

 With the upcoming inauguration of United States' 44th President, USTelecom Association has released a Broadband Now video highlighting challenges facing the country, and how broadband can make a significant difference. From revitalizing the economy to tackling health care, education and global climate change, broadband can play a vital role, says the association which represents broadband service providers, manufacturers and suppliers providing advanced applications and entertainment. more
With the upcoming inauguration of United States' 44th President, USTelecom Association has released a Broadband Now video highlighting challenges facing the country, and how broadband can make a significant difference. From revitalizing the economy to tackling health care, education and global climate change, broadband can play a vital role, says the association which represents broadband service providers, manufacturers and suppliers providing advanced applications and entertainment. more
The result of the economic downturn will force cable industry and telephone companies to face some unsettling prospects in terms of customer growth and revenue increases, according to a forecast by research firm, Pike & Fischer. According to the report released today, Pike & Fischer anticipates approximately 5.7 million U.S. households to become new high-speed Internet customers this year, marking a 12% decline in subscriber growth compared to 2008. The report also suggests that the cable industry will capture about 75% of new broadband subscribers. more
 Whatever your personal perspective of the rights and wrongs of the current Arab-Israeli war in Gaza, there is a second front being fought on the Internet, says Jart Armin of HostExploit.com in a blog post today. "This form of warfare is a battle of words and often vivid imagery engaged by hackers from either side of the divide." more
Whatever your personal perspective of the rights and wrongs of the current Arab-Israeli war in Gaza, there is a second front being fought on the Internet, says Jart Armin of HostExploit.com in a blog post today. "This form of warfare is a battle of words and often vivid imagery engaged by hackers from either side of the divide." more
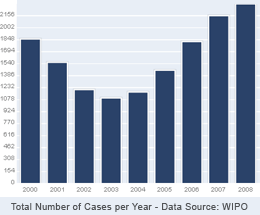 Domain name disputes have been on steady rise for the past several years and have more than doubled since 2003. As reported today by Pingdom, while there was a period between 2000 and 2003 when the number of domain dispute cases declined, they have been continuously increased since 2003 with most cases involving more than one domain name. more
Domain name disputes have been on steady rise for the past several years and have more than doubled since 2003. As reported today by Pingdom, while there was a period between 2000 and 2003 when the number of domain dispute cases declined, they have been continuously increased since 2003 with most cases involving more than one domain name. more
Whistleblower website WikiLeaks has released the list of newly blacklisted websites by Thailand's Ministry of Information and Communication Technology (MICT). The list was leaked by advisory board member CJ Hinke, director of Freedom Against Censorship Thailand, according the WikiLeaks website. From WikiLeaks' announcement: "The 1,203 blocked websites are located in Australia, Brazil, Canada, Czech Republic, France, Germany, Hong Kong, Hungary, India, Ireland, Israel, Italy, Japan, Mexico, The Netherlands, New Zealand, Poland, Russia, South Korea, Spain, Sweden and Vietnam..." more
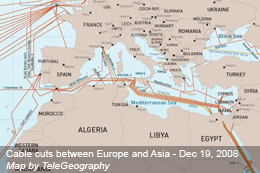 France Telecom has reported today that 3 major underwater cables were cut: “Sea Me We 4” at 7:28am, “Sea Me We3” at 7:33am and FLAG at 8:06am. The causes of the cut, which is located in the Mediterranean between Sicily and Tunisia, on sections linking Sicily to Egypt, remain unclear. Most of the B to B traffic between Europe and Asia is rerouted through the USA. Traffic from Europe to Algeria and Tunisia is not affected, but traffic from Europe to the Near East and Asia is interrupted to a greater or lesser extent (read more for country). more
France Telecom has reported today that 3 major underwater cables were cut: “Sea Me We 4” at 7:28am, “Sea Me We3” at 7:33am and FLAG at 8:06am. The causes of the cut, which is located in the Mediterranean between Sicily and Tunisia, on sections linking Sicily to Egypt, remain unclear. Most of the B to B traffic between Europe and Asia is rerouted through the USA. Traffic from Europe to Algeria and Tunisia is not affected, but traffic from Europe to the Near East and Asia is interrupted to a greater or lesser extent (read more for country). more
