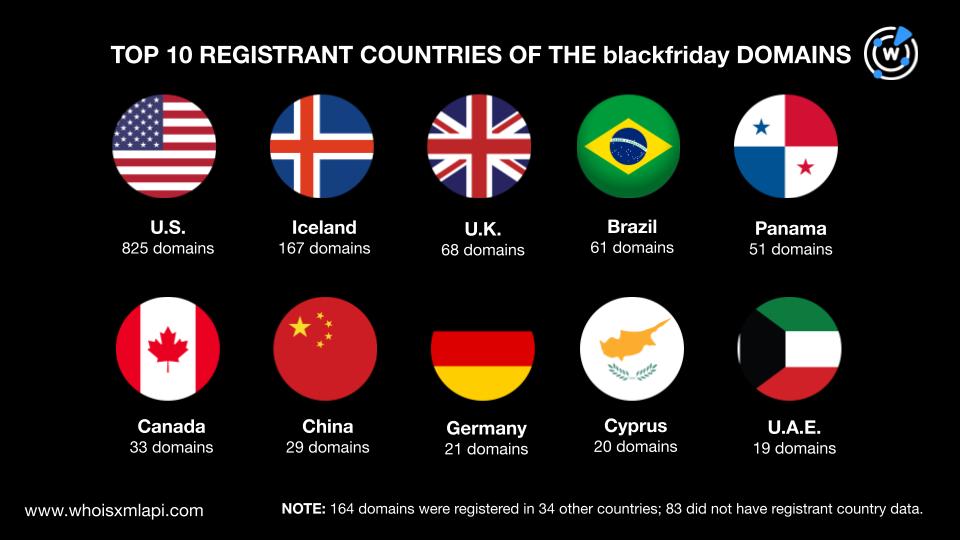
A bulk WHOIS lookup query for the 2,091 blackfriday domains showed that only 1,541 had current WHOIS records. The results for the 1,541 domains showed that:
They were created between 2014 and 2024. A majority, 99% to be exact, were fairly new, created from 2023 onward. Five domains were created in 2015; three each in 2014, 2021, and 2022; and one each in 2016, 2018, and 2020.
They were registered in 44 different countries led by the U.S., which accounted for 825 domains. The rest of the top 10 registrant countries were Iceland with 167 domains, the U.K. with 68, Brazil with 61, Panama with 51, Canada with 33, China with 29, Germany with 21, Cyprus with 20, and the U.A.E. with 19. The remaining 34 countries accounted for 11% of the total domain volume. Finally, about 5% of the domains did not have registrant country data in their current WHOIS records.
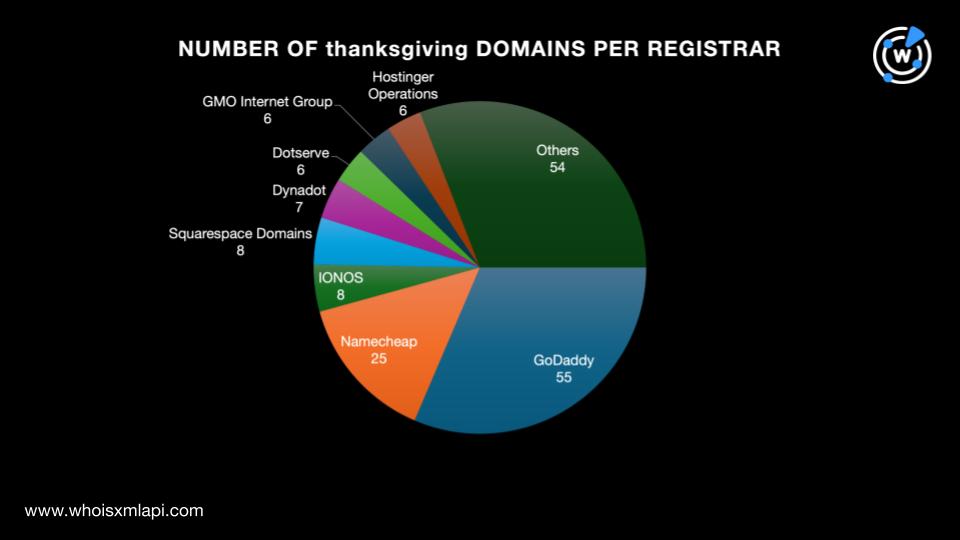
Meanwhile, a bulk WHOIS lookup query for the 233 thanksgiving domains revealed that only 175 had current WHOIS records. The results for the 175 domains showed that:
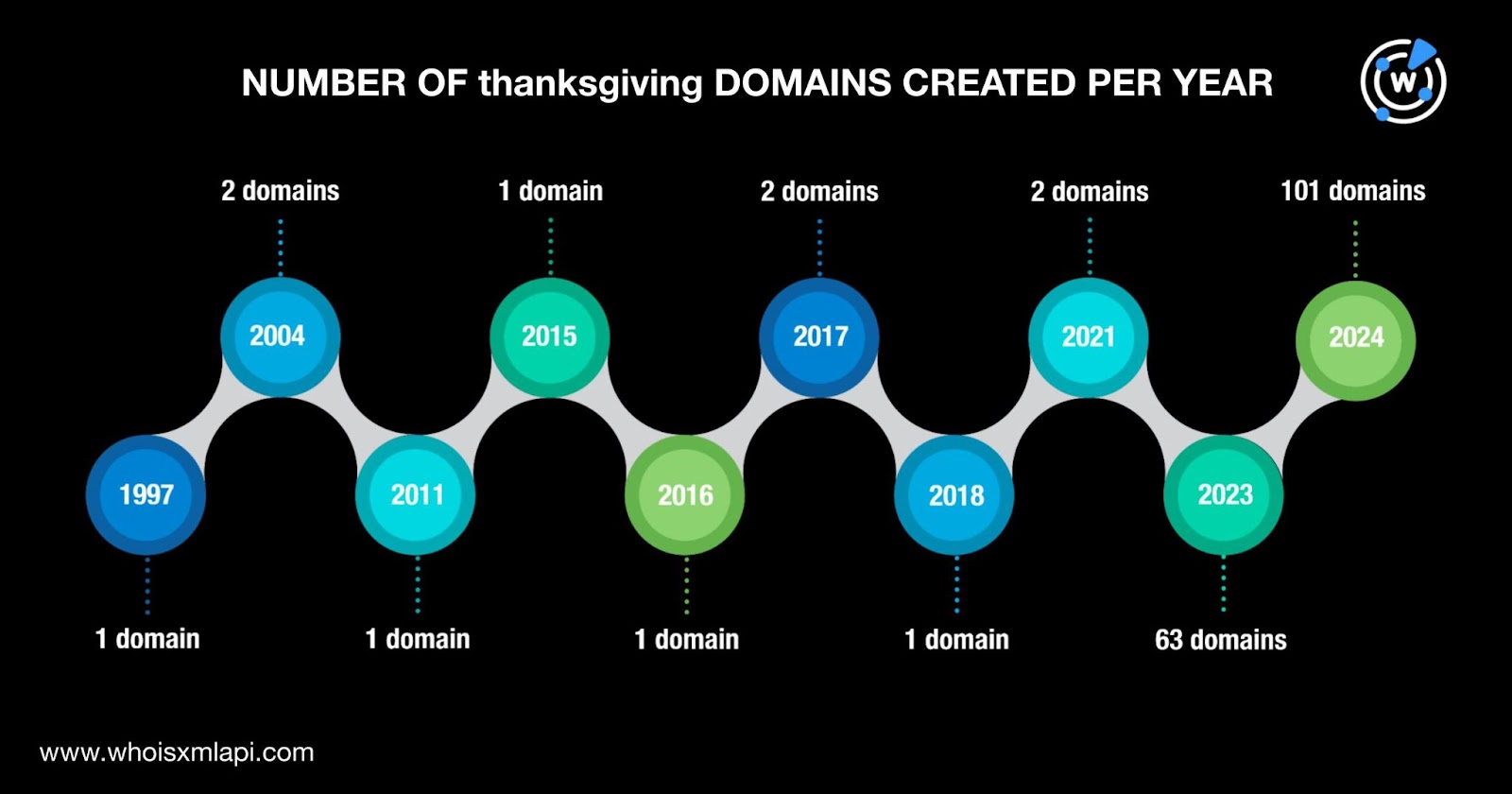
They were created between 1997 and 2024. As with the blackfriday domains, most of the thanksgiving domains, 94% to be exact, were also relatively new, created from 2023 onward. Two domains each were created in 2004, 2017, and 2021, while one each were created in 1997, 2011, 2015, 2016, and 2018.
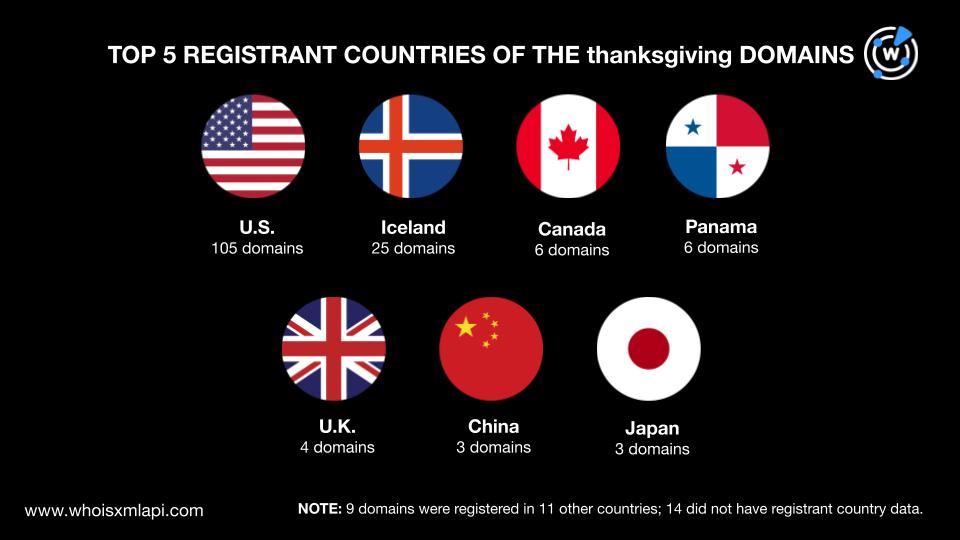
They were registered in 16 different countries led by the U.S., which accounted for 105 domains. The other countries that made it to the top 5 were Iceland with 25 domains, Canada and Panama with six each, the U.K. with four, and China and Japan with three each. The 11 remaining countries accounted for 5% of the total domain volume. Finally, 8% of the countries did not have registrant country data in their current WHOIS records.
