


|
||
|
||
 Since last fall, several waves of distributed denial of service (DDoS) attacks have targeted major players in the U.S. banking industry. JPMorgan Chase, Wells Fargo and PNC were among the first to sustain intermittent damage. Eventually, the top 50 institutions found themselves in the crosshairs. Websites crashed, customers couldn’t connect to make transactions and banks scrambled to get back online—and stay there as long as they could. In the months to come, security experts would praise the banks’ collective response, from heightened DDoS protection to candid customer communications. While the danger is hardly over, these larger institutions have learned some painful lessons that smaller firms might heed as they seek to minimize risks.
Since last fall, several waves of distributed denial of service (DDoS) attacks have targeted major players in the U.S. banking industry. JPMorgan Chase, Wells Fargo and PNC were among the first to sustain intermittent damage. Eventually, the top 50 institutions found themselves in the crosshairs. Websites crashed, customers couldn’t connect to make transactions and banks scrambled to get back online—and stay there as long as they could. In the months to come, security experts would praise the banks’ collective response, from heightened DDoS protection to candid customer communications. While the danger is hardly over, these larger institutions have learned some painful lessons that smaller firms might heed as they seek to minimize risks.
DDoS attackers are fast learners.
The attacks on banks are the work of the Cyber Fighters of Izz ad-din Al Qassam, a group claiming to protest an anti-Moslem video, though many observers believe a nation-state, possibly Iran, is responsible. To date, the attackers haven’t stolen customer data or siphoned off funds, being content to disrupt operations and get the industry’s attention.
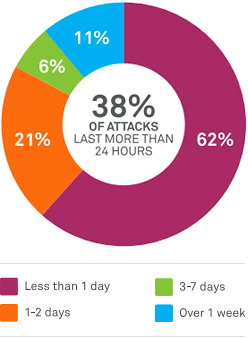 How long do DDos attacks last? 38% of ecommerce companies experienced attacks lasting more than 24 hours. 17% reported attacks lasting from 3 days to 7+ days.(Source: Neustar 2012 DDoS Survey)In doing this, they’ve launched some of the largest DDoS attacks ever, up to 150Gbps. Even more sobering, as banks have fortified defenses and sharpened DDoS responses, the attackers too have made adjustments to stay a step ahead. For example, after banks got better at defending their websites and DNS, attackers began to focus their attention on ISPs. Some attacks zeroed in on email servers and VPNs. Another adjustment: Initially, Al Qassam made voluminous requests for super-sized files like annual reports, brochures and loan applications. At 4-5 Mbps, these assets devoured outbound bandwidth. When some banks removed the files or switched to a CDN, the attackers started probing other cracks in the wall.
How long do DDos attacks last? 38% of ecommerce companies experienced attacks lasting more than 24 hours. 17% reported attacks lasting from 3 days to 7+ days.(Source: Neustar 2012 DDoS Survey)In doing this, they’ve launched some of the largest DDoS attacks ever, up to 150Gbps. Even more sobering, as banks have fortified defenses and sharpened DDoS responses, the attackers too have made adjustments to stay a step ahead. For example, after banks got better at defending their websites and DNS, attackers began to focus their attention on ISPs. Some attacks zeroed in on email servers and VPNs. Another adjustment: Initially, Al Qassam made voluminous requests for super-sized files like annual reports, brochures and loan applications. At 4-5 Mbps, these assets devoured outbound bandwidth. When some banks removed the files or switched to a CDN, the attackers started probing other cracks in the wall.
The bad guys have also seen how application-layer attacks drain human as well as computing resources, creating all-handson-deck emergencies, some lasting days or weeks. Code-red situations aren’t ideal for deploying anything, including DDoS protection hardware and mitigation procedures. The larger banks already had certain defenses in place. Smaller banks and credit unions with little or no protection would be even more hard pressed to keep pace under duress.
Al Qassam has provided a template your adversaries might use.
