

 During California's devastating 2025 wildfires, Starlink, Tesla, and T-Mobile offered vital emergency connectivity. Their improvised response reveals both the promise of satellite-based disaster aid and the need for formalised coordination with public agencies.
During California's devastating 2025 wildfires, Starlink, Tesla, and T-Mobile offered vital emergency connectivity. Their improvised response reveals both the promise of satellite-based disaster aid and the need for formalised coordination with public agencies.
 DNSSEC promised to secure DNS with cryptographic proof, yet messy rollouts, outages, and hype backlash ruined its reputation. This piece argues that storytelling and emotions shape adoption as much as specs, and that automation enables a reset.
DNSSEC promised to secure DNS with cryptographic proof, yet messy rollouts, outages, and hype backlash ruined its reputation. This piece argues that storytelling and emotions shape adoption as much as specs, and that automation enables a reset.
 ICANN invites proposals for its DNSSEC and Security Workshop at the ICANN85 Community Forum in March 2026, offering a platform for global experts to share insights on DNS, routing security, and emerging threats.
ICANN invites proposals for its DNSSEC and Security Workshop at the ICANN85 Community Forum in March 2026, offering a platform for global experts to share insights on DNS, routing security, and emerging threats.
 Universities sit on vast reserves of IPv4 addresses -- a legacy from the early internet. Instead of one-off sales, leasing these assets could generate sustainable revenues while preserving long-term digital infrastructure and institutional flexibility.
Universities sit on vast reserves of IPv4 addresses -- a legacy from the early internet. Instead of one-off sales, leasing these assets could generate sustainable revenues while preserving long-term digital infrastructure and institutional flexibility.
 AT&T’s CEO plays down the threat of satellite cellular, citing bandwidth and coverage limits. Yet growing interest in rural and IoT applications suggests the technology could still claim valuable niches in the wireless market.
AT&T’s CEO plays down the threat of satellite cellular, citing bandwidth and coverage limits. Yet growing interest in rural and IoT applications suggests the technology could still claim valuable niches in the wireless market.
 Poland thwarted a large-scale cyberattack on its energy grid without disruption, offering a rare case study in critical infrastructure resilience, decentralised energy governance, and the balancing act between openness and digital security.
Poland thwarted a large-scale cyberattack on its energy grid without disruption, offering a rare case study in critical infrastructure resilience, decentralised energy governance, and the balancing act between openness and digital security.
 The draft String Similarity Evaluation Guidelines risk entrenching past failures of Internet governance. With opaque algorithms and no right of appeal, ICANN's credibility hangs on whether transparency and fairness are restored before final adoption.
The draft String Similarity Evaluation Guidelines risk entrenching past failures of Internet governance. With opaque algorithms and no right of appeal, ICANN's credibility hangs on whether transparency and fairness are restored before final adoption.
 A 2026 outlook charts Internet governance between fear and hope, tracking cyber conflict, digital trade and taxation, shrinking rights, and global AI rivalry, while asking whether multistakeholder cooperation can still steer the network toward stability.
A 2026 outlook charts Internet governance between fear and hope, tracking cyber conflict, digital trade and taxation, shrinking rights, and global AI rivalry, while asking whether multistakeholder cooperation can still steer the network toward stability.
 Global digital policy frameworks often overlook the realities of African SMEs, imposing compliance standards shaped by mature economies and infrastructure, thereby constraining innovation, competitiveness, and inclusion in the digital economy.
Global digital policy frameworks often overlook the realities of African SMEs, imposing compliance standards shaped by mature economies and infrastructure, thereby constraining innovation, competitiveness, and inclusion in the digital economy.
 ICANN's 2026 Nominating Committee invites applications for key policy council roles that shape global Internet governance, offering leadership opportunities in domain regulation, digital rights, and multistakeholder decision-making. Deadline: 18 February 2026.
ICANN's 2026 Nominating Committee invites applications for key policy council roles that shape global Internet governance, offering leadership opportunities in domain regulation, digital rights, and multistakeholder decision-making. Deadline: 18 February 2026.
 Iran's deliberate disconnection from the global internet reveals a deeper crisis in digital governance, where state-led suppression and procedural legitimacy now threaten the foundational architecture and human rights principles of an open web.
Iran's deliberate disconnection from the global internet reveals a deeper crisis in digital governance, where state-led suppression and procedural legitimacy now threaten the foundational architecture and human rights principles of an open web.
 Low Earth Orbit satellite networks are dismantling traditional IP address allocation models. As signals defy borders, Regional Internet Registries face challenges in geolocation accuracy, routing security, and the definition of digital territory itself.
