


|
||
|
||
Check Point Research published an in-depth analysis of the recent spearphishing attack launched by Iranian threat group Educated Manticore. The attackers targeted Israeli journalists, high-profile cybersecurity experts, and computer science professors from leading Israeli universities.
The threat actors directed victims who engaged with them to fake Gmail login pages or Google Meet invitations. The credentials the victims entered on phishing pages were sent to the attackers, enabling them to intercept passwords and two-factor authentication (2FA) codes and gain unauthorized access to the victims’ accounts.
The researchers identified 141 indicators of compromise (IoCs) comprising 129 domains and 12 IP addresses in their report “Iranian Educated Manticore Targets Leading Tech Academics.” We analyzed the IoCs in greater depth and uncovered:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
We began our analysis by looking deeper into the IoCs by querying the 129 domains tagged as IoCs on Bulk WHOIS API. We discovered that 125 of them had current WHOIS records. Further analysis of the 125 domains showed that:
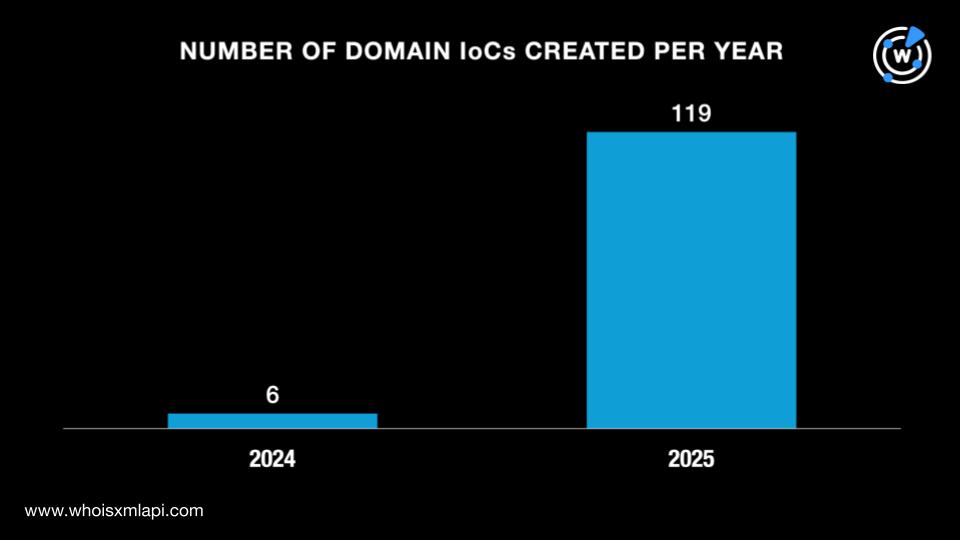
They were split among four registrars led by Namecheap, which accounted for 111 domains. NameSilo came in second place with 11 domains. Dynadot placed third with two domains. Finally, Communigal Communications accounted for one domain.
