


|
||
|
||
Check Point Research (CPR) recently discovered the JSCEAL campaign targeting crypto app users. According to “Sealed Chain of Deception: Actors Leveraging Node.JS to Launch JSCEAL,” the threat actors used malicious ads to lure victims to install fake versions of close to 50 of the most popular cryptocurrency trading apps. In the first half of 2025 alone, the actors released around 35,000 malicious ads that have been viewed at least a few million times in the European Union (EU) alone. The apps the users downloaded were, of course, masked variants of JSCEAL.
CPR identified 94 domains as indicators of compromise (IoCs). We analyzed them in great depth and uncovered these discoveries:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
We began our analysis by looking more closely at the 94 domains identified as IoCs. First, we queried them on Bulk WHOIS API and got these results:
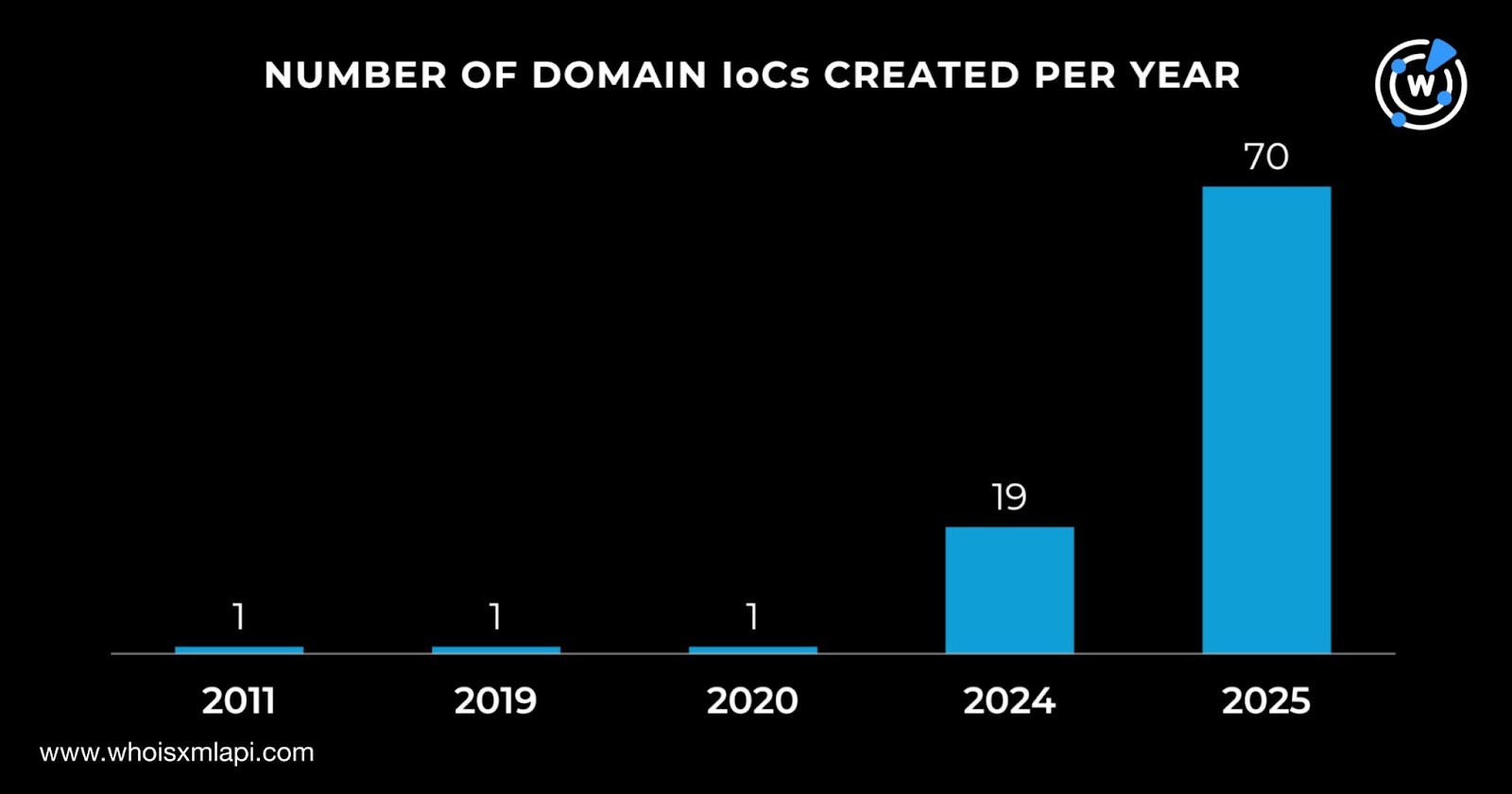
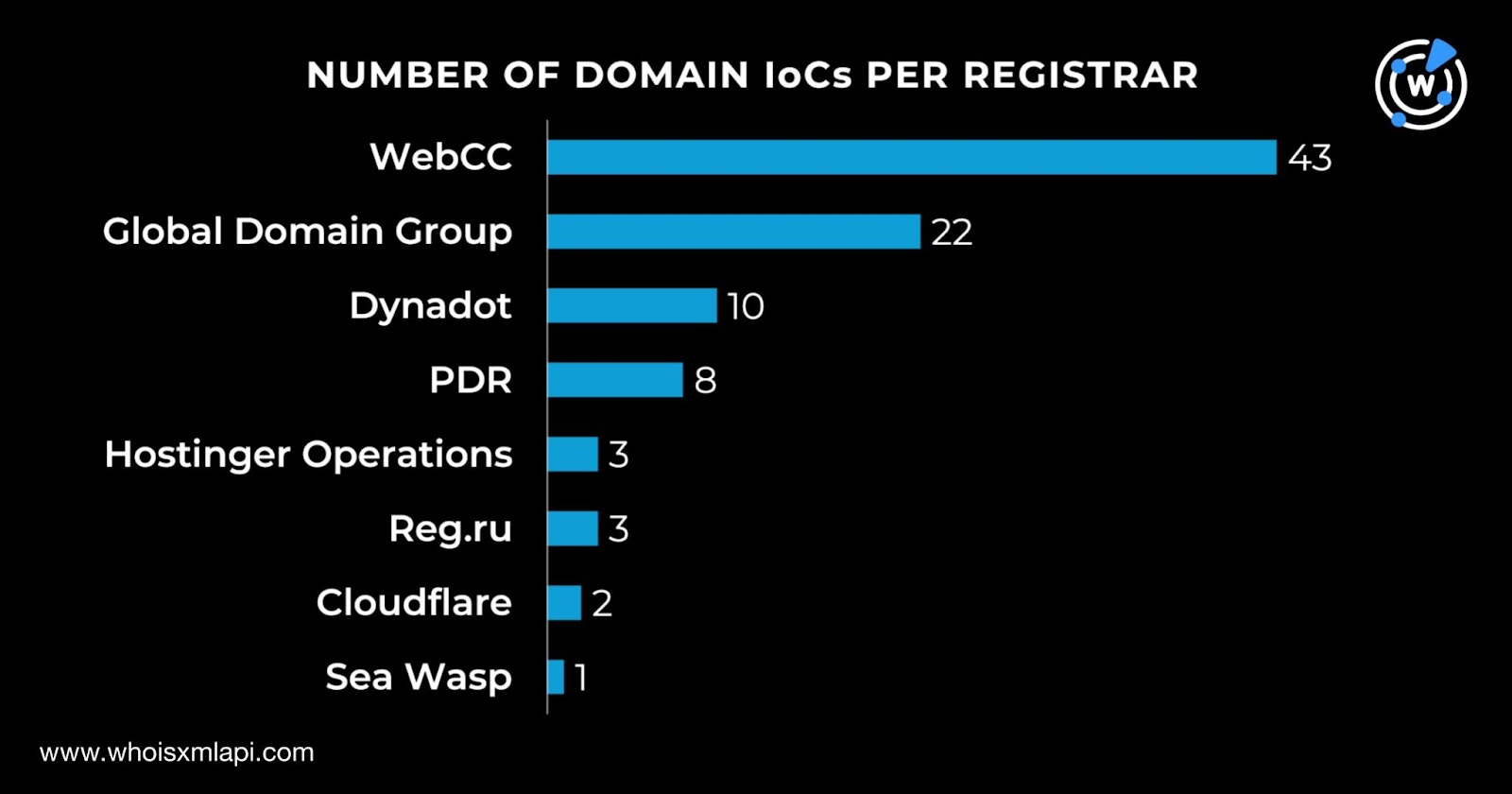
The 92 domains were administered by eight different registrars led by WebCC, which accounted for 43. A total of 22 were managed by Global Domain Group, 10 by Dynadot, eight by PDR, three each by Hostinger Operations and Reg.ru, two by Cloudflare, and one by Sea Wasp.
