


|
||
|
||
New kids on the cybercrime block, pig butchering scams, have been making waves lately, and it is not surprising why. Scammers have been earning tons from them by being able to trick users into investing in seemingly legitimate business ventures but losing their hard-earned cash instead.
Trend Micro recently published an in-depth analysis of pig butchering scams and named eight domains as indicators of compromise (IoCs) in the process. These domains supposedly belonged to investment brokers who were really scammers in disguise.
The WhoisXML API research team, in a bid to uncover other unknown threat vectors, expanded the list of pig butchering scam IoCs and found:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
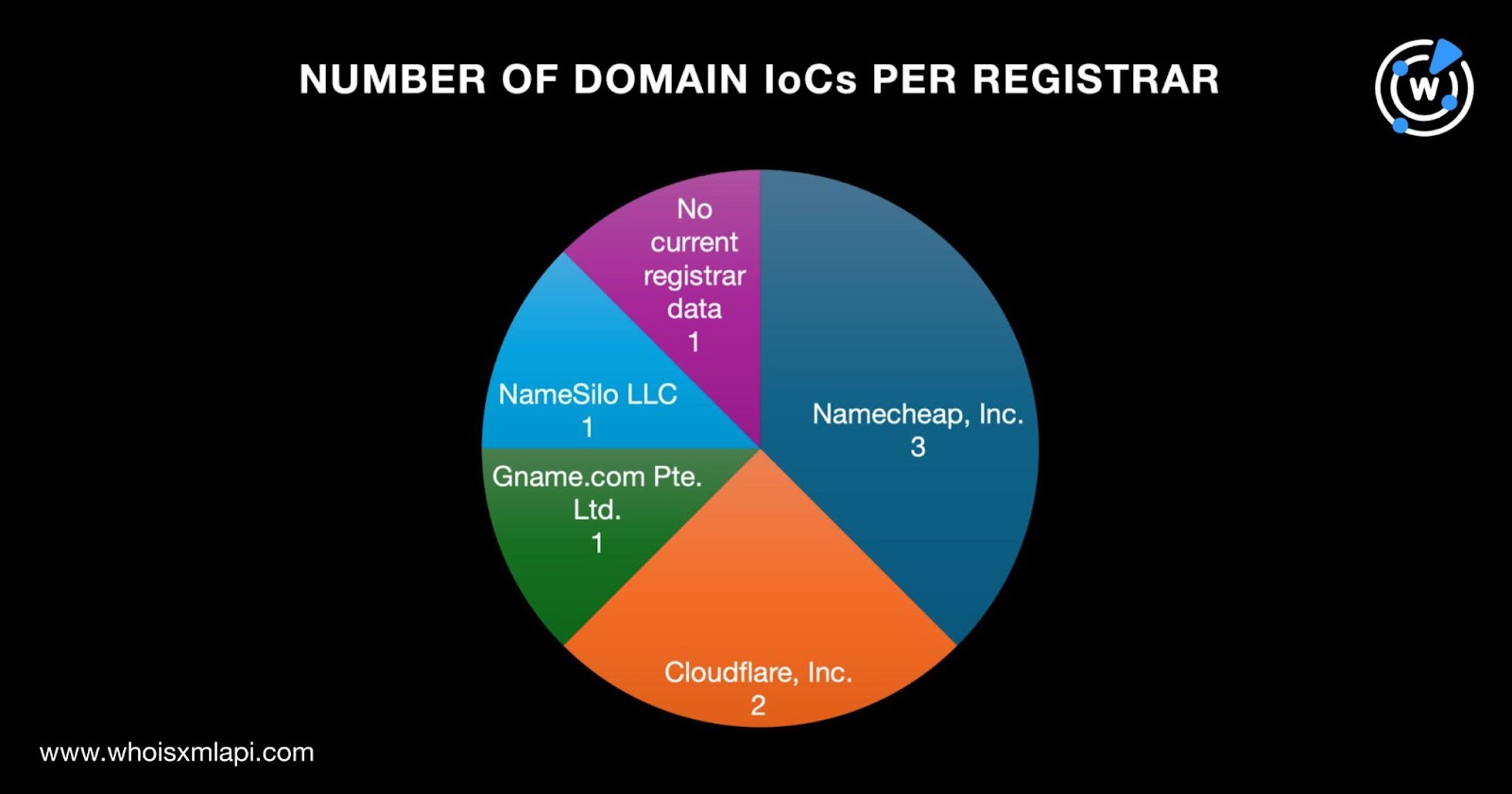
As the usual first step in our analysis, we sought to find more information about the eight domains identified as IoCs. A bulk WHOIS lookup for them led to these findings:
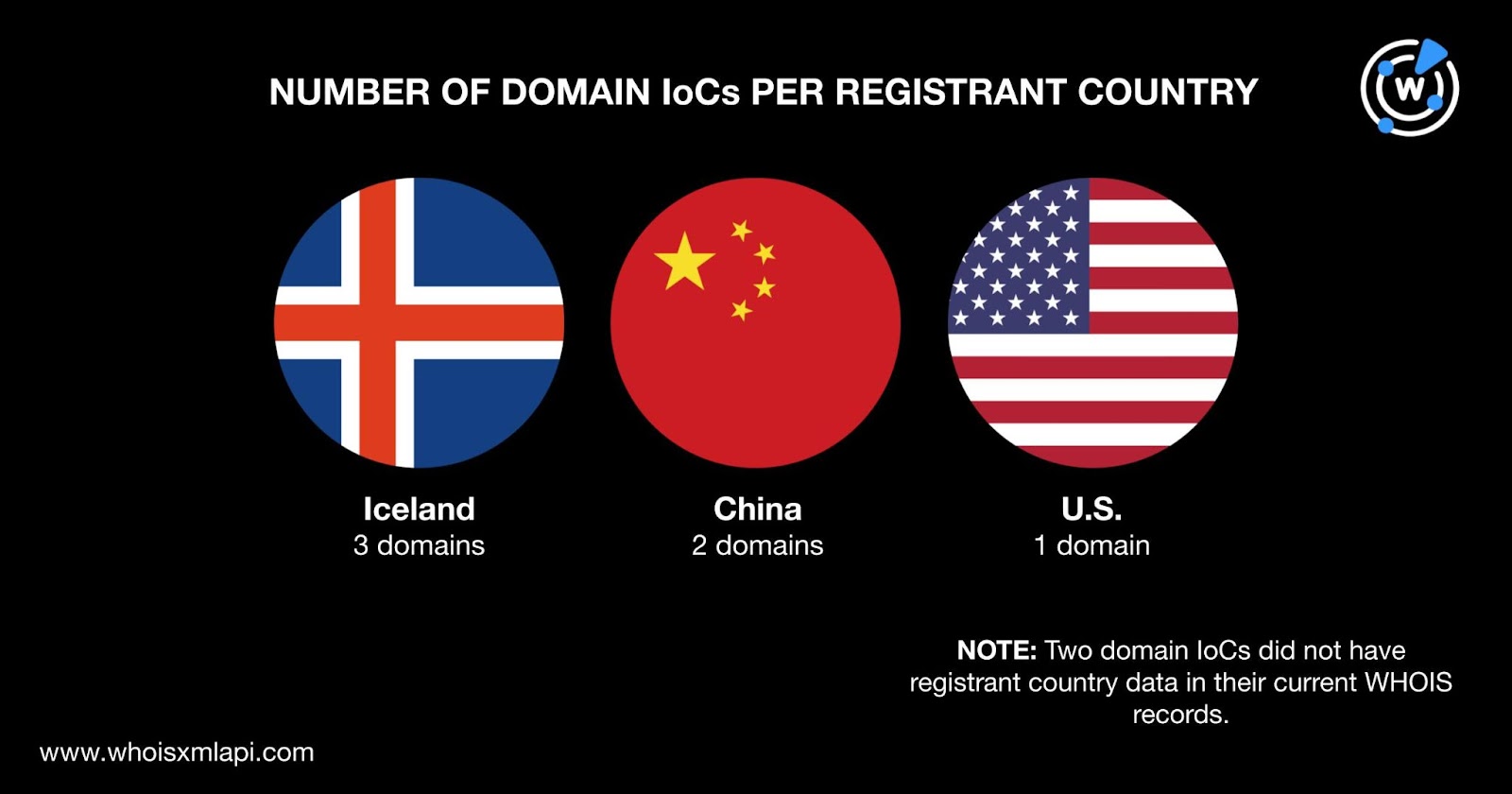
They were registered in three different countries led by Iceland, which accounted for three domain IoCs. Two domain IoCs were registered in China and one in the U.S. Two domain IoCs did not have registrant country data in their current WHOIS records.
To uncover pig butchering scam digital breadcrumbs, we began our expansion analysis with WHOIS History API queries for the eight domains identified as