Next, we combined all the blackfriday and thanksgiving domains, with or without current WHOIS records, ending up with a total of 2,324 domains. We queried them on Threat Intelligence API and found that four of them were associated with various threats. An example is blackfriday-best-deals[.]com, which has already been tagged as an indicator of compromise (IoC) for generic threats and phishing.
The bulk WHOIS lookups we performed earlier for the blackfriday and thanksgiving domains uncovered 219 email addresses from their current WHOIS records after duplicates were filtered out. Upon closer scrutiny, we determined that 32 of these email addresses were public.
Querying the 32 public email addresses on Reverse WHOIS API resulted in the discovery of 318 email-connected domains after duplicates and the original domains were removed. Threat Intelligence API showed that one of them—feiraochevro[.]com—was associated with a cyber attack.
DNS lookups for the 2,324 original domains with current WHOIS records revealed that they resolved to 1,250 unique IP addresses—464 IPv6 addresses and 786 IPv4 addresses. We focused on the 786 IPv4 addresses for the rest of our analysis.
Threat Intelligence API queries for the 786 IP addresses showed that 635 were associated with various threats. Take a look at five examples below.
| MALICIOUS IP ADDRESS | ASSOCIATED THREATS |
|---|---|
| 103[.]169[.]142[.]0 | AttackCommand and control (C&C)GenericMalwarePhishingSuspicious |
| 216[.]239[.]32[.]21 | AttackC&CGenericMalwarePhishingSpamSuspicious |
| 3[.]13[.]222[.]255 | GenericMalwarePhishing |
| 44[.]227[.]65[.]245 | AttackC&CGenericMalwarePhishingSuspicious |
| 51[.]91[.]236[.]255 | AttackC&CGenericMalwarePhishingSpamSuspicious |
A bulk IP geolocation lookup for the 786 IP addresses showed that:

