


|
||
|
||
UNC5174, a Chinese-sponsored group known for using the open-source reverse shell tool named “SUPERSHELL,” struck again. In January 2025, they used a new open-source tool and command-and-control (C&C) infrastructure dubbed “SNOWLIGHT.” This time around, they have begun using another tool dubbed “VShell.”
The Sysdig Threat Research Team disclosed their findings about UNC5174’s latest campaign, including 25 indicators of compromise (IoCs) comprising 13 domains and 12 IP addresses. WhoisXML API expanded the current list of IoCs, which led to the discovery of these new artifacts:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
Before embarking on our IoC list expansion, we sought to uncover more information about the attack IoCs first. To that end, we queried the 13 domains identified as IoCs on Bulk WHOIS API and found that only 11 of them had current WHOIS records. We also discovered that:
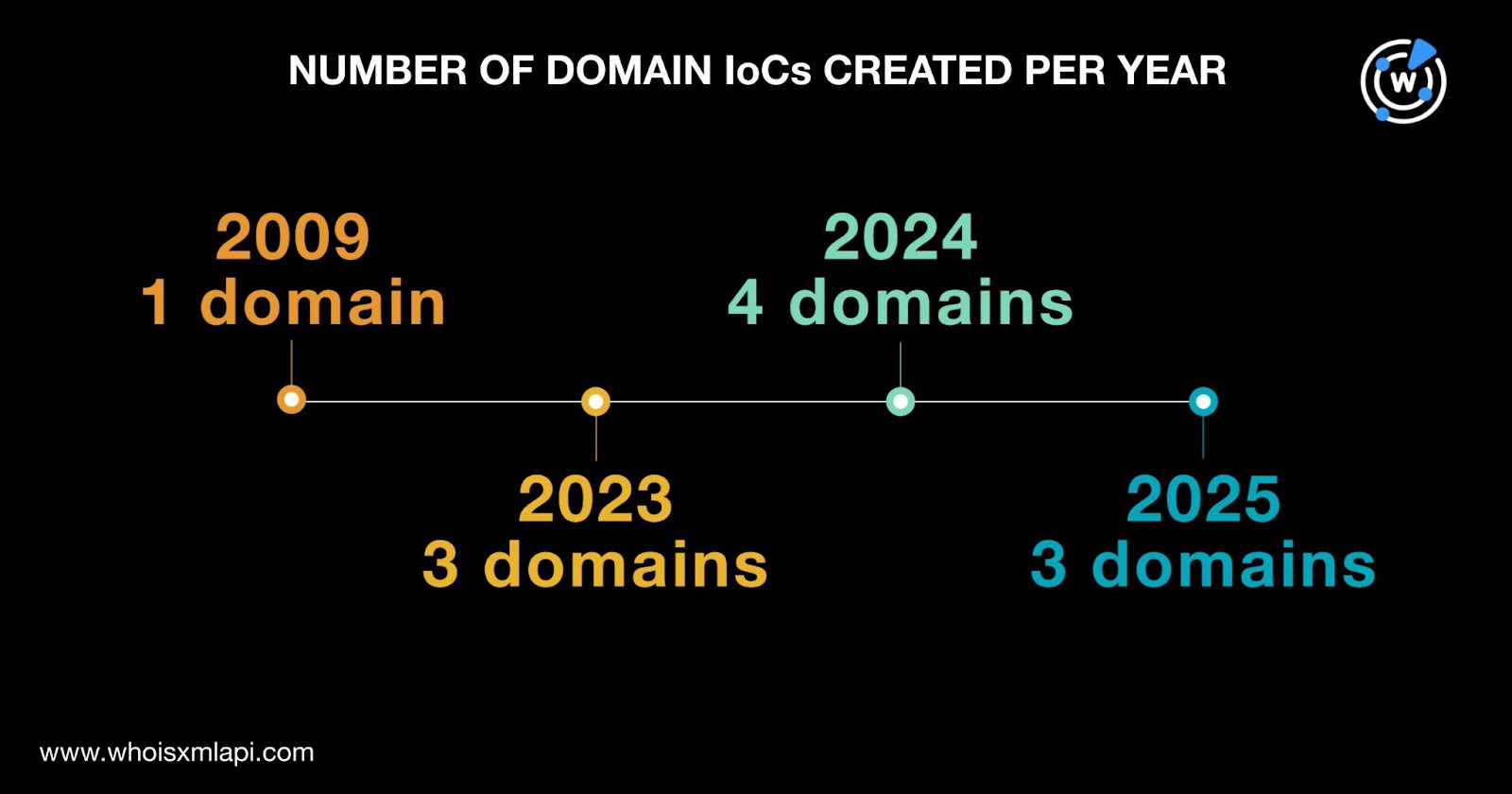
The 11 domains were administered by six registrars led by GoDaddy, which accounted for four domains. Cloudflare and Name.com tied in second place with two domains each. Finally, one domain each was administered by Gname.com, Namecheap, and Whois.
