


|
||
|
||
Palo Alto Unit 42 reported on the latest Slow Pisces attack that engaged with cryptocurrency developers on LinkedIn. The threat actors posed as potential employers and sent malware disguised as coding challenges. Developers who took on the challenge ended up running a compromised project, infecting their systems with RN Loader and RN Stealer.
The report identified 54 indicators of compromise (IoCs) comprising 27 domains and 27 IP addresses, which WhoisXML API expanded. Our analysis led to the discovery of other potentially connected artifacts, namely:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
Our threat investigation began with a deep dive into the 54 IoCs Palo Alto Unit 42 identified.
We started by querying the 27 domains identified as IoCs on Bulk WHOIS API, which revealed that only 26 of them had current WHOIS records. We also found that:
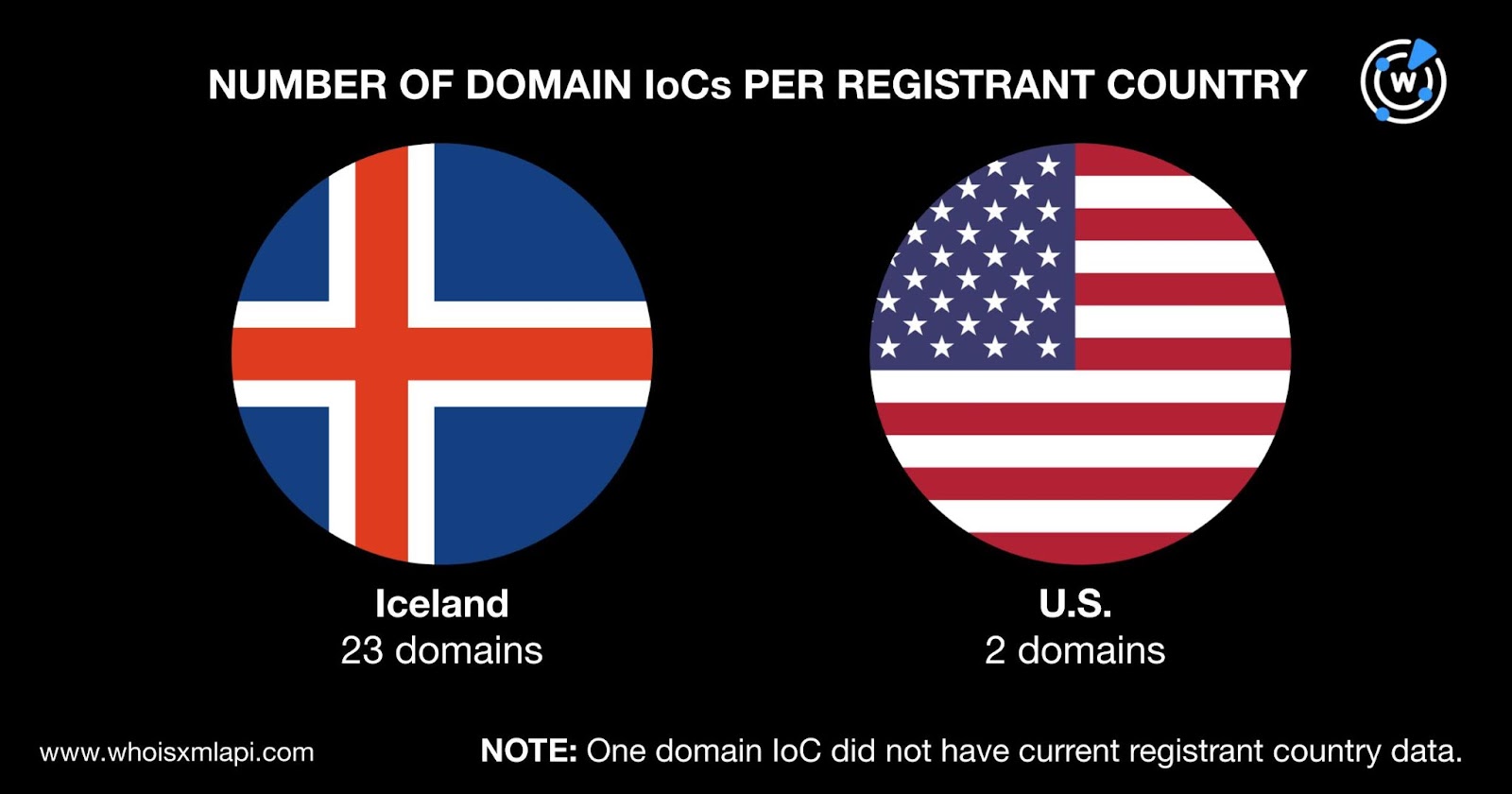
While one of the 26 domains did not have a registrant country on record, the 25 remaining ones were split between two countries. Specifically, 23 domains were registered in Iceland while two were registered in the U.S.
We then queried the 27 domains identified as IoCs on DNS Chronicle API and found that 24 of them had historical domain-to-IP address resolutions. The 24 domains had 239 IP resolutions over time. The domain leaguehub[.]net with 67 resolutions in all, in particular, recorded the oldest resolution date, that is, 6 February 2017. Take a look at more details for five other domains below.
| DOMAIN IoC | NUMBER OF RESOLUTIONS | FIRST IP RESOLUTION DATE |
|---|---|---|
| bitzone[.]io | 30 | 6 June 2020 |
| coinhar[.]io | 1 | 27 March 2025 |
| getstockprice[.]info | 1 | 8 January 2025 |
