

Brand Protection |
Sponsored by |

|



 In the early days of Online Brand Protection (OBP), before it was commonly understood how damaging to revenue infringements could be, this was an extremely popular topic. I remember delivering webinars on the subject then and even running a couple of half-day in-person workshops for brand owners at major conferences.
In the early days of Online Brand Protection (OBP), before it was commonly understood how damaging to revenue infringements could be, this was an extremely popular topic. I remember delivering webinars on the subject then and even running a couple of half-day in-person workshops for brand owners at major conferences.
 There is an interesting new trend in fiber construction. Some relatively large cities are getting fiber networks using microtrenching. Just in the last week, I've seen announcements of plans to use microtrenching in cities like Mesa, Arizona, and Sarasota Springs, New York. In the past, the technology was used for new fiber networks in Austin, Texas, San Antonia, Texas, and Charlotte, North Carolina.
There is an interesting new trend in fiber construction. Some relatively large cities are getting fiber networks using microtrenching. Just in the last week, I've seen announcements of plans to use microtrenching in cities like Mesa, Arizona, and Sarasota Springs, New York. In the past, the technology was used for new fiber networks in Austin, Texas, San Antonia, Texas, and Charlotte, North Carolina.
 Over the last two years, we've all faced supply shortages on items we previously never thought could be in short supply. Most recently, the baby formula and semiconductor markets were hit. Before that, supply chain attacks on Colonial Pipeline and JBS Foods showed us that an attack on one company through a singular point of compromise has the potential to disrupt an entire network of connected companies, products, partners, vendors, and customers.
Over the last two years, we've all faced supply shortages on items we previously never thought could be in short supply. Most recently, the baby formula and semiconductor markets were hit. Before that, supply chain attacks on Colonial Pipeline and JBS Foods showed us that an attack on one company through a singular point of compromise has the potential to disrupt an entire network of connected companies, products, partners, vendors, and customers.
 FCC Chairman Jessica Rosenworcel has circulated a draft Notice of Inquiry inside the FCC to kick off the required annual report to Congress on the state of U.S. broadband. As part of preparing that report, she is recommending that the FCC adopt a new definition of broadband of 100/20 Mbps and establish gigabit broadband as a longer-term goal. I have a lot of different reactions to the idea.
FCC Chairman Jessica Rosenworcel has circulated a draft Notice of Inquiry inside the FCC to kick off the required annual report to Congress on the state of U.S. broadband. As part of preparing that report, she is recommending that the FCC adopt a new definition of broadband of 100/20 Mbps and establish gigabit broadband as a longer-term goal. I have a lot of different reactions to the idea.
 I often read marketing material from Online Brand or Content Protection vendors, especially some of the newer ones, that make IP rights enforcement sound very straightforward. In some scenarios, given the correct processes are followed, this can be the case - using eBay's VERO program or similar offerings from the major legitimate platforms, counterfeit listings can be removed very quickly.
I often read marketing material from Online Brand or Content Protection vendors, especially some of the newer ones, that make IP rights enforcement sound very straightforward. In some scenarios, given the correct processes are followed, this can be the case - using eBay's VERO program or similar offerings from the major legitimate platforms, counterfeit listings can be removed very quickly.
 Geotargeting is a well-established online technique for delivering tailored web content based on a user's geographic location. From an internet technology point of view, this is usually based on the user's IP address, which is converted to a physical location through a standard look-up process performed by network infrastructure. Geotargeting is commonly used by websites for several legitimate reasons, including providing users with relevant advertising and other content...
Geotargeting is a well-established online technique for delivering tailored web content based on a user's geographic location. From an internet technology point of view, this is usually based on the user's IP address, which is converted to a physical location through a standard look-up process performed by network infrastructure. Geotargeting is commonly used by websites for several legitimate reasons, including providing users with relevant advertising and other content...
 As a long-established online attack strategy, phishing remains a popular tool for fraudsters because of its effectiveness. The Anti-Phishing Working Group reported more than 300,000 distinct phishing attacks in December 2021 -- more than three times the number reported in early 2020, and the highest monthly total ever identified.
As a long-established online attack strategy, phishing remains a popular tool for fraudsters because of its effectiveness. The Anti-Phishing Working Group reported more than 300,000 distinct phishing attacks in December 2021 -- more than three times the number reported in early 2020, and the highest monthly total ever identified.
 Counterfeiting is big business. A 2021 study by the Organisation for Economic Cooperation and Development (OECD) estimated that the international trade in counterfeit and pirated products was worth up to $464 billion in 2019, or around 2.5% of all world trade. A significant proportion of this trade occurs via digital channels, where global annual expenditure on eCommerce is more than $4 trillion.
Counterfeiting is big business. A 2021 study by the Organisation for Economic Cooperation and Development (OECD) estimated that the international trade in counterfeit and pirated products was worth up to $464 billion in 2019, or around 2.5% of all world trade. A significant proportion of this trade occurs via digital channels, where global annual expenditure on eCommerce is more than $4 trillion.
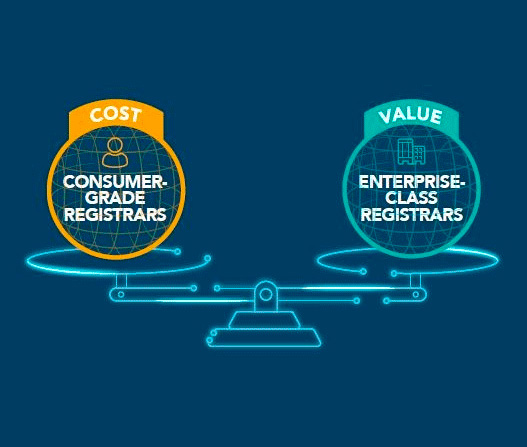
 A web domain name is the foundational piece of internet property allowing its owner (registrant) to construct and host an associated website. On a domain, the owner is also able to construct whatever subdomains they wish -- a process that is technically achieved via the configuration of records on the authoritative domain name system (DNS) server.
A web domain name is the foundational piece of internet property allowing its owner (registrant) to construct and host an associated website. On a domain, the owner is also able to construct whatever subdomains they wish -- a process that is technically achieved via the configuration of records on the authoritative domain name system (DNS) server.
 It's sometimes easy to forget that the broadband business is just over twenty-five years old. The telephone companies had a monopoly on copper-based technologies until Congress passed the Telecommunication Act of 1996, which forced the big telephone companies to allow competition for copper-based broadband services.
It's sometimes easy to forget that the broadband business is just over twenty-five years old. The telephone companies had a monopoly on copper-based technologies until Congress passed the Telecommunication Act of 1996, which forced the big telephone companies to allow competition for copper-based broadband services.