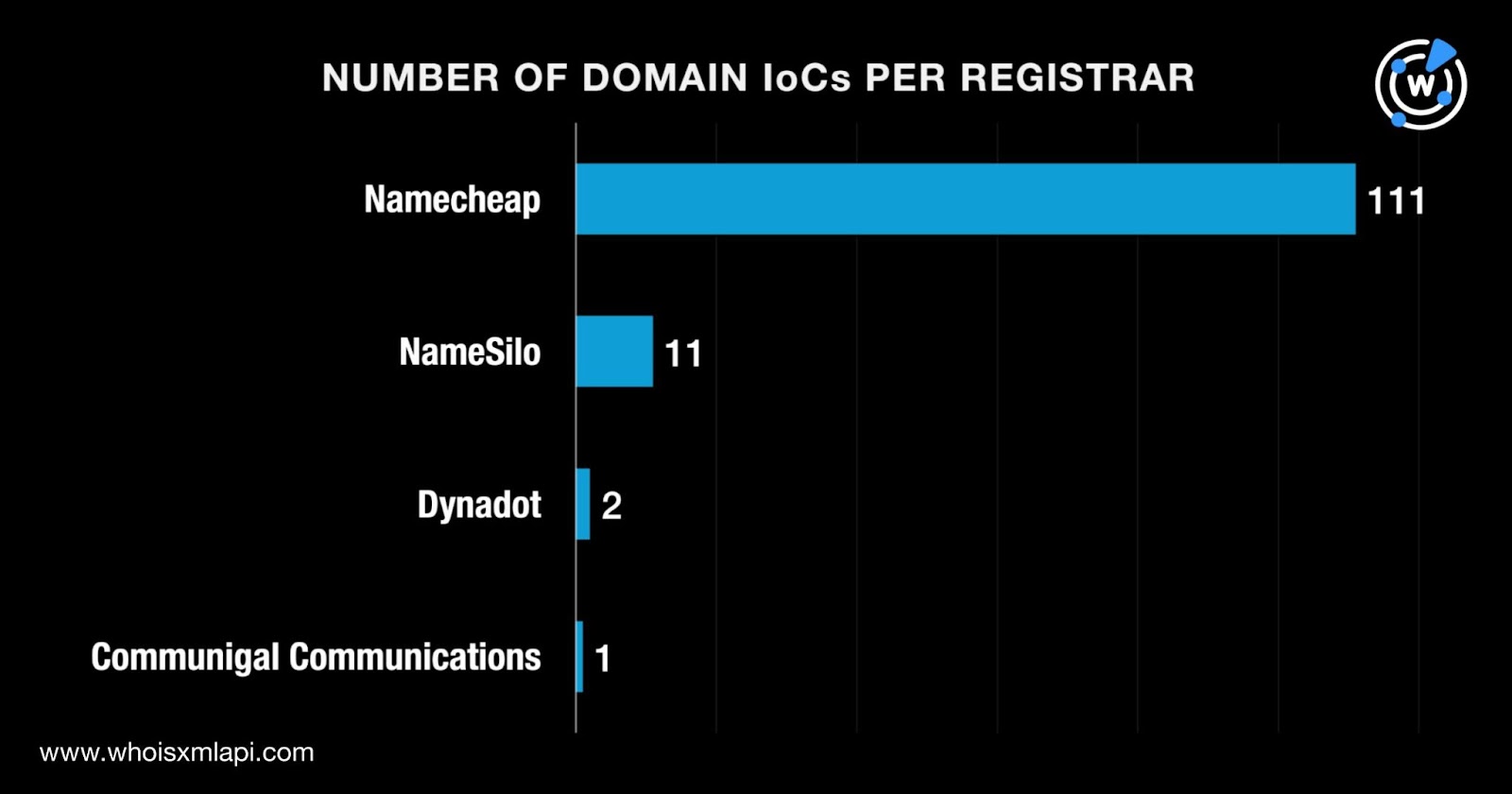
Only 71 of the 125 domains had registrant countries on record. They were registered in three countries topped by Iceland, which accounted for 57 domains. The U.S. took the second spot with 13 domains. Cyprus placed third with one domain. The remaining 54 domains did not have registrant countries in their current WHOIS records.
A DNS Chronicle API query for the 129 domains tagged as IoCs showed that 123 of them had historical domain-to-IP resolutions. Specifically, the 123 domains recorded 2,630 resolutions over time. The IoC alpha-man[.]info posted the oldest domain-to-IP resolution on 5 February 2017. Take a look at more details for five other domains below.
