

New research has uncovered evidence of spammers establishing their own fake URL-shortening services for the first time. According to the latest MessageLabs Intelligence report, shortened links created on these fake URL-shortening sites are not included directly in spam messages; instead, the spam emails contain shortened URLs created on legitimate URL-shortening sites. "Rather than leading directly to the spammer's final Web site, these links actually point to a shortened URL on the spammer's fake URL-shortening Web site, which in turn redirects to the spammer's final Web site." more
 Kevin Murphy reporting in DomainIncite: "Interpol plans to apply to join ICANN's Governmental Advisory Committee as an observer, according to ICANN. The news came in a press release this evening, detailing a meeting between ICANN president Rod Beckstrom and Interpol secretary general Ronald Noble. The meeting 'focused on Internet security governance and enhancing common means for preventing and addressing Internet crime'." more
Kevin Murphy reporting in DomainIncite: "Interpol plans to apply to join ICANN's Governmental Advisory Committee as an observer, according to ICANN. The news came in a press release this evening, detailing a meeting between ICANN president Rod Beckstrom and Interpol secretary general Ronald Noble. The meeting 'focused on Internet security governance and enhancing common means for preventing and addressing Internet crime'." more
Pingdom has conducted a study on how today's two billion internet users around the world are spread over different time zones. Study found two time zones stand head and shoulders above the others in terms of the amount of Internet users they contain: UTC+8, which passes through eastern Asia, and UTC+1, which passes through Europe and Africa. more
Defense Systems reports: "The U.S. government's sweeping new cybersecurity strategy announced May 16 states that the country will respond to a major cyberattack using any or all of the means at its disposal, reports the Associated Press. Although military response to a cyberattack is one of the options listed in the International Strategy for Cyberspace, it will be considered only as a last resort, officials said." more
Digital Civil Rights in Europe reports: "During an investors day on 10 May 2011 in London, Dutch Internet service provider KPN admitted to using deep packet inspection (DPI) technology, to determine the use of certain applications by its mobile internet customers. Vodafone soon followed with an announcement that it used this technology for traffic shaping. The Dutch minister of Economic Affairs within days announced an investigation into KPN's practices and promised to publish the results within two weeks." more
Microsoft Program Manager, Jeb Haber, reports in a blog post that from browser data collected on user downloads, 1 out of every 14 programs downloaded is later confirmed as malware. Haber says: "Consumers need information to make better decisions. That said, IE9 adds another layer of defense against socially engineered attacks that now looks at the application being downloaded -- this is in addition to the URL-based protection described above. This new layer of protection is called SmartScreen Application Reputation." more
UK registry Nominet has enabled the deployment of domain name system security extensions (DNSSEC) for 9.4 million second level .uk domains. Completing the rollout represents over a year's work and marks an important milestone in making the web a more trusted environment for UK consumers and businesses, says Nominet, which is responsible for running the .uk internet infrastructure. more
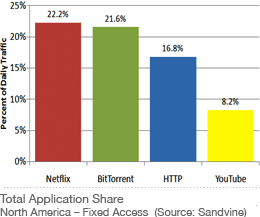 Netflix has become the largest source of Internet traffic in North America, according Sandvine's Spring 2011 Global Internet Phenomena Report. Company further reports that currently, Real-Time Entertainment applications consume 49.2% of peak aggregate traffic, up from 29.5% in 2009 -- a 60% increase [see figture]. Sandvine forecasts that the Real-Time Entertainment category will represent 55-60% of peak aggregate traffic by the end of 2011. more
Netflix has become the largest source of Internet traffic in North America, according Sandvine's Spring 2011 Global Internet Phenomena Report. Company further reports that currently, Real-Time Entertainment applications consume 49.2% of peak aggregate traffic, up from 29.5% in 2009 -- a 60% increase [see figture]. Sandvine forecasts that the Real-Time Entertainment category will represent 55-60% of peak aggregate traffic by the end of 2011. more
 Google yesterday dove deep into its Chrome notebook project at its annual Google I/O conference. The company has had the notebook operating system in beta for almost two years now. Google announced the first market-ready Chromebooks from partners Samsung and Acer. The Chrome OS is dependent on the cloud for storage and various web-based applications. The result is a machine that boots in a matter of seconds and carries very little in the line of native hardware. more
Google yesterday dove deep into its Chrome notebook project at its annual Google I/O conference. The company has had the notebook operating system in beta for almost two years now. Google announced the first market-ready Chromebooks from partners Samsung and Acer. The Chrome OS is dependent on the cloud for storage and various web-based applications. The result is a machine that boots in a matter of seconds and carries very little in the line of native hardware. more
VeriSign reports that it has reached a Settlement Agreement and Mutual Release with the Coalition for ICANN Transparency, Inc. ("CFIT"), CFIT's members, and specified related parties that resolves the over five-year long CFIT litigation. Under the terms of the Agreement, no payment will be made and the parties immediately will file a dismissal with prejudice of all claims in the litigation. Further, the parties executed mutual releases from all claims now and in the future related to the litigation. more
A recently conducted analysis of Canada's cyber security risk profile by Websense has detected trends indicating Canada is becoming the new launchpad for cybercriminals. Sr. Manager, Security Research at Websense in a blog post writes: "Cybercriminals are on the move again. And, this time, Canada is the prime target. IP addresses in China and Eastern Europe are highly scrutinized and undergoing intense evaluation. So hackers are on a quest to move their networks to countries, like Canada, that have better cyber reputations." more
In an press release today, Microsoft has made the official announcement for the purchase of Skype — one the most expensive acquisitions to date according to the company. more
Jason Mick reporting in DailyTech: "In the definitive cyberpunk novel Neuromancer, published in 1984, author William Gibson prophetically envisioned that wars of the future would be fought over the internet -- a new construct at the time. Today that prediction appears on the verge of coming true as we stand on the threshold of a vast digital battle. Agents in China, believed to be working for, or endorsed by the Chinese federal government are carrying out a secret cyberwar against the U.S. government and U.S. businesses. And that war appears to be escalating." more
Caixin reports that the State Council, China's cabinet, has set up an office to regulate internet activity, according to an announcement released on May 4 via an official website. The new department, called the State Internet Information Office, will supervise online content management and process approvals of businesses involved in online news reporting, according to the state-run news agency Xinhua. The new agency is reported to have the authority to investigate and punish online content-providers if necessary. more
Wout de Natris writes to report: "EU Commissioner for the Information Society Neelie Kroes today launched the EU co-funded project for the Internet of the future in which everything will be connected to everyone in the cloud. Here's the link to Mrs. Kroes' speech." more
Sponsored byCSC

Sponsored byRadix

Sponsored byVerisign

Sponsored byIPv4.Global

Sponsored byDNIB.com

Sponsored byVerisign

Sponsored byWhoisXML API