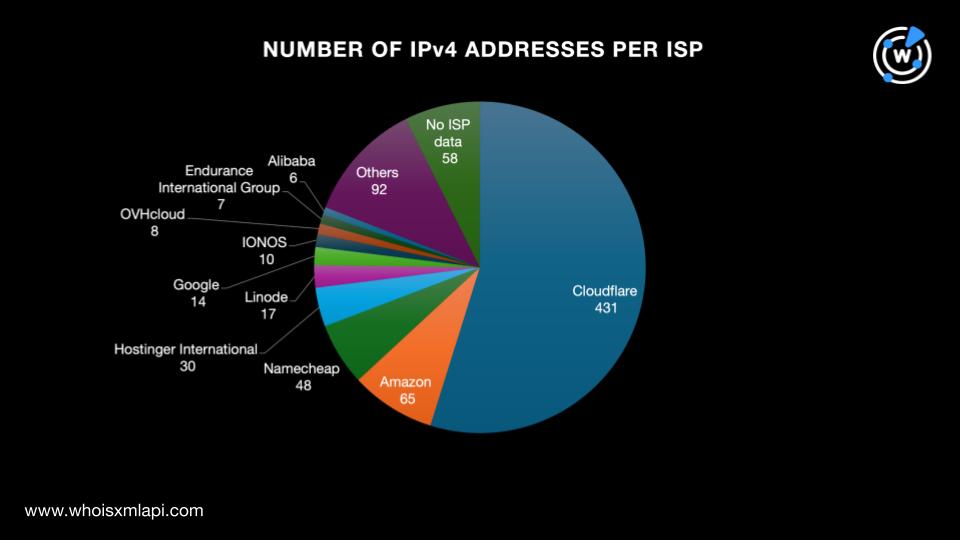
They were administered by 76 different ISPs led by Cloudflare, which accounted for 431 IP addresses. The rest of the top 10 geolocation countries were Amazon with 65 IP addresses, Namecheap with 48, Hostinger International with 30, Linode with 17, Google with 14, IONOS with 10, OVHcloud with eight, Endurance International Group with seven, and Alibaba with six. The remaining 66 ISPs accounted for 12% of the total IP address volume. Finally, 7% of the IP addresses did not have ISP data.
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byCSC

Sponsored byWhoisXML API

Sponsored byVerisign

Sponsored byIPv4.Global

Sponsored byVerisign

Sponsored byRadix

Sponsored byDNIB.com