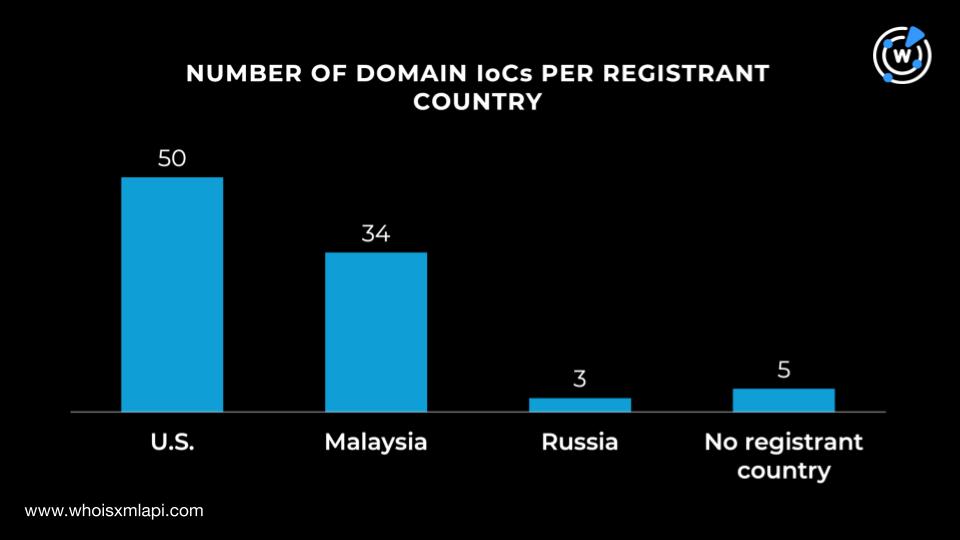
While five of the 92 domains did not have registrant countries on record, the rest were registered in three different countries led by the U.S., which accounted for 50. A total of 34 were registered in Malaysia and three in Russia.