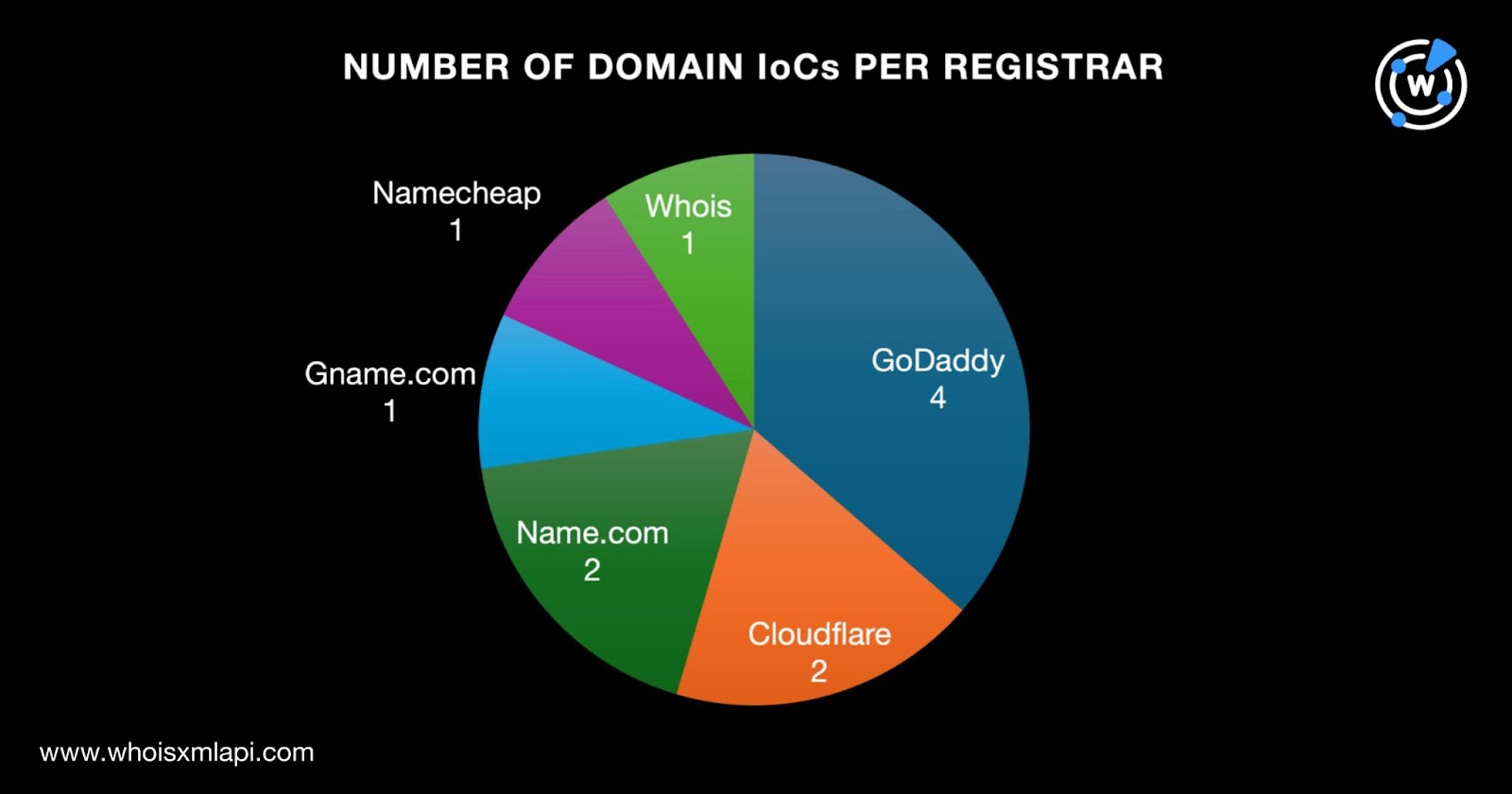
Only 10 of the 11 domains had registrant countries on record. Specifically, they were registered in four countries led by the U.S., which accounted for seven domains. Finally, one domain each was registered in China, Iceland, and South Korea.
We also queried the 13 domains identified as IoCs on DNS Chronicle API and found that only nine of them had historical domain-to-IP resolutions. Altogether, the nine domains posted 207 resolutions over time. The domain c1oudf1are[.]com recorded the oldest IP resolution date. In particular, it resolved to the IP address 104[.]18[.]52[.]126 on 16 October 2019. Take a look at the historical DNS details for three other domains below.
| DOMAIN IoC | NUMBER OF IP RESOLUTIONS | FIRST IP RESOLUTION DATE |
|---|---|---|
| bing-server[.]com | 12 | 1 August 2023 |
| ciscocdn[.]com | 32 | 6 December 2019 |
| gooogleasia[.]com | 27 | 4 September 2023 |
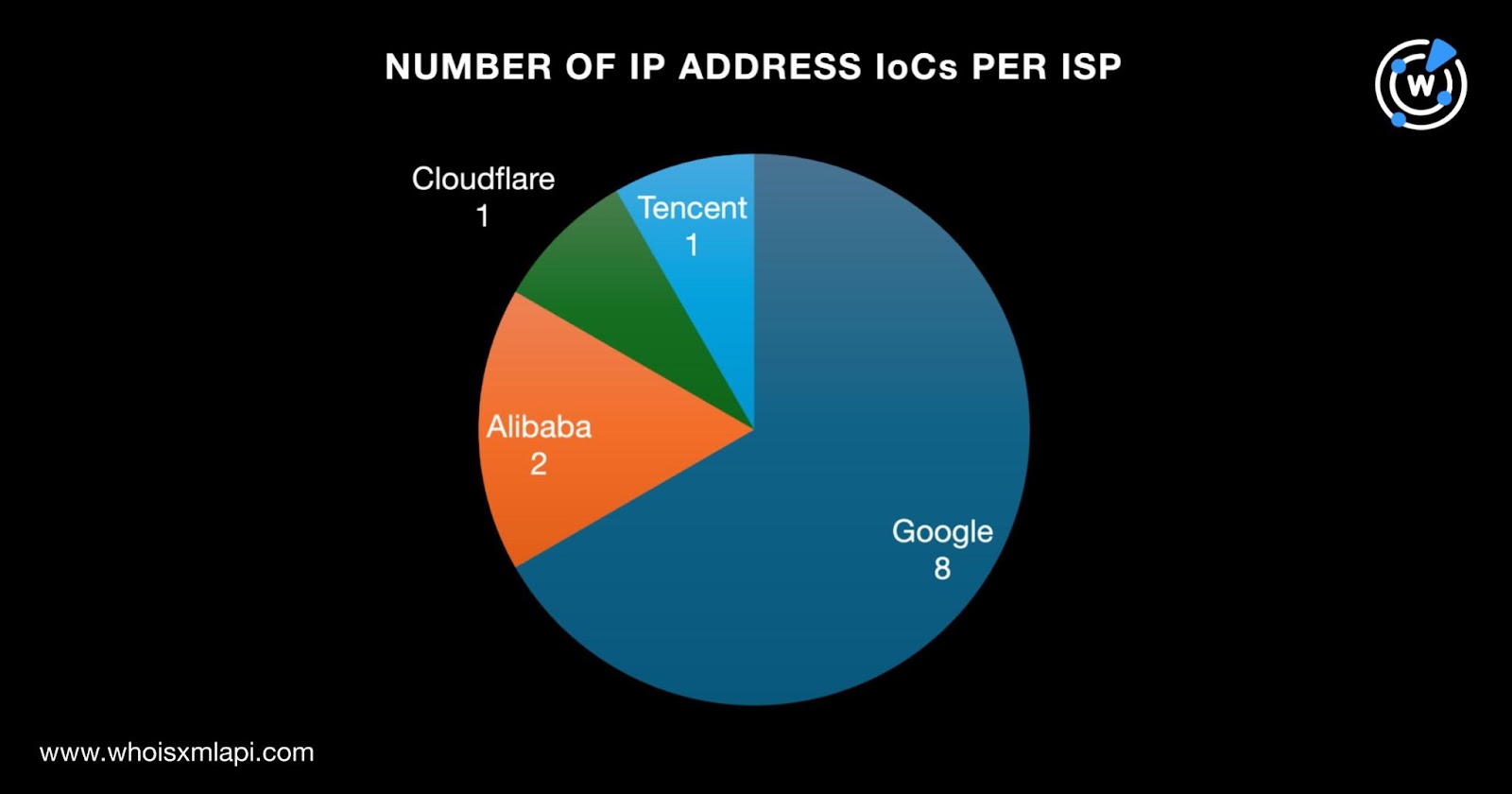
Next, we queried the 12 IP addresses identified as IoCs on Bulk IP Geolocation Lookup and found that:
They were administered by four ISPs led by Google, which accounted for eight IP addresses. Alibaba came in second place with two IP addresses. Finally, one IP address each was administered by Cloudflare and Tencent.
Like the domains identified as IoCs, we queried the 12 IP addresses on DNS Chronicle API as well. We found that 10 of them had historical IP-to-domain resolutions. Specifically, the 10 IP addresses resolved to 1,180 domains so far. Interestingly, six of the 10 IP addresses recorded the oldest resolution date, that is, 19 November 2021. Take a look at five examples below.
| IP ADDRESS IoC | NUMBER OF DOMAIN RESOLUTIONS | FIRST DOMAIN RESOLUTION DATE |
|---|---|---|
| 188[.]114[.]97[.]3 | 1,000 | 25 January 2022 |
| 34[.]131[.]20[.]34 | 12 | 19 November 2021 |
| 34[.]150[.]33[.]237 | 12 | 19 November 2021 |
| 34[.]92[.]255[.]51 | 13 | 19 November 2021 |
| 34[.]96[.]239[.]183 | 42 | 19 November 2021 |
In addition, using sample netflow data our researchers obtained from the IASC, we found additional information on the IP address 45[.]43[.]208[.]31 that was identified as an IoC. The sample data revealed one alleged victim IP record.
Our analysis began with a WHOIS History API query for the 13 domains identified as IoCs. The results showed that only three domains had email addresses in their historical WHOIS records. In particular, the three domains had 15 email addresses in their records after duplicates were filtered out. Further scrutiny revealed that only two were public email addresses.
A Reverse WHOIS API query for the two public email addresses revealed that they were not present in any domain’s current WHOIS records but they did appear in the historical records of eight email-connected domains after duplicates and those already identified as IoCs were filtered out.
Next, we queried the 13 domains identified as IoCs on DNS Lookup API and found that seven of them actively resolved to IP addresses. Specifically, the seven domains resolved to 13 unique IP addresses after duplicates and those already tagged as IoCs were filtered out.
A Threat Intelligence API query for the 13 additional IP addresses showed that 11 have already been weaponized for cyber attacks.
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byRadix

Sponsored byIPv4.Global

Sponsored byVerisign

Sponsored byWhoisXML API

Sponsored byVerisign

Sponsored byCSC

Sponsored byDNIB.com