| DOMAIN IoC | NUMBER OF DOMAIN-TO-IP RESOLUTIONS | FIRST RESOLUTION DATE |
|---|---|---|
| conn-ectionor[.]cfd | 1 | 24 June 2025 |
| becker624[.]online | 1 | 16 June 2025 |
| steve-brown[.]info | 3 | 6 April 2025 |
| network-show[.]online | 1 | 4 February 2025 |
| suite-moral[.]info | 3 | 26 April 2025 |
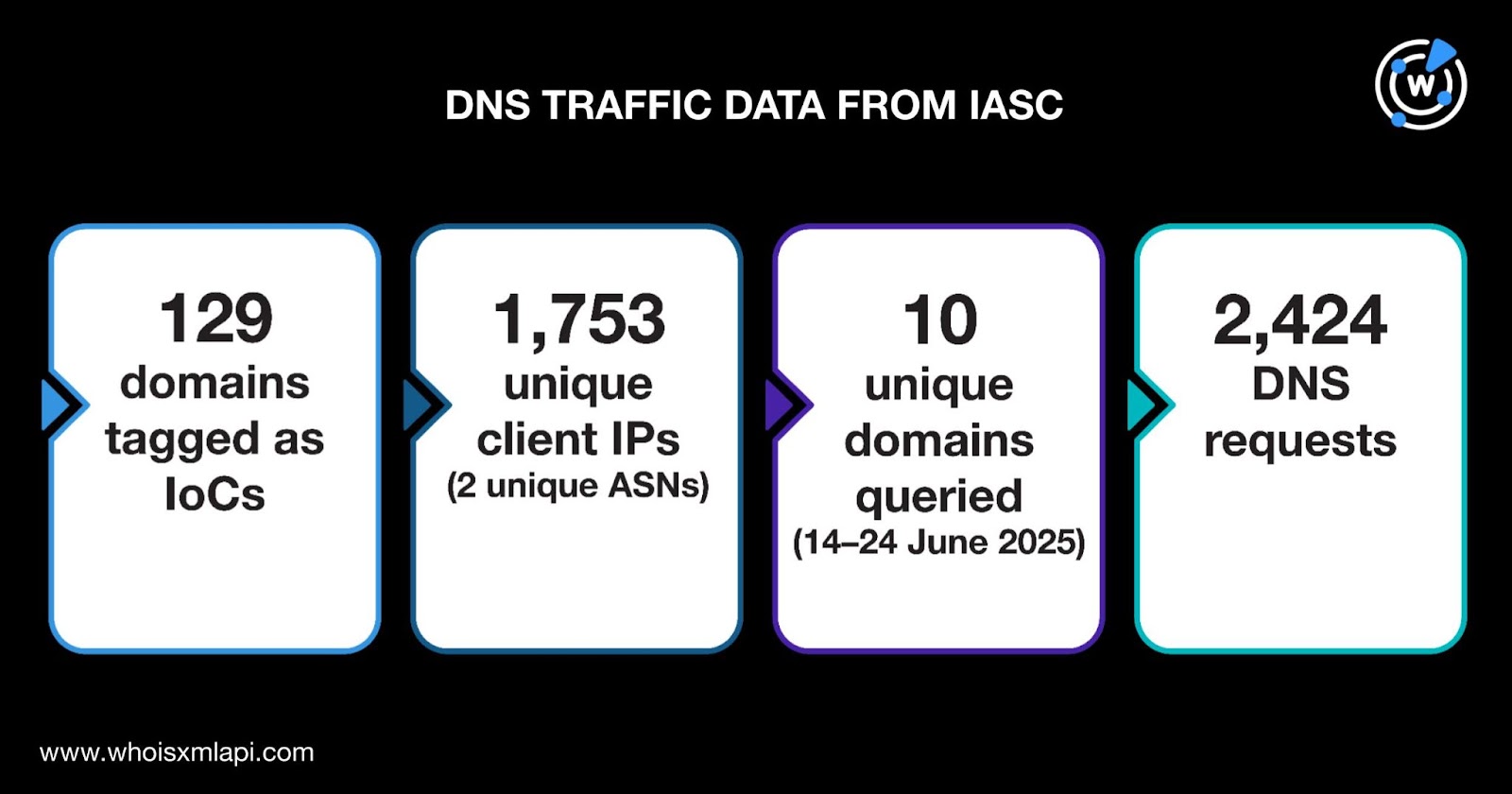
Using sample DNS traffic data our researchers obtained from the IASC, we further analyzed the 129 domains tagged as IoCs. The sample data revealed that 1,753 unique client IP addresses tied to two unique AS numbers queried 10 distinct domains on 14—24 June 2025 via 2,424 DNS requests.