| logoeye[.]net | 1 | 9 October 2024 |
| stocksindex[.]org | 16 | 7 February 2017 |
Considering that bitzone[.]io was created on 25 April 2024 but first resolved to an IP address on 6 June 2020, it may have been recently reregistered. The same is true for stocksindex[.]org, which was created on 11 September 2024 but first resolved to an IP address on 7 February 2017.
Next, we queried the 27 IP addresses identified as IoCs on Bulk IP Geolocation Lookup and discovered that:
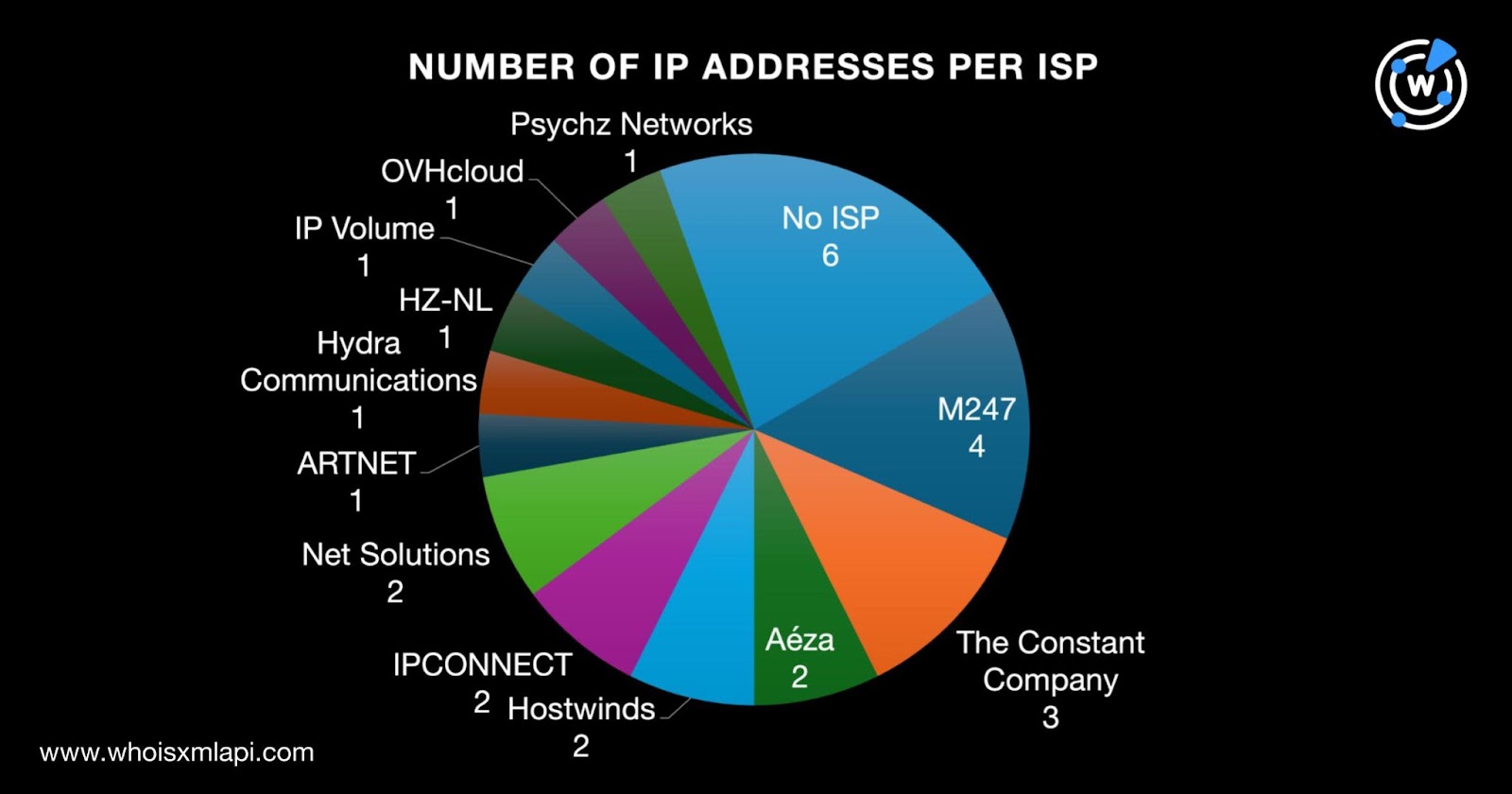
Only 21 of the 27 IP addresses had ISPs on record. Specifically, four IP addresses were administered by M247. The Constant Company administered three IP addresses while Aéza, Hostwinds, IPCONNECT, and Net Solutions administered two each. Finally, one IP address each was administered by ARTNET, Hydra Communications, HZ-NL, IP Volume, OVHcloud, and Psychz Networks.
A DNS Chronicle API query for the 27 IP addresses identified as IoCs revealed that 22 of them had historical IP address-to-domain resolutions. Specifically, the 22 IP addresses recorded 2,011 resolutions over time. The IP address 54[.]39[.]83[.]151 with 239 resolutions had the oldest resolution date, that is, 17 October 2019. Take a look at additional details for five other IP addresses below.
| IP ADDRESS IoC | NUMBER OF RESOLUTIONS | FIRST DOMAIN RESOLUTION DATE |
|---|---|---|
| 185[.]62[.]58[.]74 | 678 | 18 April 2020 |
| 195[.]133[.]26[.]32 | 14 | 19 November 2021 |
| 5[.]206[.]227[.]51 | 227 | 29 May 2020 |
| 91[.]193[.]18[.]201 | 28 | 28 January 2022 |
| 91[.]234[.]199[.]90 | 139 | 24 January 2023 |