Low Earth Orbit satellite networks are dismantling traditional IP address allocation models. As signals defy borders, Regional Internet Registries face challenges in geolocation accuracy, routing security, and the definition of digital territory itself.
 The gTLD race is not just about technical readiness. Governance strategy, institutional stamina, and adversarial foresight will define success in ICANN's 2026 round, where geopolitical resistance, not DNS errors, threatens survival.
The gTLD race is not just about technical readiness. Governance strategy, institutional stamina, and adversarial foresight will define success in ICANN's 2026 round, where geopolitical resistance, not DNS errors, threatens survival.
 Starlink expanded to 42 new countries in 2025, added 2.7 million customers, improved network speeds and latency, and continued satellite launches as it nears its first-phase constellation goal of 12,000 satellites.
Starlink expanded to 42 new countries in 2025, added 2.7 million customers, improved network speeds and latency, and continued satellite launches as it nears its first-phase constellation goal of 12,000 satellites.
 As AI shifts from experimentation to real-world deployment, its unseen foundation - undersea cables - emerges as a strategic frontier. Their resilience may shape not only infrastructure policy but the outcome of US-China AI competition.
As AI shifts from experimentation to real-world deployment, its unseen foundation - undersea cables - emerges as a strategic frontier. Their resilience may shape not only infrastructure policy but the outcome of US-China AI competition.
 ICANN's Nominating Committee is calling for community input to help shape its 2026 leadership selection. Feedback on candidate criteria, job descriptions, and process improvements is due by 21 January 2026.
ICANN's Nominating Committee is calling for community input to help shape its 2026 leadership selection. Feedback on candidate criteria, job descriptions, and process improvements is due by 21 January 2026.
 The Internet Society is accepting nominations for two seats on the 2026 Board of the Public Interest Registry, the non-profit behind .ORG and other domains serving civil society. Deadline: 30 January 2026.
The Internet Society is accepting nominations for two seats on the 2026 Board of the Public Interest Registry, the non-profit behind .ORG and other domains serving civil society. Deadline: 30 January 2026.
 In African Internet governance, procedural authorship is quietly displacing community legitimacy. When conveners, not members, define reform processes, legitimacy becomes retrospective and trust erodes -- not by intention, but through unchecked structural roles.
In African Internet governance, procedural authorship is quietly displacing community legitimacy. When conveners, not members, define reform processes, legitimacy becomes retrospective and trust erodes -- not by intention, but through unchecked structural roles.