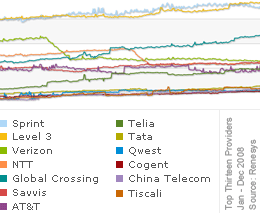 In a post by Earl Zmijewski of Renesys, a number of observations have been made in the effort to rank all Internet service providers in the world for 2008 -- globally, geographically, as well as by market segment. Given the controversial nature of such a ranking in the industry, Zmijewski has pointed out that the changes in rank can be far more revealing than the actual rank itself. For instance it is noted that providers who are moving up in the rankings are doing so due, in large measure, to Asia. "China Telecom poised to enter the top-10 'global' providers, despite not being very global. Guess that is easy to do when you 'own' 1/6 of the world's population," says Zmijewski. Findings also include Sprint losing its long held #1 status to Level 3 and Global Crossing surging to #3, leaving their peers behind. more
In a post by Earl Zmijewski of Renesys, a number of observations have been made in the effort to rank all Internet service providers in the world for 2008 -- globally, geographically, as well as by market segment. Given the controversial nature of such a ranking in the industry, Zmijewski has pointed out that the changes in rank can be far more revealing than the actual rank itself. For instance it is noted that providers who are moving up in the rankings are doing so due, in large measure, to Asia. "China Telecom poised to enter the top-10 'global' providers, despite not being very global. Guess that is easy to do when you 'own' 1/6 of the world's population," says Zmijewski. Findings also include Sprint losing its long held #1 status to Level 3 and Global Crossing surging to #3, leaving their peers behind. more
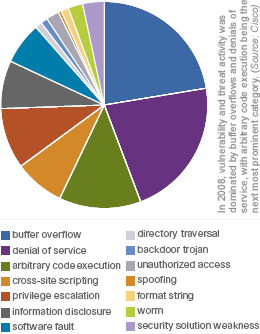 In a 52 page security report released by Cisco, the company has confirmed what has been consistently been observed through out this year: "the Internet-based attacks are becoming increasingly sophisticated and specialized as profit-driven criminals continue to hone their approach to stealing data from businesses, employees and consumers." The 2008 edition of the report has specified the year's top security threats and offers recommendations for protecting networks against attacks that are propagating more rapidly, becoming increasingly difficult to detect, and exploiting technological and human vulnerabilities. more
In a 52 page security report released by Cisco, the company has confirmed what has been consistently been observed through out this year: "the Internet-based attacks are becoming increasingly sophisticated and specialized as profit-driven criminals continue to hone their approach to stealing data from businesses, employees and consumers." The 2008 edition of the report has specified the year's top security threats and offers recommendations for protecting networks against attacks that are propagating more rapidly, becoming increasingly difficult to detect, and exploiting technological and human vulnerabilities. more
 The Pew Internet Project has just released its third report on its "The Future of the Internet" series where it has surveyed experts about the future social, political, and economic impact of the Internet. In this latest web-based survey, 578 leading Internet activists, builders, and commentators and 618 additional stakeholders (1,196 respondents) were asked to assess thought-provoking proposed scenarios for the year 2020, which include the following quantitative results... more
The Pew Internet Project has just released its third report on its "The Future of the Internet" series where it has surveyed experts about the future social, political, and economic impact of the Internet. In this latest web-based survey, 578 leading Internet activists, builders, and commentators and 618 additional stakeholders (1,196 respondents) were asked to assess thought-provoking proposed scenarios for the year 2020, which include the following quantitative results... more
 Eugene Kaspersky, co-founder of Internet security software Kaspersky Lab, was recently interviewed PC World where he talked about his views regarding cybersecurity and the evolution of malware. In response to fixing the problems with malware on the Internet, Kapersky says: "The Internet was never designed with security in mind. If I was God, and wanted to fix the Internet, I would start by ensuring that every user has a sort of Internet passport: basically, a means of verifying identity, just like in the real world, with driver's licenses and passports and so on. The second problem is one of jurisdiction. The Internet has no borders, and neither do the criminals who operate on the Internet. However, law enforcement agencies have jurisdictional limits, and are unable to conduct investigations across the globe. ... There is no such thing as anonymity on the Internet, for the average user." more