IoCs. They allowed us to gather eight email addresses from the domain IoCs’ historical WHOIS records. One of the email addresses was public.
A Reverse WHOIS API query for the public email address led to the discovery of 27 email-connected domains after duplicates and the IoCs were removed.
Threat Intelligence API queries for the email-connected domains showed that one—designalps[.]com—figured in a phishing campaign.
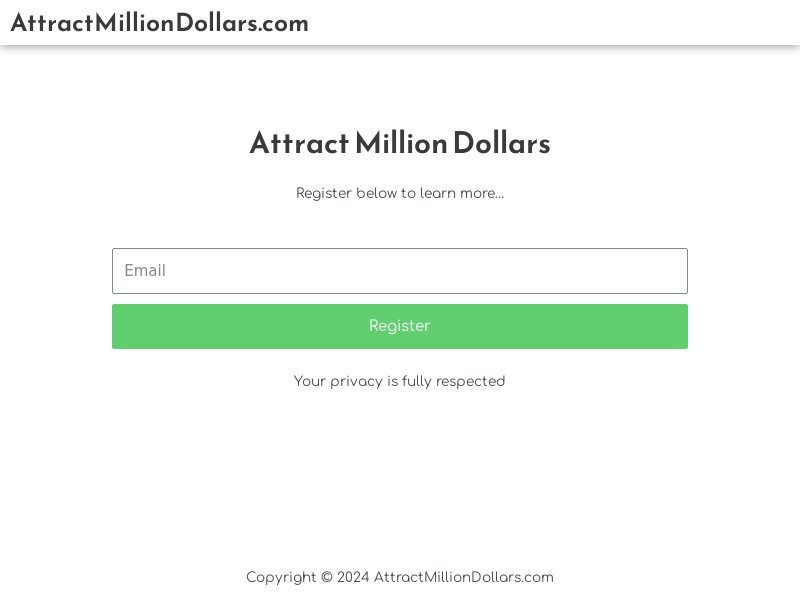
While designalps[.]com was no longer accessible, Screenshot API revealed that 21 of the email-connected domains continued to resolve to live pages. Twelve of them seemingly led to trading-related sites. Take a look at two examples below.