The very first DDoS attacks occurred in 2001, aimed at ecommerce sites like eBay and Yahoo. The tactics were later refined by the Russian Mafia, other criminal gangs and socio-political protesters, all of whom turned DDoS attacks into a kind of art form. Now Al Qassam has raised the bar again.
DDoS attackers form a nefarious community of learners, taking notes and sharing tips via, what else, the Internet. While a nation-state, for example, may not target local credit unions or regional banks, good old-fashioned cyber thieves do it every day. The scenario that worries security pros: DDoS as a distraction for payroll theft and more, used in tandem with malware like SpyEye, Zeus and Citadel. Again, the Al Qassam attackers haven’t tried to steal, but their goal is political influence, not financial gain. Criminals hitting businesses that use small to mid-sized banks, however, now have a way to distract their victims for hours on end. Imagine a DDoS attack on a bank in Somewhere, Kansas, timed for 4:45 on a Friday afternoon—just as payroll funds are whizzing through cyber-space. Sophisticated crooks are hard enough to catch when you’re focused. When you can’t confirm wire transfers because your bank’s gone dark, your chances of being defrauded increase dramatically.
With bigger and more successful attacks than anyone else to date, Al Qassam has drawn the blueprints for the ultimate cover-and-delay.
It’s easy for DDoS attackers to throw in the kitchen sink.
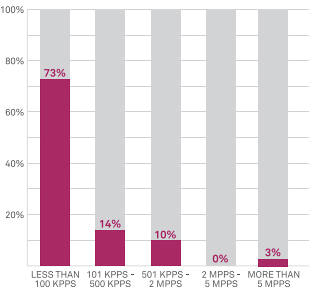 How big were DDos attacks? A 2012 Neustar survey looked at the size of Layer 3 network attacks as measured in packets per second, a standard measurement of traffic flowing through network routers. In early 2013, the news was filled with massive, high-profile DDoS attacks. The attack that shut down Spamhaus, the well-known spam tracker, was reportedly measured at 300+ Gbps. Some attacks on major banks may have reached over 150 Gbps.Exactly how big are DDoS attacks in mid-2013? “Just big enough” is what most attackers would say. Al Qassam has shown a knack for ratcheting up the volume as banks invest in greater DDoS mitigation bandwidth. The Al Qassam template hasn’t gone unnoticed. In the cyber underground, criminal gangs have chatted about the group’s favorite weapon, the “itsoknoproblembro” DDoS toolkit, which hits various parts of a website at the same time and floods servers with traffic up to 70Gbps. The Al Qassam botnet—dubbed the “brobot”—is striking too. Instead of marshalling tens of thousands of infected home computers, it uses hosting providers’ or business’ commercial content servers, which offer fatter pipes and bandwidth galore. The same tactics are available to those whose motive is greed, with the Internet itself serving as their weapons storehouse. Since they never pay for those high-capacity servers and all that power, what’s to stop attackers from using as much as they want? Though an attack of less than 2Gbps can take down many sites, attackers want to be sure your site is down throughout the world. In fact, they use free web monitoring services to make sure that folks in Chicago and Paris alike can’t reach you. If the attack isn’t working globally, the attackers up the ante. Just figuratively, though—humongous attacks cost no more to sustain than surgical strikes.
How big were DDos attacks? A 2012 Neustar survey looked at the size of Layer 3 network attacks as measured in packets per second, a standard measurement of traffic flowing through network routers. In early 2013, the news was filled with massive, high-profile DDoS attacks. The attack that shut down Spamhaus, the well-known spam tracker, was reportedly measured at 300+ Gbps. Some attacks on major banks may have reached over 150 Gbps.Exactly how big are DDoS attacks in mid-2013? “Just big enough” is what most attackers would say. Al Qassam has shown a knack for ratcheting up the volume as banks invest in greater DDoS mitigation bandwidth. The Al Qassam template hasn’t gone unnoticed. In the cyber underground, criminal gangs have chatted about the group’s favorite weapon, the “itsoknoproblembro” DDoS toolkit, which hits various parts of a website at the same time and floods servers with traffic up to 70Gbps. The Al Qassam botnet—dubbed the “brobot”—is striking too. Instead of marshalling tens of thousands of infected home computers, it uses hosting providers’ or business’ commercial content servers, which offer fatter pipes and