 Internet governance is shifting from participatory forums to security-driven mandates. As authority accelerates ahead of legitimacy, technical systems face growing instability and operators absorb the risks of politically motivated control.
Internet governance is shifting from participatory forums to security-driven mandates. As authority accelerates ahead of legitimacy, technical systems face growing instability and operators absorb the risks of politically motivated control.
 Global internet use has surpassed six billion users, yet stark divides persist between regions, genders and urban-rural populations. Meanwhile, download speeds have surged and smartphones now dominate how people access the web worldwide.
Global internet use has surpassed six billion users, yet stark divides persist between regions, genders and urban-rural populations. Meanwhile, download speeds have surged and smartphones now dominate how people access the web worldwide.
Despite the long-anticipated exhaustion of IPv4 addresses, the Internet continues to function through clever workarounds, market transfers, and cautious optimism, while IPv6 adoption remains slow and the future of global connectivity appears uncertain. more
Iran is finalizing a nationwide internet isolation system that would allow authorities to disconnect from the global web, as protests continue and external equipment sources, including Huawei, remain shrouded in secrecy. more
Iran's regime has all but nullified, for the most part, Elon Musk's Starlink satellite network using advanced jamming, legal threats, and raids, turning a promising tool for protestors into a cautionary tale of digital authoritarianism. more
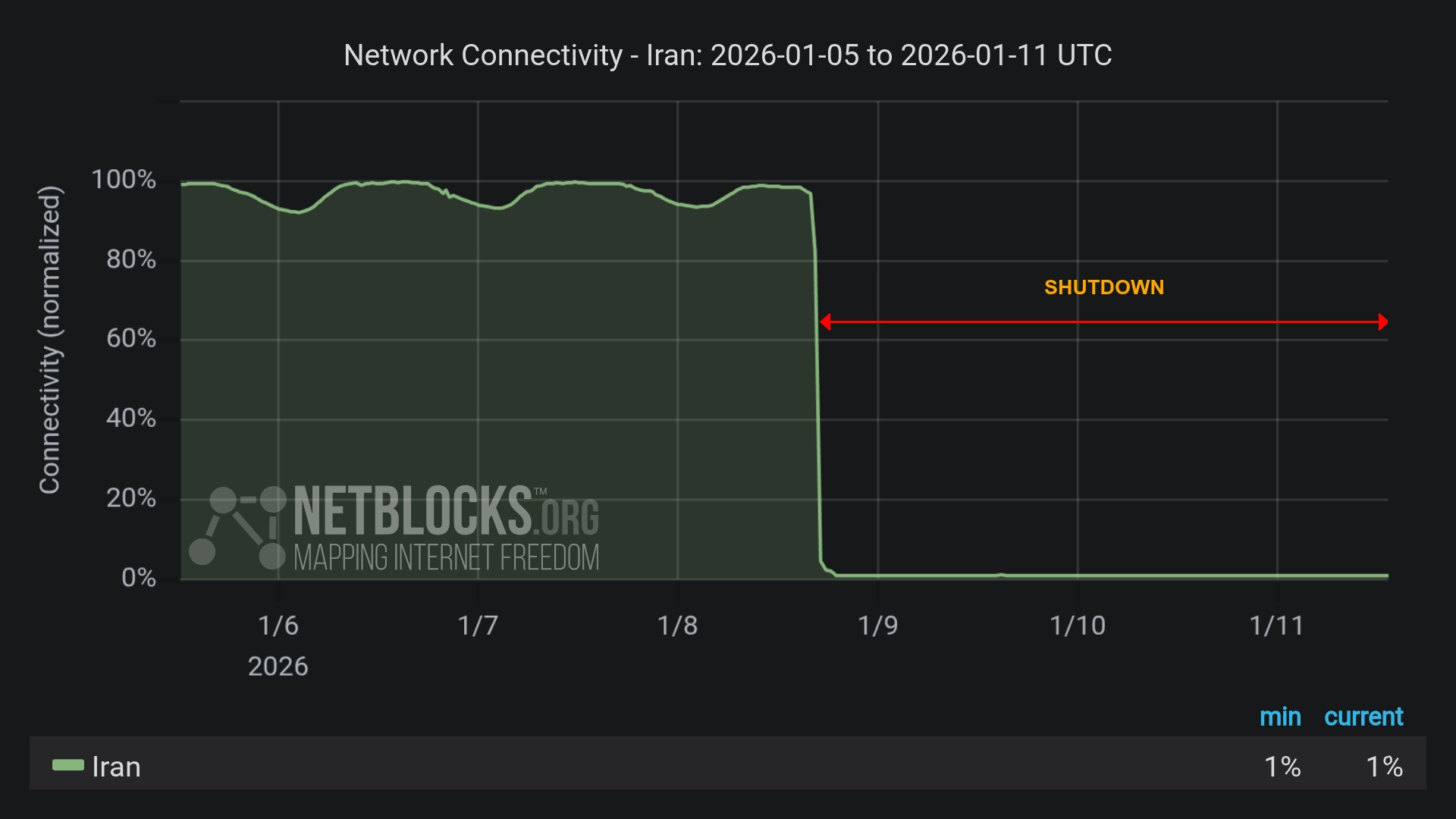 Iran Cuts Off Internet Nationwide as Regime Disrupts Even Starlink Amid Expanding Protests
Iran Cuts Off Internet Nationwide as Regime Disrupts Even Starlink Amid Expanding Protests
Iran has imposed a sweeping internet blackout amid nationwide protests, disrupting even Starlink satellite service. The move marks a new level of digital repression, raising fears of an impending crackdown shielded from global view. more
ICANN will open applications for new top-level domains in April 2026, offering brands a rare chance to secure custom domain names to enhance trust, marketing flexibility, and long-term online security. more
As AI systems take on critical roles in telecommunications, global regulatory frameworks remain outdated and fragmented, leaving essential infrastructure vulnerable to novel risks that current laws on cybersecurity and data protection fail to address. more
The NANOG 95 conference spotlighted breakthroughs in fibre optics, wireless technology, routing security, and quantum computing, offering a forward-looking assessment of internet infrastructure and its vulnerabilities, as reported by APNIC's Geoff Huston. more
