


|
||
|
||
Cybercriminals are known for using so-called “loaders” like Xloader to initiate computer infections. Worse, even newbies can now get their hands on these malware distributors via hacker forums. Case in point? JinxLoader, one of the latest malicious offerings up for grabs on the likes of hackforums[.]net.
Palo Alto’s Unit 42 published 19 JinxLoader indicators of compromise (IoCs) comprising 18 domains and one IP address in late November 2023. The WhoisXML API research team sought to determine if the JinxLoader operators left more digital traces through a DNS deep dive that brought to light:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
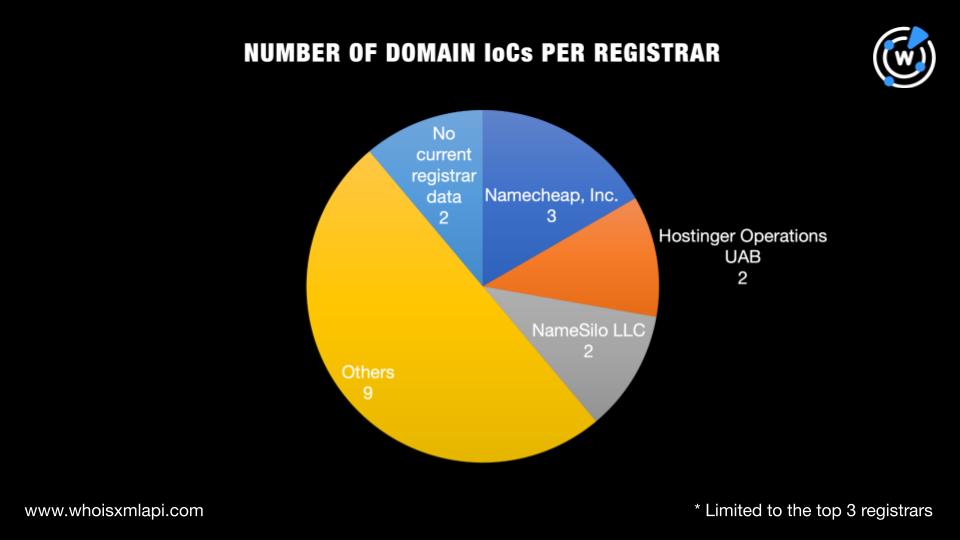
As with every investigation, we sought to discover more about the 21 JinxLoader IoCs starting with a bulk WHOIS lookup for the 18 domains that led to these findings:
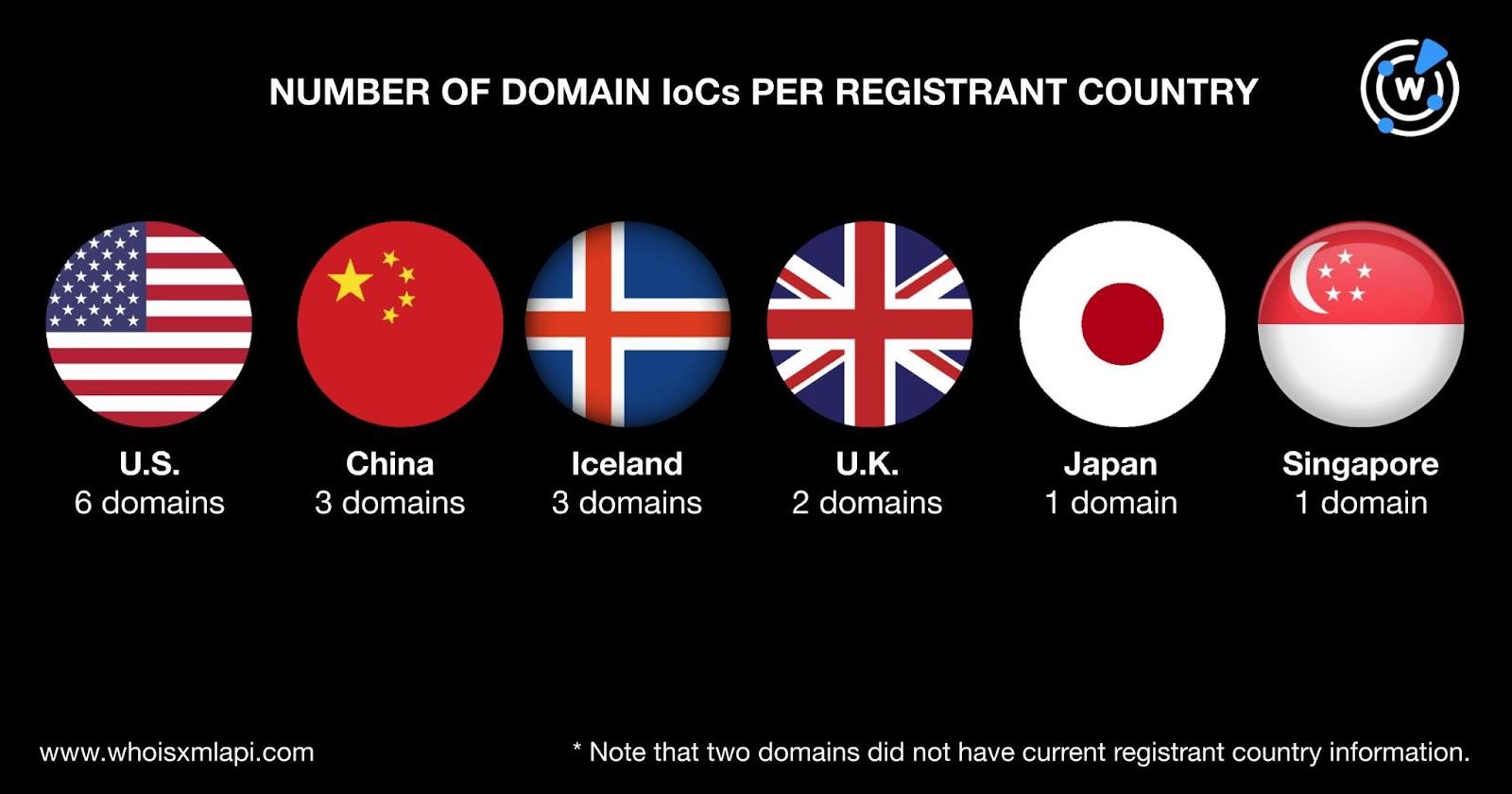
The 18 domains were spread across six registrant countries topped by the U.S., which accounted for six of them. China and Iceland took the second spot with three domains each while the U.K. with two domains placed third. Japan and Singapore accounted for one domain each. Finally, two did not have current registrant country information.
An IP geolocation lookup, meanwhile, for the IP address classified as an IoC showed it was geolocated in Japan with Alibaba (U.S.) Technology Co. Ltd. as its ISP.
We began our search for JinxLoader traces in the DNS with WHOIS History API searches for email addresses. We found 41 results after duplicates and the IoCs were removed. Seven of the email addresses were public.
Reverse WHOIS API searches showed that three of the public email addresses appeared in the current WHOIS records of 314 other domains after duplicates and the IoCs were filtered out.
Screenshot API searches for the 314 email-connected domains revealed that 115 remained accessible to date.
Next, we subjected the 18 domain IoCs to DNS lookups, which showed that 17 actively resolved to 26 IP addresses after duplicates and the IoC were removed.
IP geolocation lookups for the 26 additional IP addresses led to these findings:

Note that Japan, an IP address IoC geolocation country, also appeared as an origin of one additional IP address.
Threat intelligence lookups for the 26 additional IP addresses revealed that 14 were associated with various threats. Take a look at the detailed results for five of them below.
| IP ADDRESSES | ASSOCIATED THREAT TYPES |
|---|---|
| 103[.]107[.]239[.]13 | Malware |
| 118[.]27[.]125[.]154 | Malware |
| 154[.]215[.]150[.]218 | Malware |
| 162[.]0[.]235[.]58 | Generic Malware Phishing |
| 162[.]255[.]119[.]78 | Malware |
Reverse IP lookups for the 26 additional IP addresses showed that five of them could be dedicated. They hosted 158 unique domains that were not part of the list of IoCs or email-connected domains.
Threat Intelligence API, meanwhile, revealed that one—echolinkevolve[.]xyz—was seemingly associated with malware distribution.
Screenshot API showed that 72 of the 158 IP-connected domains remained accessible. It is also worth noting that 12 of them looked quite suspicious—brightpathtechgroups[.]top, frontiersunrisepro[.]life, greensagesstrategies[.]top, ivisas-affaires[.]com, mailerpay[.]com, matrixleapsystems[.]xyz, nexusglobalfusions[.]top, oceanicpulsetek[.]xyz, pbc-finance[.]com, solarflaredisruptors[.]life, trebletech[.]xyz, and visionquestengage[.]life—in that they shared the same content as malicious IP-connected domain echolinkevolve[.]xyz.
To cover all our bases, we used Domains & Subdomains Discovery with the Starts with parameter to look for other possibly connected domains, specifically those containing text strings found among the IoCs. We uncovered 1,116 such properties for eight strings, namely:
Threat Intelligence API showed that one string-connected domain—worldlifefree[.]info—was associated with malicious command-and-control (C&C) and malware distribution.
Screenshot API, meanwhile, showed that 472 of the 1,116 string-connected domains remained accessible as of this writing.
Our foray into the DNS for more signs of JinxLoader led to the discovery of 1,588 potentially connected artifacts. We also uncovered 26 additional IP addresses that played host to the domain IoCs, several of which turned out to be malicious. A couple of the connected domains were also associated with various threats.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byWhoisXML API

Sponsored byVerisign

Sponsored byIPv4.Global

Sponsored byCSC

Sponsored byVerisign

Sponsored byRadix

Sponsored byDNIB.com
