


|
||
|
||
Phishing is and remains a top threat. Google alone blocks around 100 million phishing emails daily, and it doesn’t help that phishers get extra help from phishing kits—ready-made cybercrime tools that allow even cybercriminal newbies to launch attacks following a few simple steps.
Resecurity recently uncovered a phishing campaign targeting the customers of several European banks aided by the V3B Phishing Kit. The company’s research on the threat identified 28 domains as indicators of compromise (IoCs).
The WhoisXML API research team expanded the current list of IoCs in a bid to identify other potentially connected artifacts and found:
Note that this post contains only a preview of our findings. The full research, including a sample of the additional artifacts obtained from our analysis are available for download from our website.
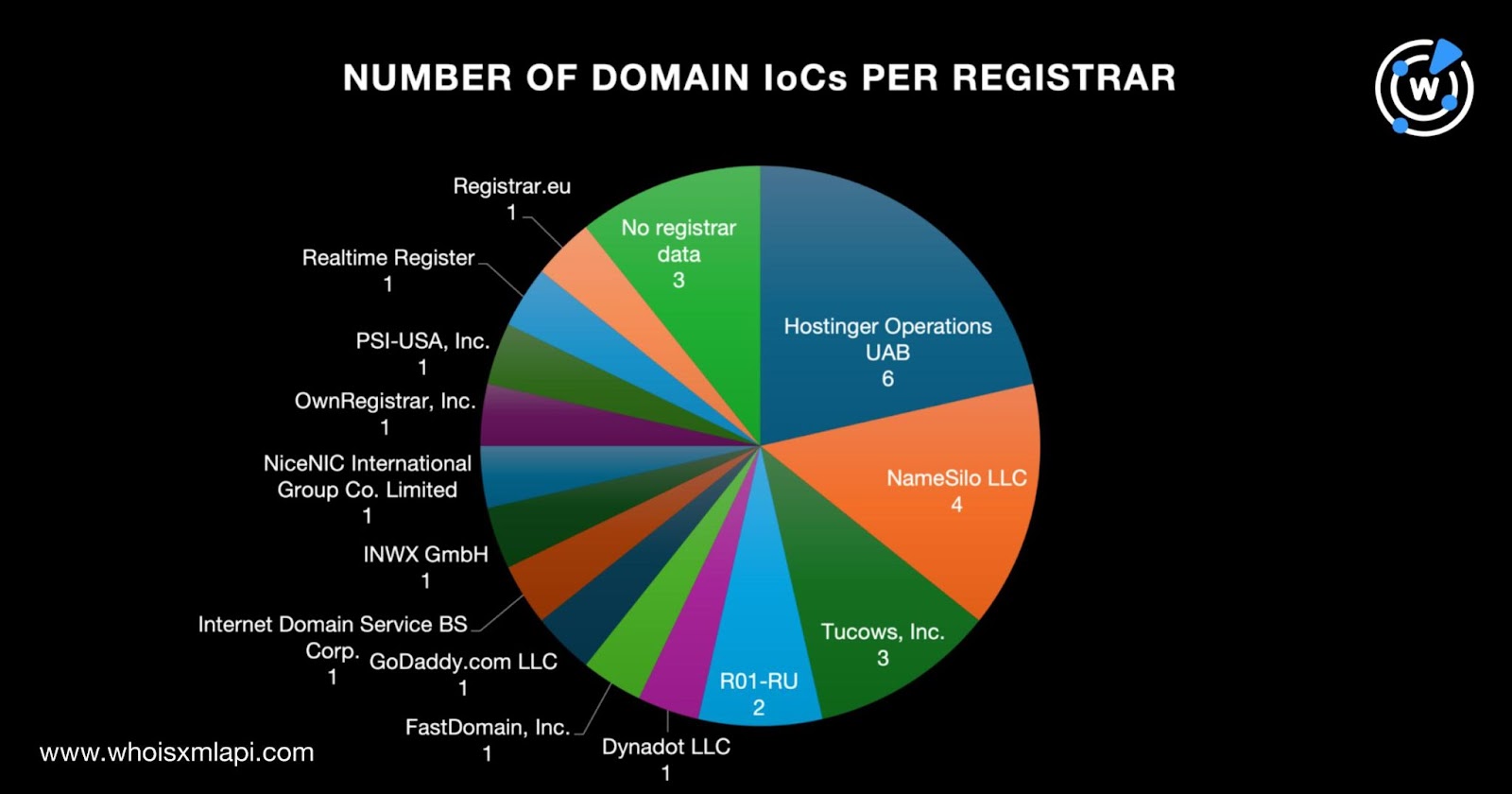
To find out more about the threat, we began by looking into the WHOIS records of the 28 domains tagged as IoCs via a bulk WHOIS lookup. Our query gave the following results:
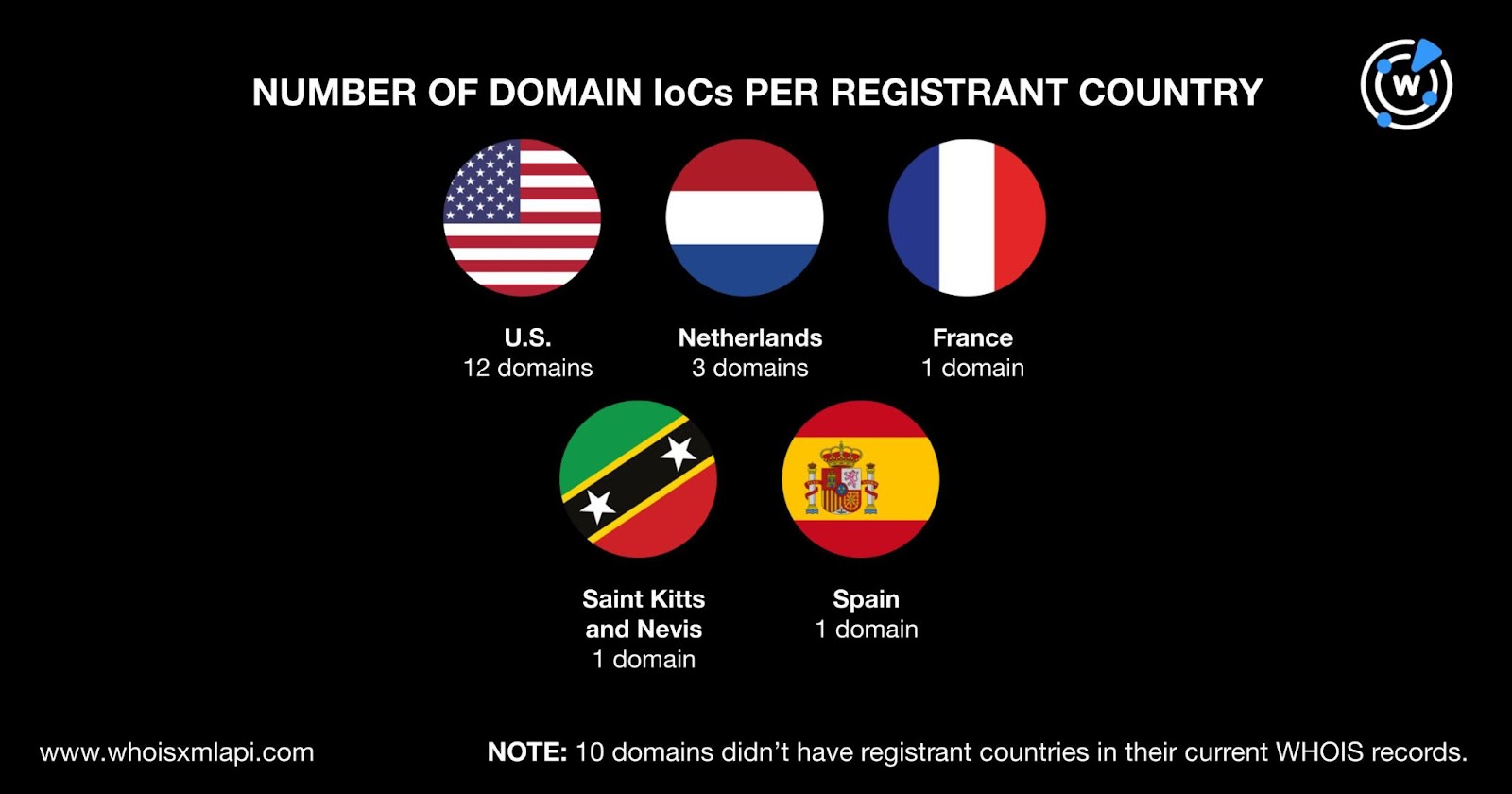
The domain IoCs were registered in five countries led by the U.S., which accounted for 12 domains. The Netherlands took the second spot with three domain IoCs. France, Saint Kitts and Nevis, and Spain accounted for one domain each. Finally, 10 domain IoCs didn’t have registrant countries in their current WHOIS records.
We began our search for connected threat artifacts by querying the 28 domains tagged as IoCs on WHOIS History API. The query led to the discovery of 15 email addresses in their historical WHOIS records after duplicates were filtered out. Eight of the email addresses were public.
Reverse WHOIS API queries for the eight public email addresses revealed that they were present in the current WHOIS records of 177 email-connected domains after duplicates and the IoCs were removed.
Next, we conducted DNS lookups for the 28 domains tagged as IoCs and found that they resolved to nine unique IP addresses, eight of which turned out to be associated with various threats according to Threat Intelligence Lookup.
This post only contains a snapshot of the full research. You can download the complete findings and a sample of the additional artifacts found on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byWhoisXML API

Sponsored byVerisign

Sponsored byVerisign

Sponsored byCSC

Sponsored byIPv4.Global

Sponsored byDNIB.com

Sponsored byRadix