AWS is introducing Route 53 Accelerated Recovery to help organizations maintain DNS control during regional outages, offering a 60-minute recovery objective and sustained access to key API operations for critical updates and traffic management. more
 US Senators Move to Shield Undersea Internet Cables from Global Threats
US Senators Move to Shield Undersea Internet Cables from Global Threats
A bipartisan Senate bill seeks to strengthen U.S. oversight and global coordination to protect undersea fiber-optic cables, vital infrastructure increasingly targeted by geopolitical adversaries, natural disasters, and cyber or physical sabotage. more
Global eSIM connections are projected to reach 4.9 billion by 2030, driven by China's rapid adoption, new provisioning standards, and growing demand across smartphones, industrial devices, and the expanding Internet of Things ecosystem. more
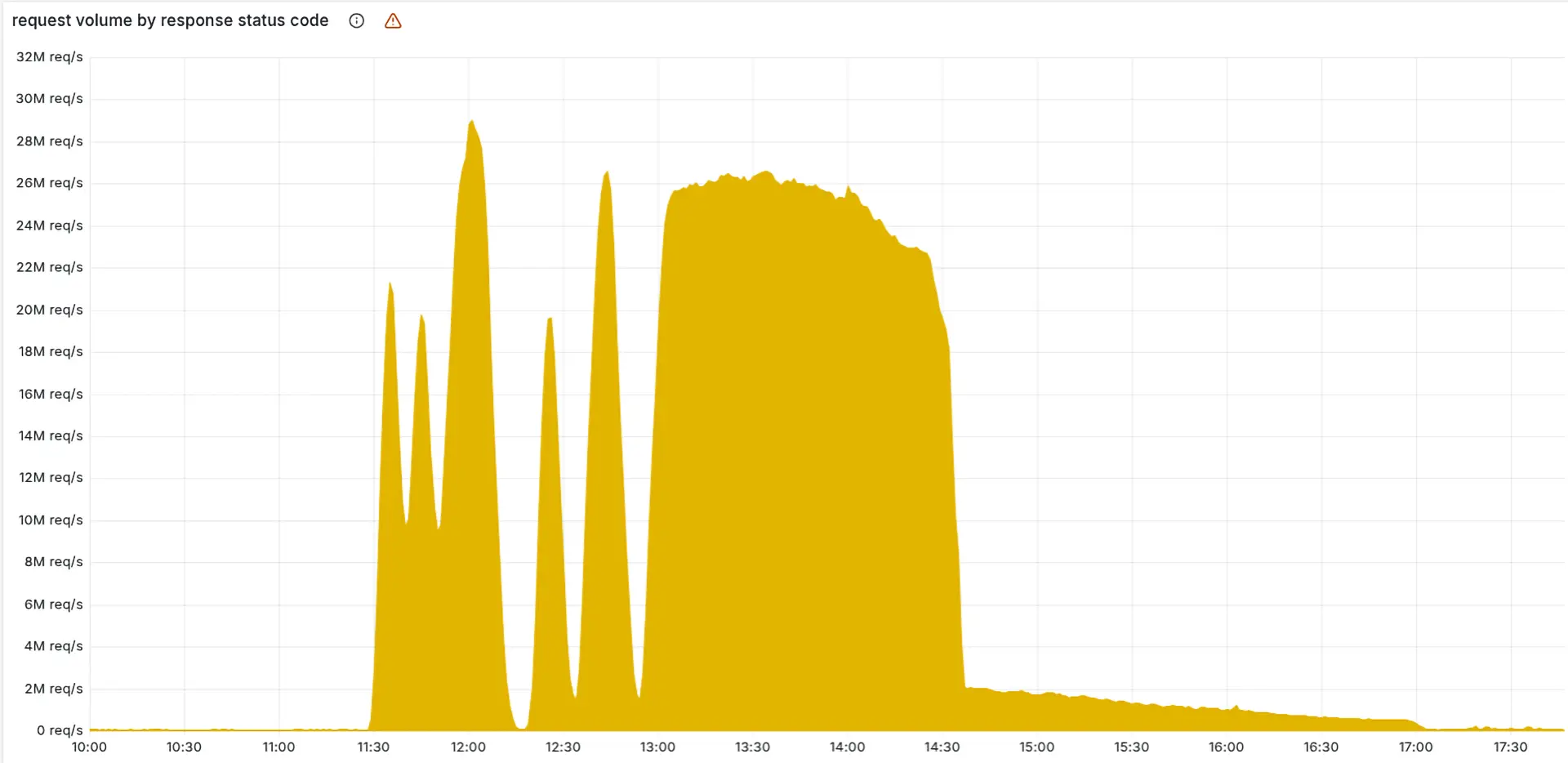 Configuration Chaos: Cloudflare Explains Major Outage in Detailed Post-Mortem
Configuration Chaos: Cloudflare Explains Major Outage in Detailed Post-Mortem
Cloudflare has detailed the cause of a global outage in a post-mortem report, revealing that a flawed internal database change -- not a cyberattack -- caused widespread service disruption across its network and customer systems. more
 Cloudflare Outage Highlights Internet’s Growing Single Points of Failure
Cloudflare Outage Highlights Internet’s Growing Single Points of Failure
Cloudflare's global outage caused cascading failures across the internet, reigniting concerns about the concentration of web infrastructure and the urgent need for more resilient, transparent systems to support critical online services. more
A Chinese-linked cyberattack exploited Anthropic's Claude AI to infiltrate global institutions with limited human input, prompting urgent calls for regulation and sparking debate over the growing autonomy of artificial intelligence in digital threats. more
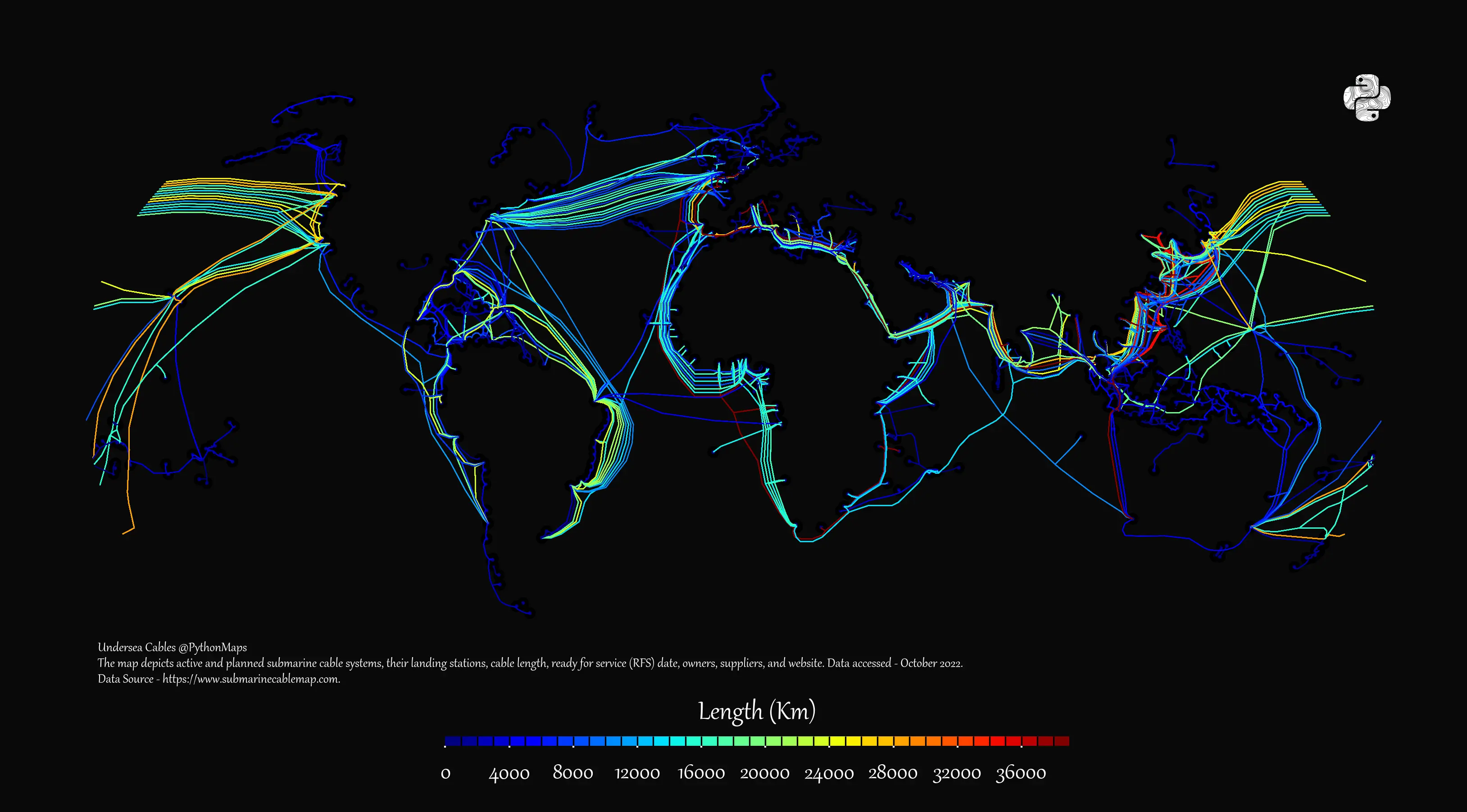 AI Boom Spurs Record Investment in Undersea Cables Amid Geopolitical and Security Concerns
AI Boom Spurs Record Investment in Undersea Cables Amid Geopolitical and Security Concerns
As AI accelerates global data demand, tech giants are investing heavily in subsea cables. These critical networks face rising geopolitical scrutiny and security risks, reshaping the future of digital infrastructure and global connectivity. more
Alice Munyua criticises ICANN's support for a proposed African internet governance overhaul, arguing it undermines multistakeholder principles and sets a dangerous precedent of political interference in global internet infrastructure. more
Google's Threat Intelligence Group reveals that hackers are integrating AI models directly into malware, enabling live code mutation, stealthier operations, and dynamic payload execution while exploiting AI tools through deceptive prompts and underground marketplaces. more
