


|
||
|
||
Phishing, despite its age and infamy, remains one of the top threats to corporate and personal networks alike. And it’s not hard to see why—it continues to be effective. In fact, more than a third of all data breaches today involve phishing.
It’s also been said that art imitates life. In the cybersecurity world, though, the opposite could also be true. So, if you think E Corp, short for “Evil Corp,” only exists in the TV show “Mr. Robot,” think again. A phishing group known as “Eevilcorp” has been wreaking havoc among organizations and individuals worldwide.
Vade’s Threat Intelligence and Response Center (TIRC) researchers analyzed what they dubbed the “Eevilcorp phishing campaign” and the malware its perpetrators used in depth. They identified nine domains and subdomains as IoCs, namely:
WhoisXML API researchers expanded the published list of IoCs and uncovered:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
The Vade TIRC researchers discovered that Eevilcorp trailed its sights on at least two big tech products—Microsoft Outlook and Adobe Document Cloud. They also abused the glitch[.]me platform to host seven of their specially crafted subdomains and used two other domains for their ongoing campaign.
We first subjected the nine web properties identified as IoCs to a bulk WHOIS lookup and found that only two had available WHOIS records—eevilcorp[.]online and ultimotempore[.]online. Both were administered by Hostinger Operations, UAB and had redacted WHOIS records, protected by Privacy Protect, LLC. They were relatively newly created, specifically in the first two months of this year and registered in the U.S.
Website categorization lookups for all nine domains also revealed interesting findings shown in the table below.
| DOMAIN | WEBSITE CATEGORIZATION LOOKUP RESULT |
|---|---|
| eevilcorp[.]online | Phishing and other fraud |
| ultimotempore[.]online | Phishing and other fraud |