bandwidth galore. The same tactics are available to those whose motive is greed, with the Internet itself serving as their weapons storehouse. Since they never pay for those high-capacity servers and all that power, what’s to stop attackers from using as much as they want? Though an attack of less than 2Gbps can take down many sites, attackers want to be sure your site is down throughout the world. In fact, they use free web monitoring services to make sure that folks in Chicago and Paris alike can’t reach you. If the attack isn’t working globally, the attackers up the ante. Just figuratively, though—humongous attacks cost no more to sustain than surgical strikes.
If this is bad news for top-tier banks, it’s potentially disastrous for smaller institutions lacking the budget and expertise to handle attacks themselves. Fortunately, a little planning and preparation can make a big difference.
“Does this hardware make me look fat?” It pays to be less attractive to attackers.
Short of making arrests, the good guys can’t stop the bad guys from launching DDoS attacks. So increasingly, larger banks have taken steps to become less appealing targets—less likely to go offline for long periods of time and more likely to retain customers thanks to helpful communications.
Best practice number one: distribute your Internet infrastructure. Separate your DNS, ecommerce, payment gateways and VPNs. If everything’s on the same infrastructure and you’re socked with a DDoS attack, the damage is more widespread and the attackers win. Say your DNS is hit. Not good, but if your VPN, for instance, is on a different circuit (either real or virtual), your staff has backdoor access to email and other functions. Because you’ve segregated your private and public-facing systems, business doesn’t grind to a complete halt. To accomplish this, find a trusted third party to manage infrastructure like DNS. Or at least have a Plan B, enabling you to park your DNS, VPN or web service somewhere else until the attack ends. By lining up a willing provider well in advance, you’ll spare yourself some agony when the kaka hits the fan.
It’s also smart to assume that someday you’re going to be hit. To paraphrase Trotsky, you may not be interested in DDoS, but DDoS is interested in you. With over 7,000 attacks daily, it’s only a matter of time, so more banks and credit unions are crafting emergency plans. Like natural disaster planning or certain business recovery efforts, these preparations go far beyond technical responses. It starts with being ready to do business, gasp, offline. If your credit union site is down, you may decide to extend your regular business hours, which in turn might require extra tellers and call center operators, or even coffee and cookies for customers in long lines. You’ll also need to let people know about any such contingencies. Be ready to communicate with customers quickly and reassuringly. Email may not be an option, so consider radio announcements or other media outlets, including a company web page separate from the one that’s under attack. Also think about a toll-free number your customers can call. How much detail should you reveal about the impact of an attack? That’s up to you, of course. Some financial institutions have chosen to say as little as possible, for fear of feeding attackers valuable information. Others have been more transparent, betting they’ll reap the reward in customer gratitude and fewer account defections.
Whatever procedures you develop, be sure to practice them. You’ll never be ready for anything, but executing the basics well can help enormously. Again, the throes of a crisis aren’t the best time to white-board responses. Run drills of your emergency plan and you’ll likely accomplish two things: more effective DDoS mitigation and better core service, the latter tending to slip when attacks are all-consuming.
While Al Qassam is a role model for cyber miscreants, the major banks are a more positive one in the DDoS protection arena. Smaller banks and credit unions don’t have the same deep pockets, but they can still make plans, develop responses and make smart technology investments. Inertia is the one thing they truly can’t afford.
Sponsored byIPv4.Global

Sponsored byCSC

Sponsored byVerisign

Sponsored byVerisign

Sponsored byWhoisXML API

Sponsored byRadix

Sponsored byDNIB.com