 Verizon and AWS Expand Network Ties to Meet AI Data Demands
Verizon and AWS Expand Network Ties to Meet AI Data Demands
Verizon and AWS have deepened their collaboration to build dedicated fiber infrastructure, addressing the growing need for low-latency, high-capacity connectivity to support the rapid expansion of enterprise-scale artificial intelligence workloads. more
China is revising its cybersecurity laws to include faster reporting requirements and stricter oversight of AI-related incidents, reflecting growing concerns about national security and the unchecked expansion of digital infrastructure. more
A new IETF draft outlines critical limitations of DNS in supporting the Internet of Autonomous Things, highlighting challenges related to latency, mobility, security, and privacy, and proposing architectural improvements to meet evolving machine-driven demands. more
 Starlink Passes 10,000 Satellites, Expanding Global Internet Reach
Starlink Passes 10,000 Satellites, Expanding Global Internet Reach
SpaceX has launched over 10,000 Starlink satellites, solidifying its lead in low-Earth orbit internet infrastructure and accelerating a broader industry shift toward satellite-based broadband in underserved and remote regions worldwide. more
 Massive AWS Outage Disrupts Global Internet, Services Restored After DNS Failure
Massive AWS Outage Disrupts Global Internet, Services Restored After DNS Failure
A major Amazon Web Services outage briefly disrupted millions of websites, apps, and smart devices worldwide. The DNS-related failure exposed the internet's heavy dependence on a few cloud providers before full recovery was achieved. more
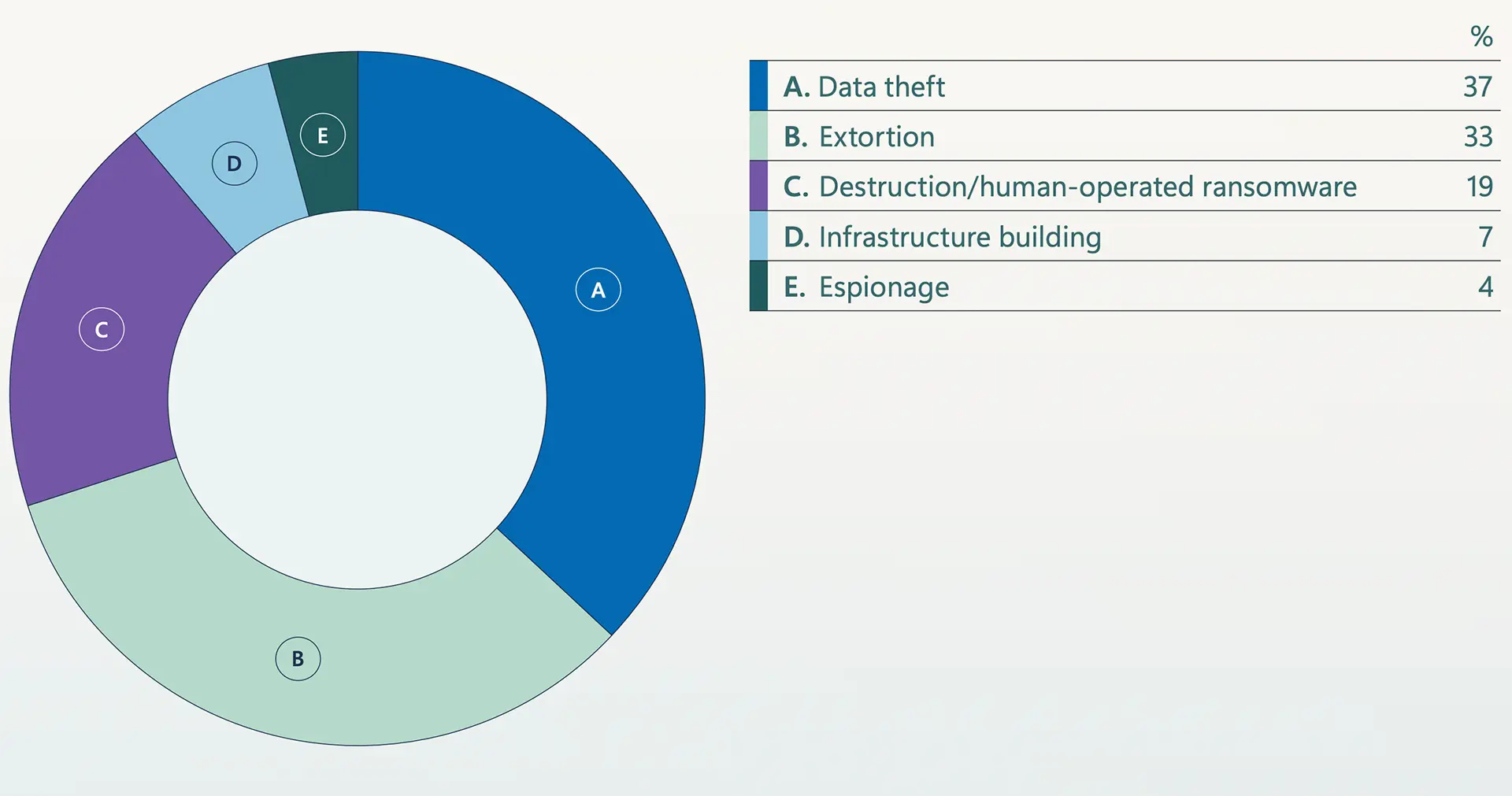 Microsoft Warns Extortion Drives Majority of Attacks Amid AI Escalation, Identity Collapse, and Global Fragmentation
Microsoft Warns Extortion Drives Majority of Attacks Amid AI Escalation, Identity Collapse, and Global Fragmentation
Microsoft's latest Digital Defense Report reveals how cybercriminals and nation-states are rapidly adopting AI to enhance attacks. With identity-based threats soaring, the company urges urgent modernization of security systems and global cooperation. more
Azure researchers propose attested DNS, a system that embeds confidential computing into the internet's naming infrastructure. By binding domain names to trusted hardware and software, it enhances service verification while maintaining compatibility with existing web technologies. more
Cloudflare's new policy challenges Google's AI practices, giving website owners legal tools to control how their content is scraped, used, and monetised by AI systems. more
Senators Hawley and Blumenthal propose a bipartisan bill requiring federal evaluation of advanced AI systems, aiming to prevent misuse while balancing national security, civil liberties, and technological competitiveness. more
Sponsored byVerisign

Sponsored byRadix