We then queried the 129 domains on First Watch and found that 72 of them appeared on various feeds 5—454 days before they were reported as attack IoCs on 25 June 2025. Take a look at five examples below.
| DOMAIN IoC | FIRST WATCH DATE ADDED | NUMBER OF DAYS PRIOR TO REPORTING DATE |
|---|---|---|
| world-shop[.]online | 28 March 2024 | 454 |
| spring-club[.]info | 9 March 2025 | 108 |
| nsim-ph[.]info | 10 April 2025 | 76 |
| yamal-group[.]online | 27 April 2025 | 59 |
| optio-nalynk[.]online | 20 June 2025 | 5 |
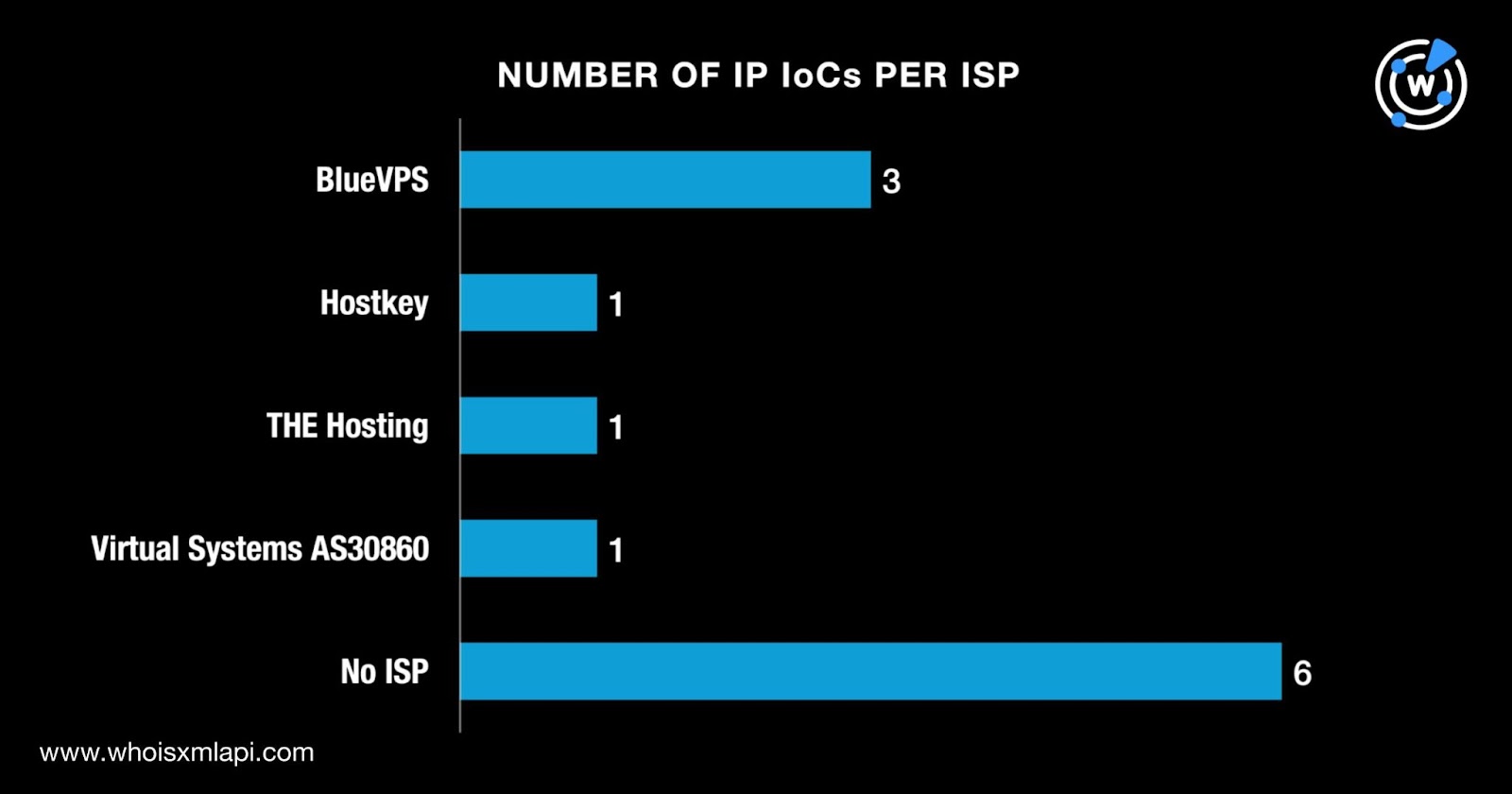
Next, we queried the 12 IP addresses tagged as IoCs on Bulk IP Geolocation Lookup and found that:
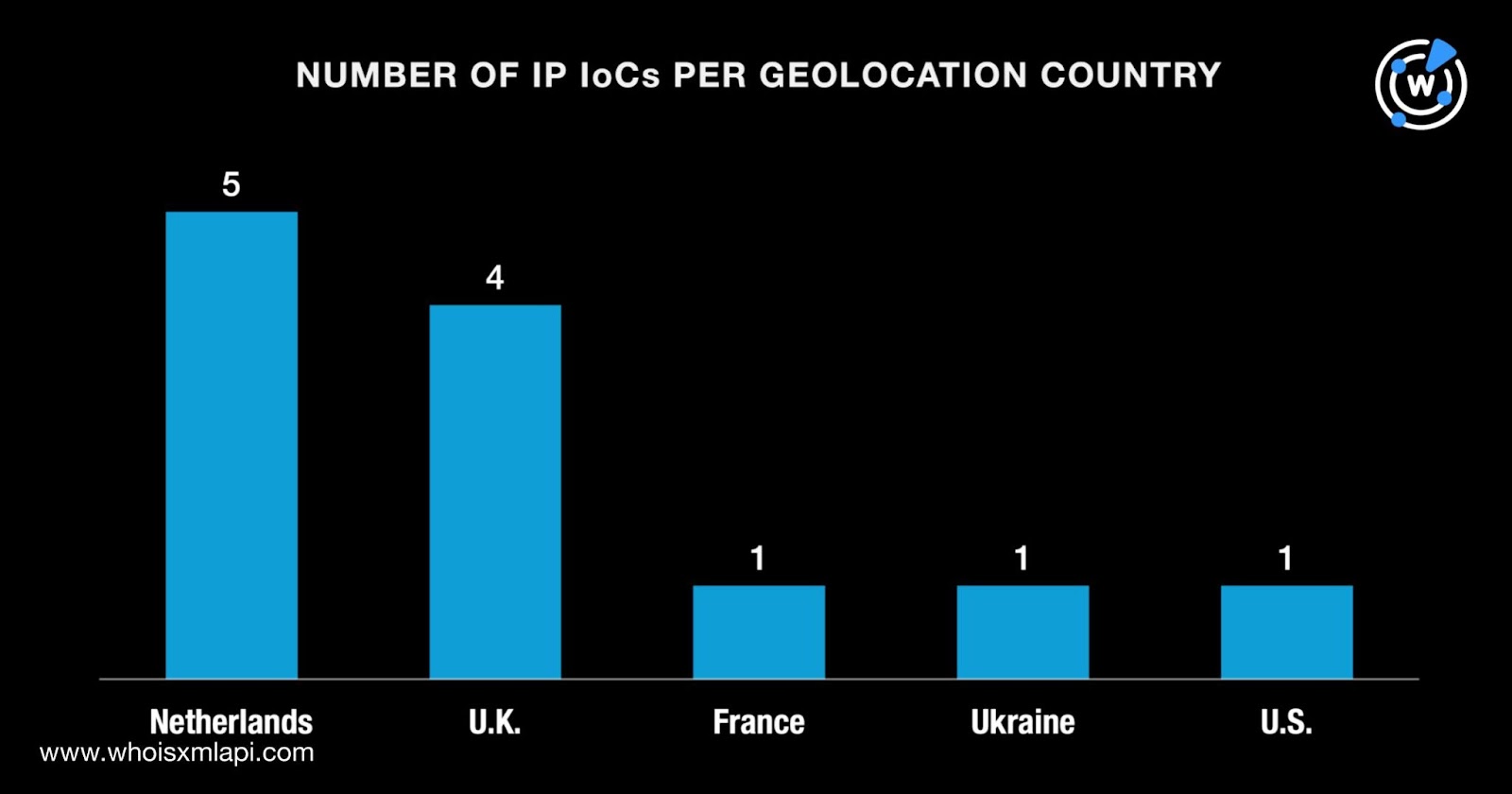
While six of them did not have ISPs on record, the other six were administered by four ISPs topped by BlueVPS, which accounted for three IP addresses. Finally, one IP address each was administered by Hostkey, THE Hosting, and Virtual Systems AS30860.
A DNS Chronicle API query for the 12 IP addresses revealed that all of them had historical IP-to-domain resolutions. Specifically, the 12 IoCs recorded 6,860 resolutions over time. The IP address 195[.]66[.]213[.]132 posted the oldest IP-to-domain resolution on 4 February 2017.