| periodic-checker[.]glitch[.]me | Phishing and other fraud |
| scan-verified[.]glitch[.]me | Phishing and other fraud |
| transfer-with[.]glitch[.]me | Phishing and other fraud |
| air-dropped[.]glitch[.]me | Phishing and other fraud |
| precise-share[.]glitch[.]me | Phishing and other fraud |
| monthly-payment-invoice[.]glitch[.]me | Phishing and other fraud |
| monthly-report-check[.]glitch[.]me | Phishing and other fraud |
In an effort to determine if organizations and individuals need to steer clear of web properties other than those that have already been identified as Eevilcorp IoCs, we expanded the current list aided by DNS intelligence.
In total, the IoCs resolved to nine unique IP addresses. Only eight of them, however, had retrievable A records based on a bulk IP geolocation lookup. The result also revealed that four were administered by Amazon and the remaining half by Cloudflare. All of the resolving IP addresses were geolocated in the U.S.
We subjected the IoCs to DNS lookups as well, which revealed that many, particularly those hosted on glitch[.]me, used the same four shared IP hosts—3[.]212[.]249[.]142, 44[.]198[.]62[.]156, 54[.]144[.]28[.]217, and 54[.]235[.]167[.]164.
The remaining four IP addresses were possibly dedicated based on reverse IP lookups, hosting 579 domains in total not on the published list of IoCs. A bulk malware check for the IP-connected domains showed that 13 were malicious.
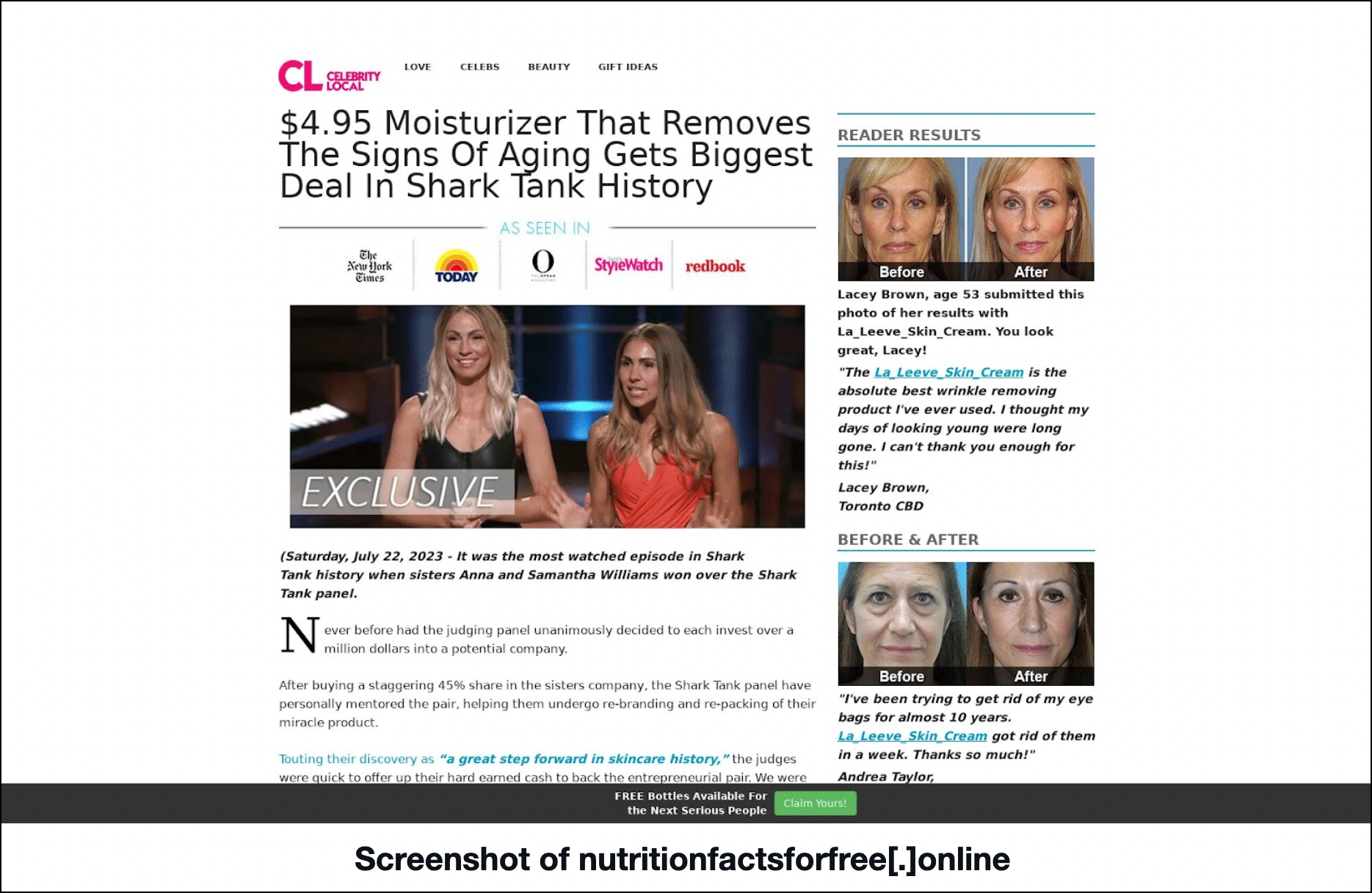
Five of the 13 malicious domains continued to host live content as evidenced by screenshot lookup results. Two of them proved most interesting in that apart from being detected as malware hosts, their content didn’t match what their domain names suggested.
First off, nutritionfactsforfree[.]online hosted what looked like a celebrity news site. Perjakatoto[.]net (perjakatoto is Malay for “girl”) and vldb2009[.]org, meanwhile, led to gambling sites.