Sponsored byWhoisXML API

Sponsored byIPv4.Global

Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byCSC

 Silver Fox, a Chinese state-backed hacking group, disguised its espionage campaign as Russian activity using Cyrillic-laced lures and DNS infrastructure, deploying ValleyRAT to steal intelligence and finance operations through Microsoft Teams abuse. more
Silver Fox, a Chinese state-backed hacking group, disguised its espionage campaign as Russian activity using Cyrillic-laced lures and DNS infrastructure, deploying ValleyRAT to steal intelligence and finance operations through Microsoft Teams abuse. more
 A sophisticated campaign by Ashen Lepus targeted Arabic-speaking government entities using a newly identified malware suite, AshTag. Enhanced encryption, obfuscation techniques, and extensive infrastructure analysis signal a notable evolution in the group's tactics. more
A sophisticated campaign by Ashen Lepus targeted Arabic-speaking government entities using a newly identified malware suite, AshTag. Enhanced encryption, obfuscation techniques, and extensive infrastructure analysis signal a notable evolution in the group's tactics. more
 A seven-year malware campaign, orchestrated through seemingly trusted browser extensions, exposed millions of users to DNS abuse. ShadyPanda's infrastructure reveals how trust, subtlety and DNS manipulation sustained an enduring threat. more
A seven-year malware campaign, orchestrated through seemingly trusted browser extensions, exposed millions of users to DNS abuse. ShadyPanda's infrastructure reveals how trust, subtlety and DNS manipulation sustained an enduring threat. more
 An analysis of domains linked to the top malware strains of Q3 2025 reveals early threat signals, typosquatting patterns, and thousands of connections to malicious infrastructure, underscoring the predictive power of DNS telemetry. more
An analysis of domains linked to the top malware strains of Q3 2025 reveals early threat signals, typosquatting patterns, and thousands of connections to malicious infrastructure, underscoring the predictive power of DNS telemetry. more
 Acronis researchers uncovered a vast malvertising scheme named TamperedChef, which exploited legitimate-looking apps to deploy malicious scripts, steal data, sell remote access, and lay the groundwork for espionage and ransomware campaigns. more
Acronis researchers uncovered a vast malvertising scheme named TamperedChef, which exploited legitimate-looking apps to deploy malicious scripts, steal data, sell remote access, and lay the groundwork for espionage and ransomware campaigns. more
 IPv4 address prices continued their gradual decline in November, with small and medium blocks narrowing the gap with large blocks. Despite falling prices, transaction volume and buyer demand remain strong heading into 2026. more