In addition, using sample netflow data our researchers obtained from the IASC, we further analyzed three IP addresses. They served as command-and-control (C&C) IP addresses related to the threat. The sample data revealed 12 alleged victim IP records associated with four ISPs operating under five ASNs according to an additional Bulk IP Geolocation Lookup query.
The IP address IoC 91[.]103[.]140[.]191 proved most interesting in that it sent data to a potential victim IP 10 times and received data from that victim IP seven times for almost four weeks. The source IP 91[.]103[.]140[.]191 also most frequently communicated via port 443 (HTTPS) in our data sample.
We began our IoC list expansion analysis by querying the 27 domains identified as IoCs on WHOIS History API. That enabled us to determine that 11 of them had 44 email addresses in their historical WHOIS records after duplicates were filtered out. Further scrutiny of the 44 email addresses revealed that seven were public email addresses.
Next, we queried the seven public email addresses on Reverse WHOIS API and found that while none of them appeared in any domain’s current WHOIS record, six of them were present in the historical WHOIS records of several domains. Specifically, the six public email addresses led to the discovery of 551 email-connected domains after duplicates and those identified as IoCs were filtered out.
We then queried the 27 domains identified as IoCs on DNS Lookup API and found that eight of them actively resolved to IP addresses. A comparison of the results with the 27 IP addresses identified as IoCs and the removal of duplicates, however, left us with only one additional IP address—199[.]59[.]243[.]228.
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byIPv4.Global

Sponsored byDNIB.com

Sponsored byWhoisXML API

Sponsored byVerisign

Sponsored byRadix

Sponsored byVerisign

Sponsored byCSC