The malicious domain personal-loan-look-seeks[.]today was, on the other hand, truer to its name, as it contained a list of loan-related searches.

Next, given the attackers’ abuse of popular brands owned by Microsoft and Adobe, we also sought to uncover if they could potentially weaponize other domains and subdomains for future campaigns.
Domains & Subdomains Discovery for domains starting with and subdomains containing microsoft + outlook led to the discovery of 20 domains and 715 subdomains created just this year. A similar search for domains starting with and subdomains containing adobe + document + cloud, meanwhile, turned up 11 domains and 15 subdomains.
A bulk WHOIS lookup for all the domains we uncovered showed none of them could be publicly attributed to Microsoft and Adobe. None of them shared the registrant email address and other WHOIS details of microsoft[.]com and adobe[.]com.
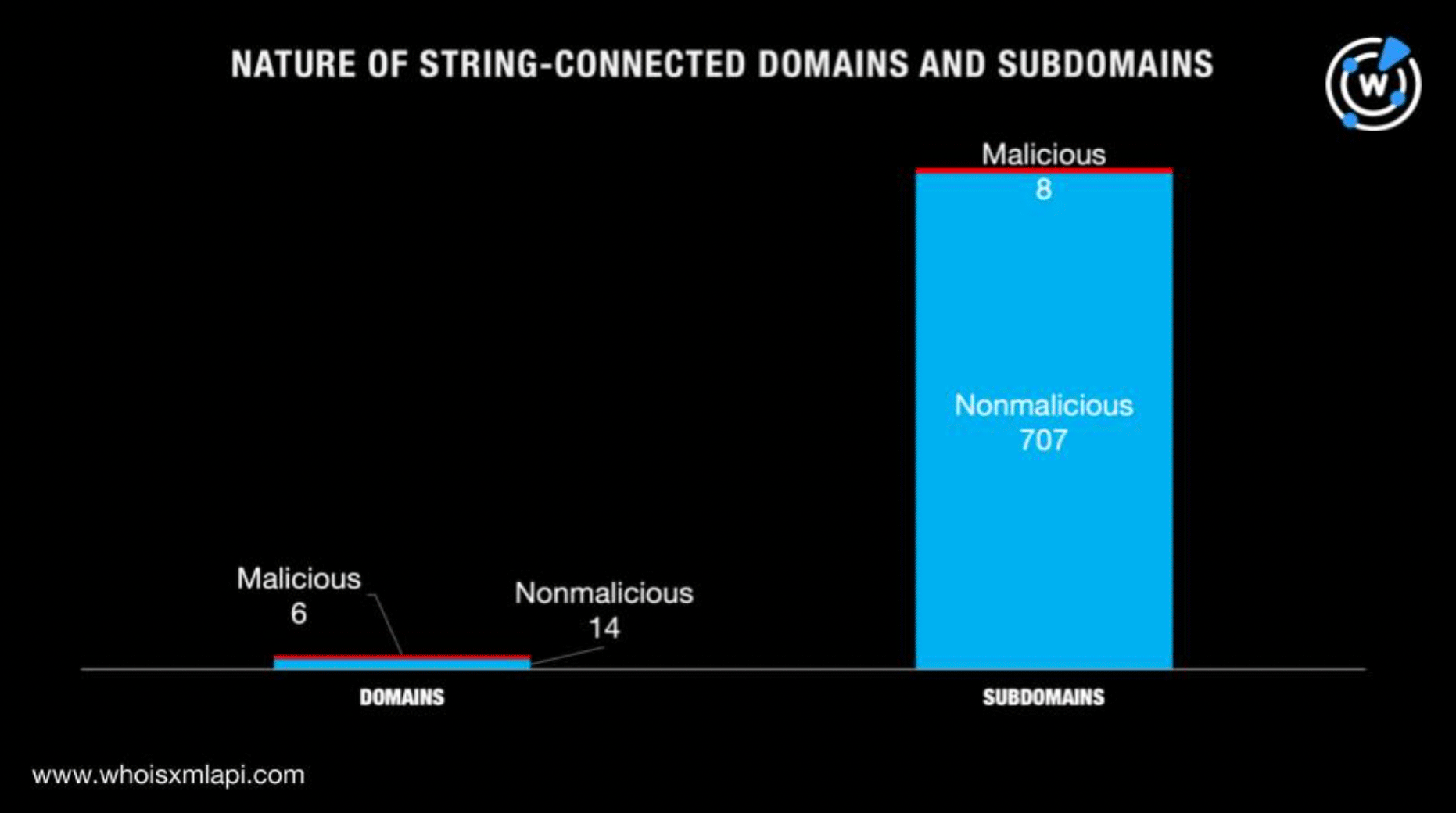
A bulk malware check for string-connected domains, on the other hand, revealed that six of them were categorized as malicious. While a majority of them were unreachable, one domain led to a site that was, according to its screenshot, under development.
We also subjected the string-connected subdomains to a bulk malware check, which revealed that eight of them have been detected as malware hosts. Only three of them remained accessible—one led to a blank page while two showed error pages.
Our latest foray into the depths of the DNS allowed us to find more digital traces Eevilcorp may have unintentionally left behind. The IoC expansion we performed brought to light more than 1,300 connected properties. Directly related or not to the group’s ongoing phishing campaign, the 27 malicious properties we found could pose risks to organizations and individuals alike.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byWhoisXML API

Sponsored byCSC

Sponsored byVerisign

Sponsored byRadix

Sponsored byIPv4.Global