IPv4 address prices continued their gradual decline in November, with small and medium blocks narrowing the gap with large blocks. Despite falling prices, transaction volume and buyer demand remain strong heading into 2026. more
 MITRE introduced nine new threat groups tied to major vulnerabilities, with deep DNS analysis uncovering 108 malicious domains, 31 risky IPs, and multiple emerging artifacts that highlight evolving attack patterns and early warning opportunities ahead. more
MITRE introduced nine new threat groups tied to major vulnerabilities, with deep DNS analysis uncovering 108 malicious domains, 31 risky IPs, and multiple emerging artifacts that highlight evolving attack patterns and early warning opportunities ahead. more
 A new DNS-based domain validation method promises to streamline certificate automation by reducing DNS write requirements, improving operational security, and aligning with broader industry moves toward scalable, standards-based certificate management. more
A new DNS-based domain validation method promises to streamline certificate automation by reducing DNS write requirements, improving operational security, and aligning with broader industry moves toward scalable, standards-based certificate management. more
 As online attacks grow in complexity and scale, DigiCert's RADAR Brief reveals why resilience across DNS, DDoS, and automation is emerging as the defining metric of digital trust in a hyperconnected economy. more
As online attacks grow in complexity and scale, DigiCert's RADAR Brief reveals why resilience across DNS, DDoS, and automation is emerging as the defining metric of digital trust in a hyperconnected economy. more
 A DNS investigation into GhostCall and GhostHire uncovers how BlueNoroff targeted tech leaders and Web3 developers, exposing extensive data theft and a wide malicious infrastructure that included suspicious domains, weaponized IP addresses, and typosquatted assets. more
A DNS investigation into GhostCall and GhostHire uncovers how BlueNoroff targeted tech leaders and Web3 developers, exposing extensive data theft and a wide malicious infrastructure that included suspicious domains, weaponized IP addresses, and typosquatted assets. more
What is a Dedicated IP VPN? A Dedicated IP VPN is a Virtual Private Network (VPN) service that provides users with a unique, static IP address assigned exclusively to them. Unlike a shared IP address, which is used by multiple users simultaneously, a dedicated IP is reserved for a single user, offering greater control and security over their online activities. more
Starlink provides high-speed, low-latency satellite internet, making it ideal for rural and remote areas lacking traditional broadband. Installation is user-friendly, and coverage continues to expand globally. However, the service is relatively expensive, and performance can be impacted by adverse weather. Overall, Starlink is a reliable choice for those without access to conventional internet options. more