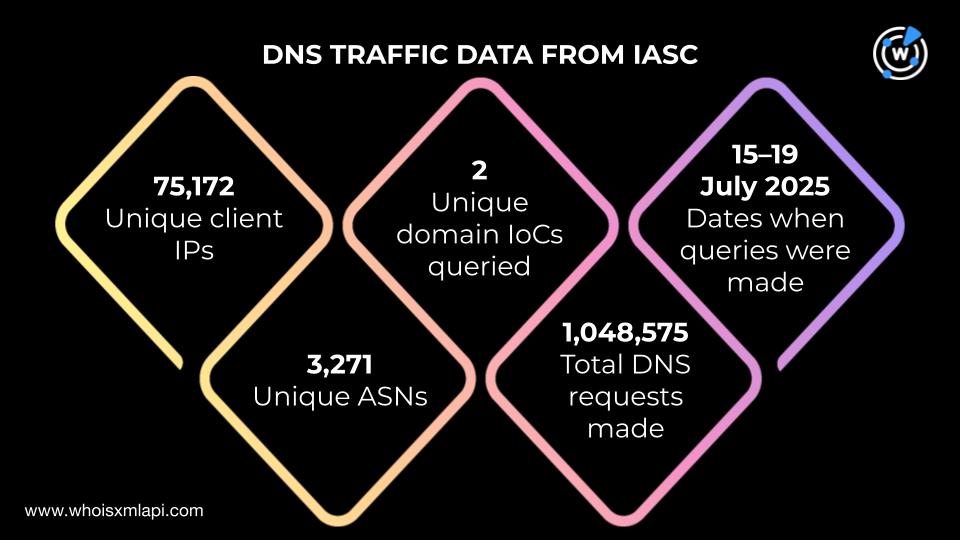
Sample DNS traffic data we obtained from the Internet Abuse Signal Collective (IASC) revealed that 75,172 unique client IPs under 3,271 unique ASNs communicated with two unique IoCs via 1,048,575 DNS requests made on 15-19 July 2025.
First Watch Malicious Domains Data Feed revealed that 56 of the 94 domains identified as IoCs were deemed likely to turn malicious as soon as they were registered, 63—509 days prior to being reported as such on 29 July 2025. The domain ohyoulookstupid[.]win was added to the feed on 7 March 2024, 509 days before it was dubbed an IoC. The domain apps-desktops-download[.]com, meanwhile, was added 63 days prior to being tagged as an IoC. Here are five other examples.
| DOMAIN IoC FOUND ON FIRST WATCH | DATE ADDED TO FIRST WATCH | NUMBER OF DAYS DEEMED LIKELY TO TURN MALICIOUS BEFORE BEING IDENTIFIED AS AN IoC |
|---|---|---|
| downloads-app-pc[.]com | 25 January 2025 | 185 |
| desktop-app-download[.]com | 24 March 2025 | 127 |
| download-desktops-pc[.]com | 3 April 2025 | 117 |
| download-apps-desktop[.]com | 11 April 2025 | 109 |
| apps-downloads-pc[.]com | 30 April 2025 | 90 |
Next, we queried the 94 domains identified as IoCs on DNS Chronicle API and discovered that 92 had 7,364 domain-to-IP resolutions over time. The domain pc-app[.]com posted the oldest resolution date—6 February 2017. Take a look at the historical DNS data for five other domains below.
| DOMAIN IoC | NUMBER OF DOMAIN-TO-IP RESOLUTIONS | FIRST DOMAIN-TO-IP RESOLUTION DATE |
|---|---|---|
| 18-22-59[.]com | 28 | 3 April 2025 |
| apps-desktops-downloads[.]com | 8 | 10 April 2025 |
| download-app-pc[.]com | 15 | 7 March 2025 |
| downloads-windows-apps[.]com | 8 | 17 April 2025 |
| pc-apps-download[.]com | 105 | 9 January 2025 |
A WhoisXML API MCP Server query through the prompt “which of these domains share the same ip infrastructure” for a sample of the 94 domains identified as IoCs revealed that 18-22-59[.]com, foo-foo[.]bar, dockmilk[.]com, pages[.]dev, and workers[.]dev were hosted on Cloudflare-administered IP ranges.
