


|
||
|
||
RisePro, a malware-as-a-service data stealer, has been plaguing users since 2022. ANY.RUN recently discovered and analyzed its latest version in great depth and identified 10 indicators of compromise (IoCs)—three domains and seven IP addresses.
In a bid to make the Internet safer and more transparent, the WhoisXML API research team expanded the current IoC list to find other connected threat artifacts. Our comprehensive DNS intelligence sources found:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
We began our analysis by looking more closely at the RisePro IoCs.
A bulk WHOIS lookup for the three domains identified as IoCs led to these discoveries:
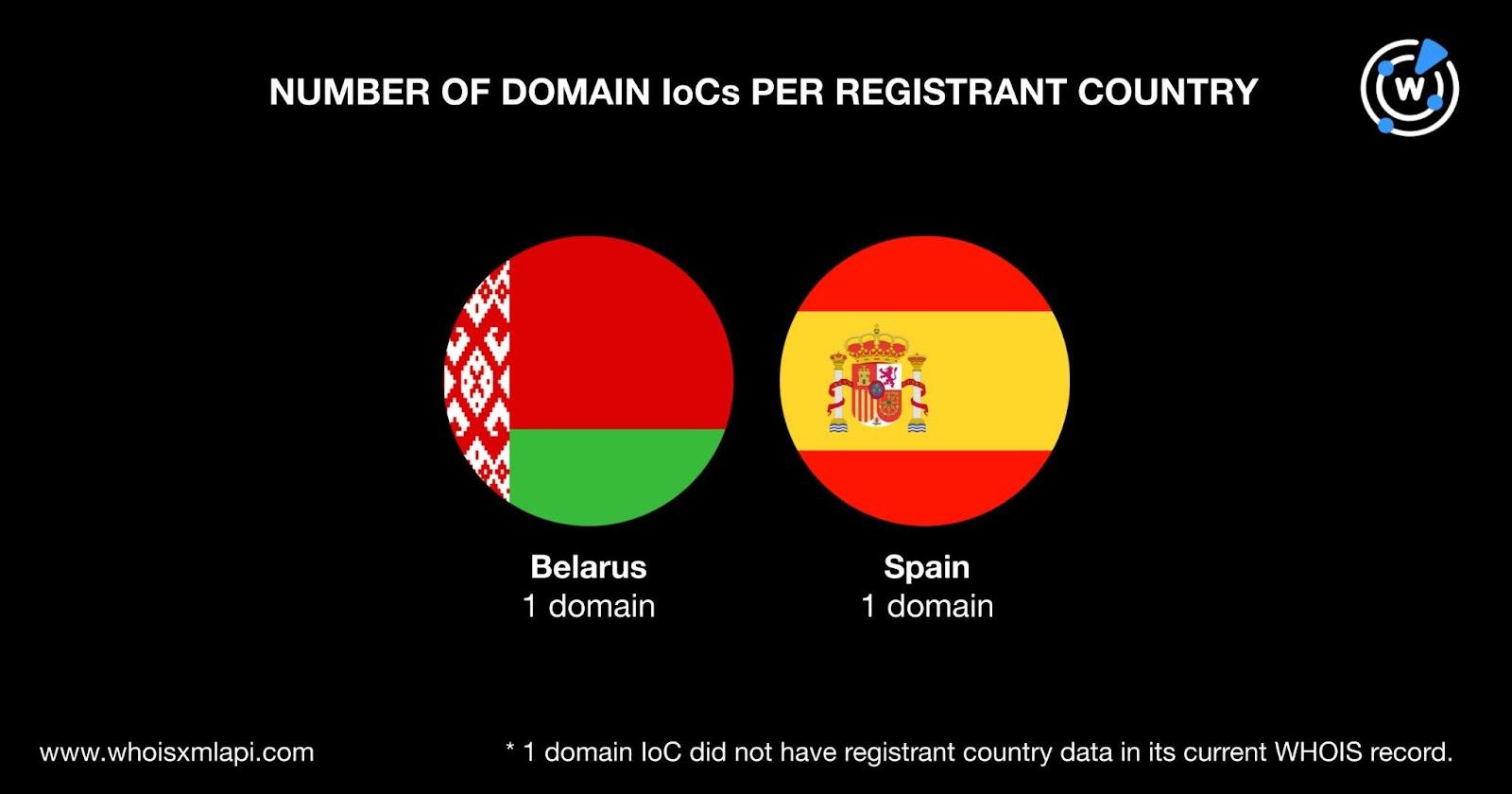
Only two of the domains had registrant countries in their current WHOIS records—ads-strong[.]online was supposedly created in Belarus and ontopothers[.]com in Spain.
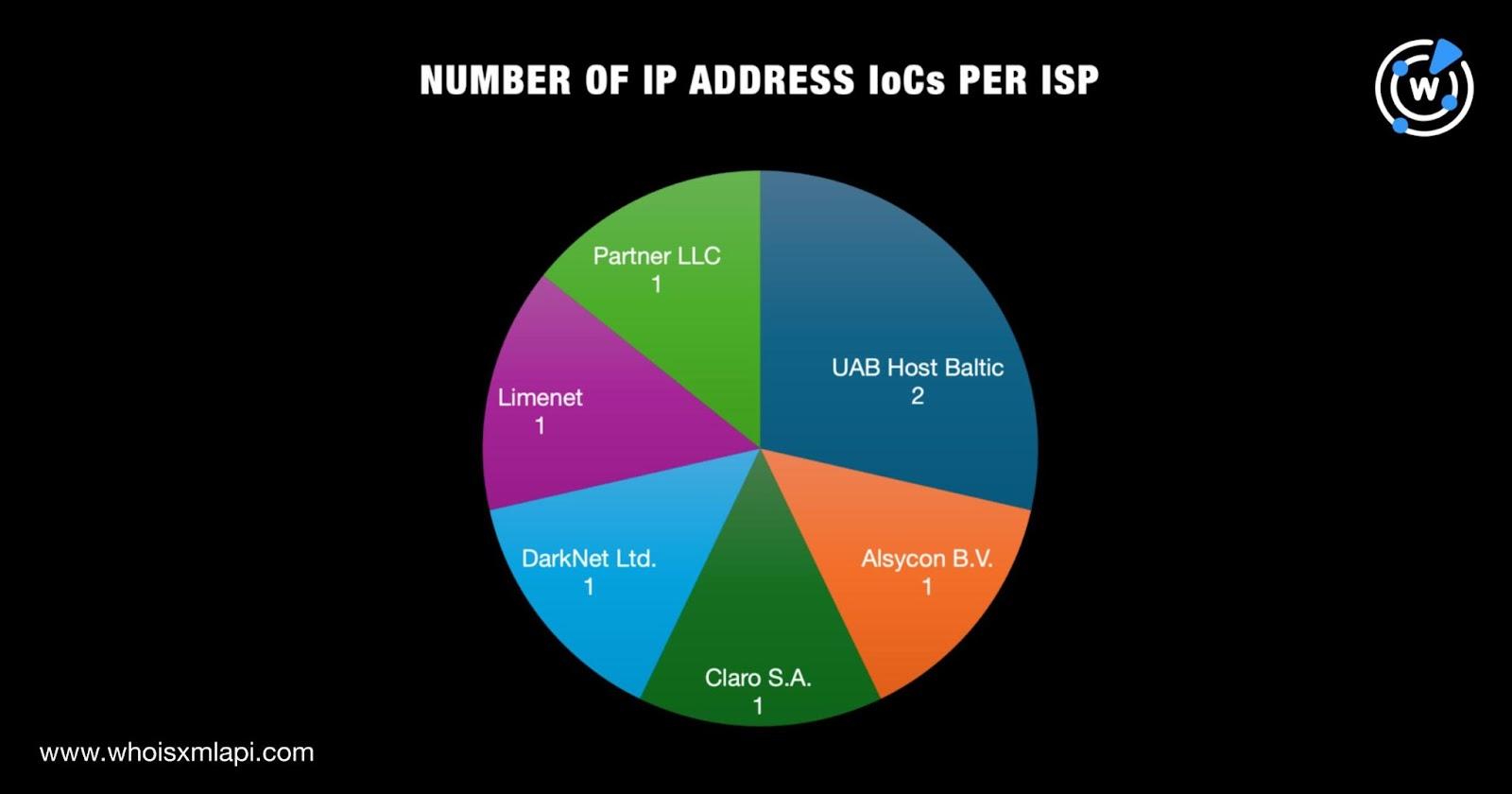
A bulk IP geolocation lookup for the seven IP addresses tagged as IoCs, meanwhile, led to these findings:

They were administered by six ISPs led by UAB Host Baltic, which accounted for two IP addresses. One IP address each was administered by Alsycon B.V., Claro S.A., DarkNet Ltd., Limenet, and Partner LLC.
To find other connected artifacts, we first looked for email addresses in the historical WHOIS records of the three domains identified as IoCs using WHOIS History API. Our search turned up one unredacted email address.
A Reverse WHOIS API query for the single unredacted email address led to the discovery of 849 email-connected domains after duplicates and those already identified as IoCs were removed.
Threat Intelligence API showed that 52 of them were associated with malware distribution, phishing, or generic attacks. Take a look at the detailed results for five malicious email-connected domains below.
| EMAIL-CONNECTED DOMAIN | ASSOCIATED THREAT TYPE |
|---|---|
| aavenetworks[.]com | Phishing |
| confirmation-setup[.]com | Malware |
| dao-aave[.]com | Phishing |
| jatep-raw[.]net | Malware |
| santander-odnowienie[.]com | Generic |
It’s also interesting to note that several of the email-connected domains could be used to target banks, cryptocurrency exchanges, postal service providers, social networks, email service providers, and tech giants, especially since none of them could be publicly attributed to the banks based on WHOIS record detail comparisons. Take a look at detailed WHOIS Lookup result comparisons for five potential typosquatting domains below.
| MIMICKED BANK | LEGITIMATE DOMAIN | TYPOSQUATTING DOMAIN | WHOIS RECORD DETAIL | |
|---|---|---|---|---|
| LEGITIMATE DOMAIN | TYPOSQUATTING DOMAIN | |||
| facebook[.]com | facebook-secured[.]com | Registrant organization: Meta Platforms, Inc. | Registrant organization: No data | |
| Gmail | gmail[.]com | gmail-sakerhet[.]com | Registrant organization: Google LLC | Registrant organization: Sahari Muti, Inc. |
| Microsoft | microsoft[.]com | microsoftsupdates-live[.]com | Registrant organization: Microsoft Corporation | Registrant organization: No data |
| HSBC | hsbc[.]com | livechathsbc[.]net | Registrant organization: HSBC | Registrant organization: Sahari Muti, Inc. |
| DHL | dhl[.]com | post-dhl-server[.]com | Registrant organization: Deutsche Post AG | Registrant organization: No data |
Next, we subjected the three domains classified as IoCs to DNS lookups that gave us two additional IP addresses not included in the current IoC list.
IP geolocation lookups for the two additional IP addresses revealed that:
Threat Intelligence API also showed that 62[.]204[.]41[.]98 was associated with cyber attacks, generic threats, malware distribution, and spam campaigns.
Reverse IP lookups for the nine IP addresses (IoCs and additional IP resolutions combined) showed that only two could be dedicated—62[.]204[.]41[.]98 and 82[.]165[.]193[.]159. Altogether, they hosted 59 domains after duplicates, those already tagged as IoCs, and those that were email-connected were filtered out.
Threat Intelligence API revealed that 18 of the IP-connected domains were associated with malware distribution. The text string ads- appeared in all of them, which could hint at their use in malvertising campaigns specifically.
To cover all our bases, we searched for other domains that contained these text strings found among two domains identified as IoCs:
Domains & Subdomains Discovery searches using the Starts with parameter provided us with 14 string-connected domains.
Our in-depth analysis of the RisePro IoCs led to the discovery of 924 connected artifacts comprising 922 domains and two IP addresses. Note, too, that 71 of them were associated with various threats. Several email-connected domains could also be weaponized (if they haven’t been already) for attacks targeting banks, cryptocurrency exchanges, postal service providers, social networks, email service providers, and tech giants.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byRadix

Sponsored byVerisign

Sponsored byWhoisXML API

Sponsored byIPv4.Global

Sponsored byDNIB.com

Sponsored byCSC

Sponsored byVerisign