ISPs can see that you are using a VPN, as they can detect encrypted traffic and the IP address of the VPN server. However, they cannot see the content of your data or the websites you visit while the VPN is active because the data is encrypted. This provides privacy for your online activities, though the fact that you're using a VPN itself is visible to the ISP. more
Satellite internet is a broadband service that connects users via signals transmitted between orbiting satellites and a satellite dish at the user's location. Unlike fiber or cable, it doesn't require physical infrastructure, making it essential in rural and remote areas. Although historically slower with higher latency, advancements like Low Earth Orbit (LEO) satellites have improved speed and reduced delays, enhancing overall performance. more
Yes, NordVPN still works with Netflix in 2024. It effectively bypasses geo-restrictions, unlocking libraries from major regions like the U.S., UK, Japan, and more. However, occasional issues like blocked servers or slow connections may arise. Troubleshooting, such as switching servers or using SmartPlay, typically resolves problems and maintains reliable access to Netflix. more
NordVPN offers two ways to try the service risk-free: a 7-day free trial for Android users and a 30-day money-back guarantee for all users. Both options allow full access to NordVPN's premium features. The trial requires payment details but can be canceled before charges occur. NordVPN provides superior security, performance, and global content access compared to free alternatives. more
NordVPN stands out for its unique double encryption, adding an extra layer of privacy. With blazing-fast servers in 60 countries, it's perfect for streaming, gaming, and bypassing geo-blocks. Its strict no-logs policy and advanced features like CyberSec ad-blocker make it a top choice for anyone seeking strong security and seamless performance. more
The best countries for VPN server locations include Switzerland, Iceland, and Panama for privacy, Germany, Japan, and the United States for fast connections, and the U.S., U.K., and Canada for streaming. These countries offer strong privacy laws, advanced infrastructure, and optimal performance for various online activities. more
VPNs are critical for remote work because they secure data by encrypting internet connections, protecting sensitive company information from cyberattacks. They also enable remote access to company networks, ensuring employees can work safely from any location while maintaining privacy and compliance with security policies. more
A VPN protects you by encrypting your internet connection, hiding your IP address, and routing your data through a secure server. This shields your online activities from hackers, trackers, and surveillance, ensuring privacy and security, especially on public Wi-Fi or when accessing sensitive information. more