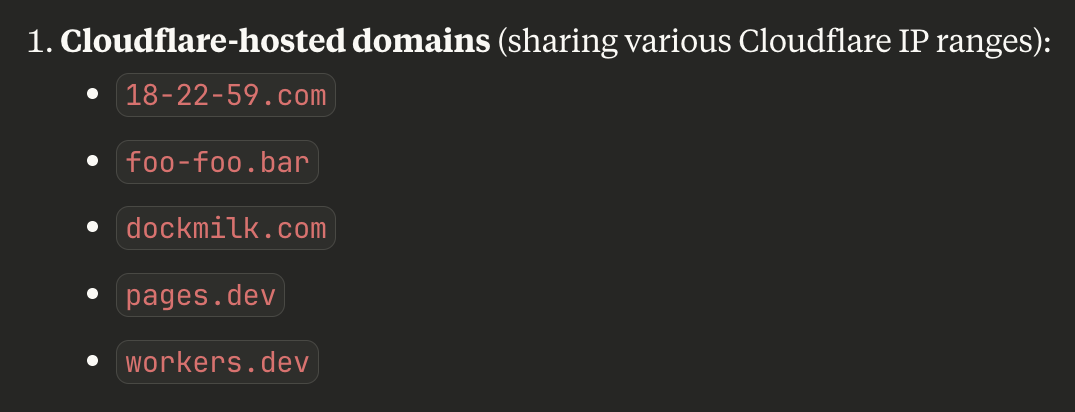
More specifically, they were hosted on the IP addresses listed below.
| DOMAIN IoC | CLOUDFLARE-ADMINISTERED IP ADDRESSES |
|---|---|
| 18-22-59[.]com | 104[.]21[.]12[.]37 172[.]67[.]193[.]164 |
| foo-foo[.]bar | 104[.]21[.]68[.]242 172[.]67[.]200[.]71 |
| dockmilk[.]com | 104[.]21[.]88[.]53 172[.]67[.]173[.]11 |
| pages[.]dev | Cloudflare Pages service |
| workers[.]dev | Cloudflare Pages service |
After finding more information about the IoCs, we sought to determine if other domains shared some of their common text strings. We discovered that several of the 94 domains identified as IoCs shared 14 the text strings listed below. Note that some domains contained more than one string.
| TEXT STRING | NUMBER OF DOMAIN IoCs WITH THE TEXT STRING |
|---|---|
| app-desktop | 5 |
| app-pc | 8 |
| apps-desktop | 7 |
| apps-download | 5 |
| apps-pc | 3 |
| desktop-app | 3 |
| desktops-download | 6 |
| download-app | 6 |
| download-desktop | 7 |
| downloads-app | 7 |
| downloads-desktop | 5 |
| downloads-windows | 2 |
| pc-app | 7 |
| pc-download | 12 |
Searches on Typosquatting Data Feed showed that one domain identified as an IoC—apps-downloads-pc[.]com—appeared in the file for 30 April 2025. Further scrutiny revealed that the group had three domains—one already identified as an IoC and two look-alikes.

Note similarities between the IoC (i.e., highlighted in yellow) and the two look-alike domains in terms of registrant country, registrar, name server (NS) provider, and creation date.
Finally, a comparison of the domain IoC’s current WHOIS record and the typosquatting group’s creation dates revealed they were the same—30 April 2025.
After finding look-alike domains and uncovering similarities between them and the IoCs, we sought to discover new artifacts.
A total of 12 of the 94 domains identified as IoCs had 10 unique public registrant names. While none of the registrant names appeared in other domains’ current WHOIS records, two did so in historical WHOIS records based on the results of our Reverse WHOIS Search queries. Specifically, we uncovered 31 registrant-connected domains after duplicates and those already tagged as IoCs were filtered out.
Next, we queried the 94 domains identified as IoCs on WHOIS History API and found out that their historical WHOIS records had 219 unique email addresses. Further scrutiny revealed that 21 were public email addresses.
We then queried the 21 public email addresses on Reverse WHOIS API, which showed that while none of them appeared in other domains’ current WHOIS records, 10 appeared in historical WHOIS records. This step led to the discovery of 280 email-connected domains after duplicates, those already identified as IoCs, and the registrant-connected domains were filtered out.
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byVerisign

Sponsored byVerisign

Sponsored byWhoisXML API

Sponsored byIPv4.Global

Sponsored byCSC

Sponsored byRadix

Sponsored byDNIB.com