Next, we subjected the eight domains tagged as IoCs to DNS lookups and found that two resolved to one unique IP address each.
IP geolocation lookups for the two IP addresses—172[.]234[.]25[.]151 and 45[.]39[.]148[.]106 showed that:
Reverse IP lookups for the two IP addresses revealed that both were shared so we decided not to look for IP-connected domains as they would likely be false positives.
Next, we used Domains & Subdomains Discovery to look for other domains that contained text strings that appeared among the domain IoCs. We found 112 string-connected domains after duplicates, the IoCs, and the email-connected domains were filtered out. They all started with the following strings:
Forty-eight of the string-connected domains continued to lead to live sites even if more than half of them, 29 to be exact, were parked or led to error or blank pages.
To succeed, pig butchering scams need to convince potential victims they are making legitimate investments. That is why scammers typically use domains with related text strings, such as forex, coin, and trading, akin to some of these domains identified as IoCs:
To cover all the bases, therefore, we scoured the DNS for other domains containing the three strings mentioned above that pig butchering scammers could weaponize in future attacks. We used the strings as Domains & Subdomains Discovery search terms and found 11,409 domains in total.
Threat Intelligence API revealed that 13 of the additional string-connected domains were associated with phishing and generic threats. Here are five examples.
| MALICIOUS ADDITIONAL STRING-CONNECTED DOMAIN | ASSOCIATED THREAT TYPE |
|---|---|
| coinbase-coin[.]shop | Phishing |
| coinwavepros[.]site | GenericPhishing |
| coinxiazai[.]com | Phishing |
| hychain[.]trading | Phishing |
| walletlink-coinbase[.]com | Phishing |
Screenshot lookups showed that five of the malicious additional string-connected domains remained accessible—three of them led to blank, error, or under construction pages, while the remaining two led to live sites as shown below.
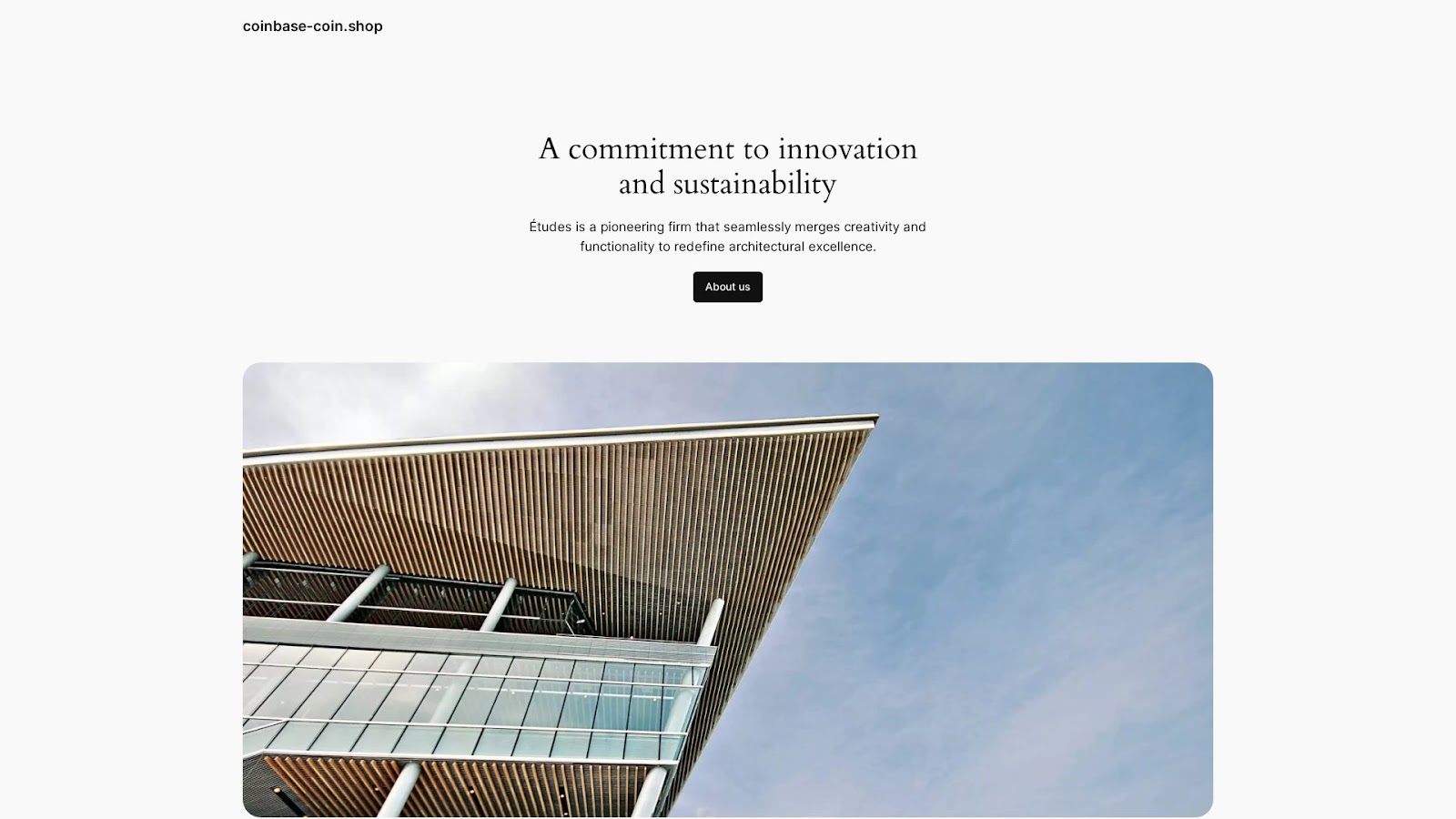
It is interesting to note that all of the malicious additional string-connected domains contained the text string coin. That could be due to the popularity of investing in cryptocurrency at the moment.
Our DNS deep dive into pig butchering scams led to the discovery of 141 connected threat artifacts, one of which turned out to be malicious. It also revealed the presence of a number of finance-, cryptocurrency-, and trading-related domains that already figured in or could be weaponized in the future for phishing campaigns, possibly even pig butchering scams.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byRadix

Sponsored byCSC

Sponsored byWhoisXML API

Sponsored byDNIB.com

Sponsored byIPv4.Global

Sponsored byVerisign

Sponsored byVerisign