Eugene Kaspersky, co-founder of Internet security software Kaspersky Lab, was recently interviewed PC World where he talked about his views regarding cybersecurity and the evolution of malware. In response to fixing the problems with malware on the Internet, Kapersky says: "The Internet was never designed with security in mind. If I was God, and wanted to fix the Internet, I would start by ensuring that every user has a sort of Internet passport: basically, a means of verifying identity, just like in the real world, with driver's licenses and passports and so on. The second problem is one of jurisdiction. The Internet has no borders, and neither do the criminals who operate on the Internet. However, law enforcement agencies have jurisdictional limits, and are unable to conduct investigations across the globe. ... There is no such thing as anonymity on the Internet, for the average user." more
Today via its Online Security Blog, Google announced the release of its Browser Security Handbook aimed at providing web application developers, browser engineers, and information security researchers a "one-stop reference" to critical security attributes of modern web browsers. "Insufficient understanding of these often poorly-documented characteristics is a major contributing factor to the prevalence of several classes of security vulnerabilities," says the introduction to the 60-page document. more
The latest issue of Policy Review from the Hoover Institution, a public policy research center -- focused on advanced study of politics, economics, and political economy -- has an essay titled eWMDs – electronic weapons of mass destruction. The Policiy Review readers are warned that botnets should be considered a serious security problem and that "cyber attacks present a grave new security vulnerability for all nations and must be urgently addressed." more
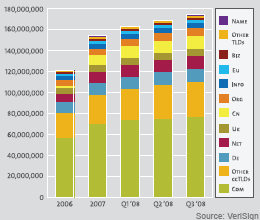 According to recent reports, the total number of new domain name registrations in the third quarter of 2008 reached 11.5 million, pushing the total number of domain names registered in total across all Top-Level Domain Names (TLDs) to 174 million. While the growth continues, the newly released Domain Report by Verisign, indicates a "a decline of new registrations by 2%t from second quarter and 2% from third quarter 2007, driven by declines in both gTLD and ccTLD growth." The decline in new domain name registrations are found to be partly due new changes made by Google to its AdSense program -- the report explains... more
According to recent reports, the total number of new domain name registrations in the third quarter of 2008 reached 11.5 million, pushing the total number of domain names registered in total across all Top-Level Domain Names (TLDs) to 174 million. While the growth continues, the newly released Domain Report by Verisign, indicates a "a decline of new registrations by 2%t from second quarter and 2% from third quarter 2007, driven by declines in both gTLD and ccTLD growth." The decline in new domain name registrations are found to be partly due new changes made by Google to its AdSense program -- the report explains... more
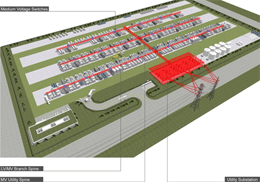 In a blog post today, Microsoft has provided details of its Generation 4 Modular Data Center plan, which the company believes to be the foundation for its cloud data center infrastructure in the next five years. Michael Manos, Microsoft's General Manager of Global Foundation Services, responsible for the global data center design writes: "We believe it is one of the most revolutionary changes to happen to data centers in the last 30 years..." more
In a blog post today, Microsoft has provided details of its Generation 4 Modular Data Center plan, which the company believes to be the foundation for its cloud data center infrastructure in the next five years. Michael Manos, Microsoft's General Manager of Global Foundation Services, responsible for the global data center design writes: "We believe it is one of the most revolutionary changes to happen to data centers in the last 30 years..." more
 Outgoing Federal Communications Commission Chairman Kevin Martin is pushing for action in December on a plan to offer free, pornography-free wireless Internet service to all Americans, despite objections from the wireless industry and some consumer groups. The proposal to allow a no-smut, free wireless Internet service is part of a proposal to auction off a chunk of airwaves. The winning bidder would be required to set aside a quarter of the airwaves for a free Internet service. more
Outgoing Federal Communications Commission Chairman Kevin Martin is pushing for action in December on a plan to offer free, pornography-free wireless Internet service to all Americans, despite objections from the wireless industry and some consumer groups. The proposal to allow a no-smut, free wireless Internet service is part of a proposal to auction off a chunk of airwaves. The winning bidder would be required to set aside a quarter of the airwaves for a free Internet service. more
Sponsored byCSC

Sponsored byVerisign

Sponsored byIPv4.Global

Sponsored byRadix

Sponsored byDNIB.com

Sponsored byVerisign

Sponsored byWhoisXML API