| IP IoC | NUMBER OF IP-TO-DOMAIN RESOLUTIONS | FIRST RESOLUTION DATE |
|---|---|---|
| 146[.]19[.]254[.]238 | 1,000 | 6 April 2025 |
| 194[.]11[.]226[.]29 | 1,000 | 1 October 2024 |
| 194[.]11[.]226[.]5 | 1,000 | 10 March 2025 |
| 194[.]61[.]120[.]185 | 1,000 | 23 November 2019 |
| 45[.]12[.]2[.]158 | 121 | 18 January 2022 |
We also looked for more information on the 12 IP addresses tagged as IoCs using traffic data we obtained from IASC and discovered that one of them—185[.]130[.]226[.]71—communicated with one source IP.
We started our in-depth analysis by querying the 129 domains tagged as IoCs on WHOIS History API and discovered that seven of them had email addresses in their historical WHOIS records. In particular, the seven domains had 14 email addresses, six of which were public addresses.
While our Reverse WHOIS API query for the six public email addresses showed they did not appear in any current WHOIS records, all of them did appear in historical records. Specifically, the six addresses were present in the historical WHOIS records of 217 email-connected domains after duplicates and those already tagged as IoCs were filtered out.
A Threat Intelligence API query for the 217 email-connected domains revealed that one of them—top-game[.]online—already figured in malware distribution.
After that, we queried the 129 domains tagged as IoCs on DNS Lookup API and discovered that 54 of them had current IP resolutions. After duplicates and those already identified as IoCs were filtered out, we were left with one additional IP address.
A Threat Intelligence API query for the IP address 198[.]54[.]117[.]242 showed that it has already figured in malware distribution, generic threats, phishing, suspicious activity, and command and control (C&C).
Next, an IP Geolocation API query for the additional IP address revealed that it was geolocated in the U.S. and administered by Namecheap. While it shared one IP IoC’s geolocation country, it did not share any of the IoCs’ ISPs.
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byVerisign

Sponsored byRadix

Sponsored byIPv4.Global

Sponsored byVerisign

Sponsored byCSC

Sponsored byWhoisXML API

Sponsored byDNIB.com
